Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jun 02, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 881:
A company wants to modify its current backup strategy to minimize the number of backups that would need to be restored in case of data loss. Which of the following would be the BEST backup strategy to implement?
A. Incremental backups followed by differential backups
B. Full backups followed by incremental backups
C. Delta backups followed by differential backups
D. Incremental backups followed by delta backups
E. Full backup followed by different backups
-
Question 882:
An analyst Is generating a security report for the management team. Security guidelines recommend disabling all listening unencrypted services. Given this output from Nmap: Which of the following should the analyst recommend to disable?
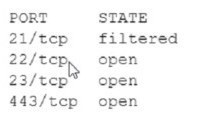
A. 21/tcp
B. 22/tcp
C. 23/tcp
D. 443/tcp
-
Question 883:
An organization would like to remediate the risk associated with its cloud service provider not meeting its advertised 99.999% availability metrics. Which of the following should the organization consult for the exact requirements for the cloud provider?
A. SLA
B. BPA
C. NDA
D. MOU
-
Question 884:
Which of the following should a technician consider when selecting an encryption method for data that needs to remain confidential for a specific length of time?
A. The key length of the encryption algorithm
B. The encryption algorithm's longevity
C. A method of introducing entropy into key calculations
D. The computational overhead of calculating the encryption key
-
Question 885:
The security team received a report of copyright infringement from the IP space of the corporate network. The report provided a precise time stamp for the incident as well as the name of the copyrighted files
The analyst has been tasked with determining the infringing source machine and instructed to implement measures to prevent such incidents from occurring again.
Which of the following is MOST capable of accomplishing both tasks?
A. HIDS
B. Allow list
C. TPM
D. NGFW
-
Question 886:
A help desk technician receives an email from the Chief Information Officer (CIO) asking for documents. The technician knows the CIO is on vacation for a few weeks. Which of the following should the technician do to validate the authenticity of the email?
A. Check the metadata in the email header of the received path in reverse order to follow the email's path.
B. Hover the mouse over the CIO's email address to verify the email address.
C. Look at the metadata in the email header and verify the orF m: line matches the CIO's email address.
D. Forward the email to the CIO and ask if the CIO sent the email requesting the documents.
-
Question 887:
A security engineer is installing a WAF to protect the company's website from malicious web requests over SSL. Which of the following is needed to meet the objective?
A. A reverse proxy
B. A decryption certificate
C. A spill-tunnel VPN
D. Load-balanced servers
-
Question 888:
A company is implementing a new SIEM to log and send alerts whenever malicious activity is blocked by its antivirus and web content filters. Which of the following is the primary use case for this scenario?
A. Implementation of preventive controls
B. Implementation of detective controls
C. Implementation of deterrent controls
D. Implementation of corrective controls
-
Question 889:
As part of a company's ongoing SOC maturation process, the company wants to implement a method to share cyberthreat intelligence data with outside security partners. Which of the following will the company MOST likely implement?
As part of a company's ongoing SOC maturation process, the company wants to implement a method to share cyberthreat intelligence data with outside security partners. Which of the following will the company MOST likely implement?
A. TAXII
B. TLP
C. TTP
D. STIX
-
Question 890:
An organization recently acquired an ISO 27001 certification. Which of the following would MOST likely be considered a benefit of this certification?
A. It allows for the sharing of digital forensics data across organizations
B. It provides insurance in case of a data breach
C. It provides complimentary training and certification resources to IT security staff.
D. It certifies the organization can work with foreign entities that require a security clearance
E. It assures customers that the organization meets security standards
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.