Exam Details
Exam Code
:156-215.77Exam Name
:Check Point Certified Security AdministratorCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:60 Q&AsLast Updated
:Dec 13, 2024
CheckPoint Checkpoint Certifications 156-215.77 Questions & Answers
-
Question 221:
Which of the following is an authentication method used by Identity Awareness?
A. SSL
B. Captive Portal
C. RSA
D. PKI
-
Question 222:
When configuring the Check Point Gateway network interfaces, you can define the direction as Internal or External. What does the option Interface leads to DMZ mean?
Exhibit:
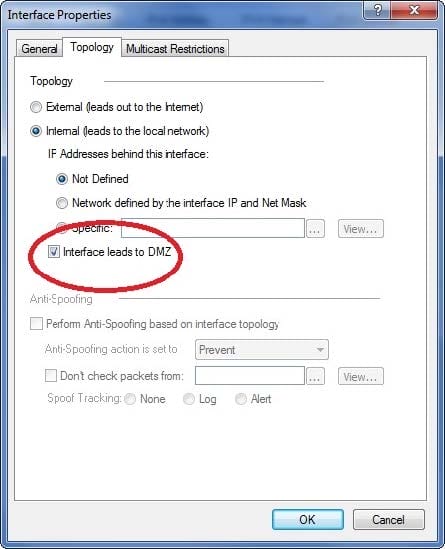
A. Using restricted Gateways, this option automatically turns off the counting of IP Addresses originating from this interface.
B. Activating this option automatically turns this interface to External.
C. It defines the DMZ Interface since this information is necessary for Content Control
D. Select this option to automatically configure Anti-Spoofing to this net.
-
Question 223:
Which of the following methods is NOT used by Identity Awareness to catalog identities?
A. AD Query
B. Captive Portal
C. Identity Agent
D. GPO
-
Question 224:
Which of the following actions do NOT take place in IKE Phase 1?
A. Peers agree on encryption method.
B. Diffie-Hellman key is combined with the key material to produce the symmetrical IPsec key.
C. Peers agree on integrity method.
D. Each side generates a session key from its private key and the peer's public key.
-
Question 225:
Which of the following describes the default behavior of an R77 Security Gateway?
A. Traffic not explicitly permitted is dropped.
B. Traffic is filtered using controlled port scanning.
C. All traffic is expressly permitted via explicit rules.
D. IP protocol types listed as secure are allowed by default, i.e. ICMP, TCP, UDP sessions are inspected.
-
Question 226:
The INSPECT engine inserts itself into the kernel between which two OSI model layers?
A. Session and Transport
B. Physical and Data
C. Presentation and Application
D. Datalink and Network
-
Question 227:
The User Directory Software Blade is used to integrate which of the following with Security Gateway R77?
A. RADIUS server
B. Account Management Client server
C. UserAuthority server
D. LDAP server
-
Question 228:
Charles requests a Website while using a computer not in the net_singapore network. What is TRUE about his location restriction?
Exhibit: A. Source setting in Source column always takes precedence.
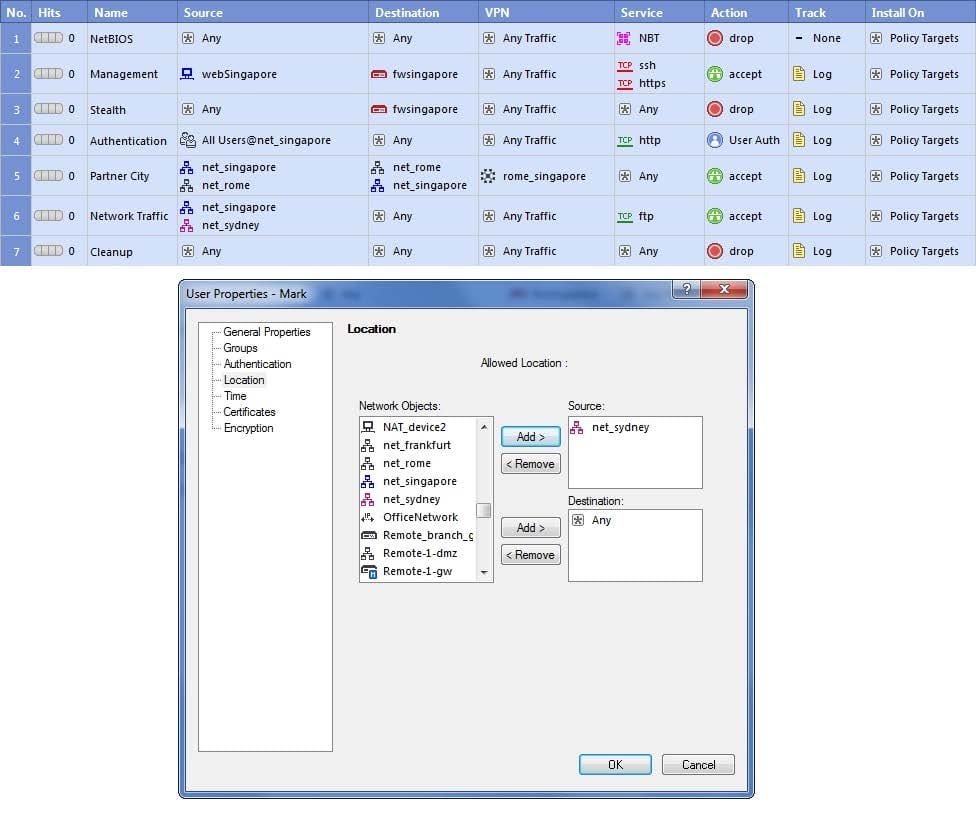
B. Source setting in User Properties always takes precedence.
C. As location restrictions add up, he would be allowed from net_singapore and net_sydney.
D. It depends on how the User Auth object is configured; whether User Properties or Source Restriction takes precedence.
-
Question 229:
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
A. John should install the Identity Awareness Agent
B. The firewall admin should install the Security Policy
C. John should lock and unlock the computer
D. Investigate this as a network connectivity issue
-
Question 230:
You are using SmartView Tracker to troubleshoot NAT entries. Which column do you check to view the NAT'd source port if you are using Source NAT?
A. XlateDst
B. XlateSPort
C. XlateDPort
D. XlateSrc
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.