Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 771:
When selecting a technical solution for identity management, an architect chooses to go from an in-house to a third-party SaaS provider. Which of the following risk management strategies is this an example of?
A. Acceptance
B. Mitigation
C. Avoidance
D. Transference
-
Question 772:
Given the following logs:
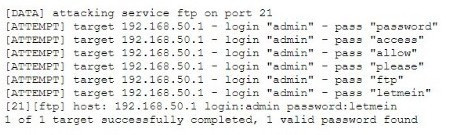
Which of the following BEST describes the type of attack that is occurring?
A. Rainbow table
B. Dictionary
C. Password spraying
D. Pass-the-hash
-
Question 773:
An organization hired a consultant to assist with an active attack, and the consultant was able to identify the compromised accounts and computers. Which of the following is the consultant MOST likely to recommend to prepare for eradication?
A. Quarantining the compromised accounts and computers, only providing them with network access
B. Segmenting the compromised accounts and computers into a honeynet so as to not alert the attackers.
C. Isolating the compromised accounts and computers, cutting off all network and internet access.
D. Logging off and deleting the compromised accounts and computers to eliminate attacker access.
-
Question 774:
An organization discovered a disgruntled employee exfiltrated a large amount of PII data by uploading files.
Which of the following controls should the organization consider to mitigate this risk?
A. EDR
B. Firewall
C. HIPS
D. DLP
-
Question 775:
Which of the following environments typically hosts the current version configurations and code, compares user-story responses and workflow, and uses a modified version of actual data for testing?
A. Development
B. Staging
C. Production
D. Test
-
Question 776:
A security analyst is configuring a large number of new company-issued laptops. The analyst received the following requirements:
1.
The devices will be used internationally by staff who travel extensively.
2.
Occasional personal use is acceptable due to the travel requirements.
3.
Users must be able to install and configure sanctioned programs and productivity suites.
4.
The devices must be encrypted
5.
The devices must be capable of operating in low-bandwidth environments.
Which of the following would provide the GREATEST benefit to the security posture of the devices?
A. Configuring an always-on VPN
B. Implementing application whitelisting
C. Requiring web traffic to pass through the on-premises content filter
D. Setting the antivirus DAT update schedule to weekly
-
Question 777:
A security analyst is reviewing the vulnerability scan report for a web server following an incident. The vulnerability that was used to exploit the server is present in historical vulnerability scan reports, and a patch is available for the vulnerability. Which of the following is the MOST likely cause?
A. Security patches were uninstalled due to user impact.
B. An adversary altered the vulnerability scan reports
C. A zero-day vulnerability was used to exploit the web server
D. The scan reported a false negative for the vulnerability
-
Question 778:
A company completed a vulnerability scan. The scan found malware on several systems that were running older versions of Windows. Which of the following is MOST likely the cause of the malware infection?
A. Open permissions
B. Improper or weak patch management
C. Unsecure root accounts
D. Default settings
-
Question 779:
Audit logs indicate an administrative account that belongs to a security engineer has been locked out multiple times during the day. The security engineer has been on vacation (or a few days). Which of the following attacks can the account lockout be attributed to?
A. Backdoor
B. Brute-force
C. Rootkit
D. Trojan
-
Question 780:
Which ol the following is required in order or an IDS and a WAF to be effective on HTTPS traffic?
A. Hashing
B. DNS sinkhole
C. TLS inspection
D. Data masking
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.