Exam Details
Exam Code
:156-215.77Exam Name
:Check Point Certified Security AdministratorCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:60 Q&AsLast Updated
:Dec 13, 2024
CheckPoint Checkpoint Certifications 156-215.77 Questions & Answers
-
Question 231:
You cannot use SmartDashboard's User Directory features to connect to the LDAP server. What should you investigate?
1) Verify you have read-only permissions as administrator for the operating system.
2) Verify there are no restrictions blocking SmartDashboard's User Manager from connecting to the LDAP server.
3) Check that the login Distinguished Name configured has root permission (or at least write permission Administrative access) in the LDAP Server's access control configuration.
A. 1, 2, and 3
B. 2 and 3
C. 1 and 2
D. 1 and 3
-
Question 232:
Exhibit:

Chris has lost SIC communication with his Security Gateway and he needs to re-establish SIC. What would be the correct order of steps needed to perform this task?
A. 5, 1, 2, 4
B. 5, 1, 4, 2
C. 3, 1, 4, 2
D. 2, 3, 1, 4
-
Question 233:
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to a set of designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
He has received a new laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop with a static IP (10.0.0.19).
He wants to move around the organization and continue to have access to the HR Web Server. To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources, and installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams access the HR Web Server from any machine and from any location and installs policy.
John plugged in his laptop to the network on a different network segment and was not able to connect to the HR Web server. What is the next BEST troubleshooting step?
A. Investigate this as a network connectivity issue
B. Install the Identity Awareness Agent
C. Set static IP to DHCP
D. After enabling Identity Awareness, reboot the gateway
-
Question 234:
Which of the following commands can be used to remove site-to-site IPsec Security Association (SA)?
A. vpn debug ipsec
B. vpn ipsec
C. fw ipsec tu
D. vpn tu
-
Question 235:
The technical-support department has a requirement to access an intranet server. When configuring a User Authentication rule to achieve this, which of the following should you remember?
A. You can only use the rule for Telnet, FTP, SMTP, and rlogin services.
B. The Security Gateway first checks if there is any rule that does not require authentication for this type of connection before invoking the Authentication Security Server.
C. Once a user is first authenticated, the user will not be prompted for authentication again until logging out.
D. You can limit the authentication attempts in the User Properties' Authentication tab.
-
Question 236:
Which rule is responsible for the installation failure? Exhibit:
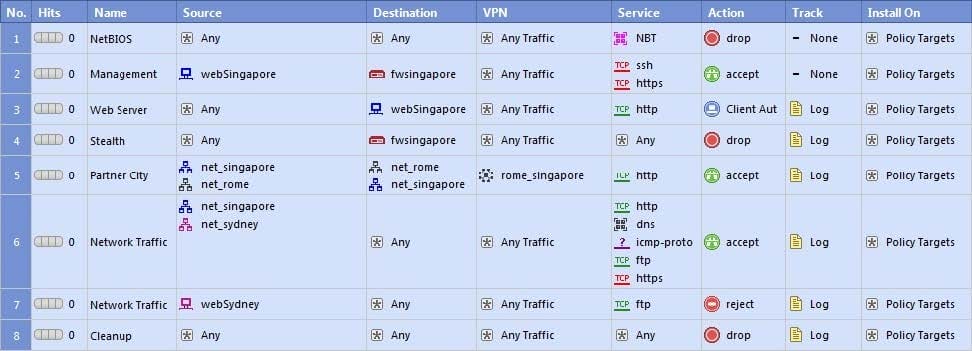
A. Rule 5
B. Rule 4
C. Rule 3
D. Rule 6
-
Question 237:
You have a mesh VPN Community configured to create a site-to-site VPN. Given the displayed VPN properties, what can you conclude about this community?
Exhibit:
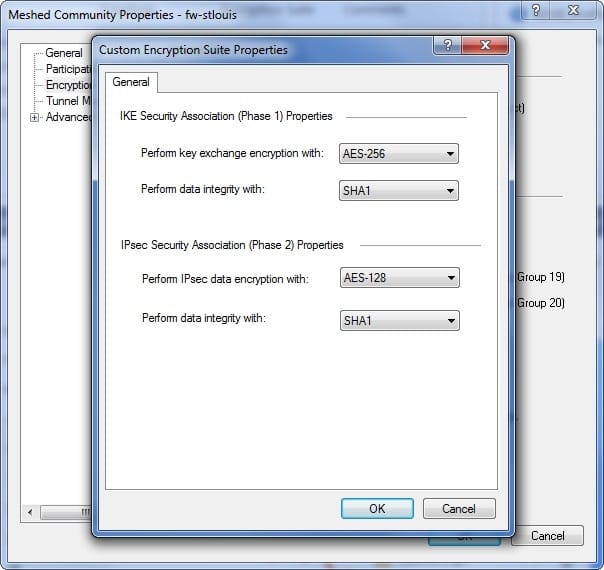
A. The VPN Community will perform IKE Phase 1 key-exchange encryption using the longest key Security Gateway R77 supports.
B. Changing the setting Perform key exchange encryption with from AES-256 to 3DES will enhance the VPN Community's security , and reduce encryption overhead.
C. Change the data-integrity setting for this VPN Community because MD5 is incompatible with AES.
D. Changing the setting Perform IPsec data encryption with from AES-128 to 3Des will increase the encryption overhead.
-
Question 238:
A client has created a new Gateway object that will be managed at a remote location. When the client attempts to install the Security Policy to the new Gateway object, the object does not appear in the Install On check box. What should you look for?
A. Secure Internal Communications (SIC) not configured for the object.
B. A Gateway object created using the Check Point > Externally Managed VPN Gateway option from the Network Objects dialog box.
C. Anti-spoofing not configured on the interfaces on the Gateway object.
D. A Gateway object created using the Check Point > Security Gateway option in the network objects, dialog box, but still needs to configure the interfaces for the Security Gateway object.
-
Question 239:
Users with Identity Awareness Agent installed on their machines login with __________, so that when the user logs into the domain, that information is also used to meet Identity Awareness credential requests.
A. Key-logging
B. ICA Certificates
C. SecureClient
D. Single Sign-On
-
Question 240:
When you use the Global Properties' default settings on R77, which type of traffic will be dropped if NO explicit rule allows the traffic?
A. SmartUpdate connections
B. Outgoing traffic originating from the Security Gateway
C. Firewall logging and ICA key-exchange information
D. RIP traffic
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.