Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 521:
Which of the following organizations sets frameworks and controls for optimal security configuration on systems?
A. ISO
B. GDPR
C. PCI DSS
D. NIST
-
Question 522:
An administrator is experiencing issues when trying to upload a support file to a vendor A pop-up message reveals that a payment card number was found in the file, and the file upload was Mocked. Which of the following controls is most likely causing this issue and should be checked FIRST?
A. DLP
B. Firewall rule
C. Content filter
D. MDM
E. Application allow list
-
Question 523:
A penetration tester was able to compromise an internal server and is now trying to pivot the current session in a network lateral movement Which of the following tools if available on the server, will provide the MOST useful information for the next assessment step?
A. Autopsy
B. Cuckoo
C. Memdump
D. Nmap
-
Question 524:
An organization is building backup server rooms in geographically diverse locations The Chief Information Security Officer implemented a requirement on the project that states the new hardware cannot be susceptible to the same vulnerabilities in the existing server room
Which of the following should the systems engineer consider?
A. Purchasing hardware from different vendors
B. Migrating workloads to public cloud infrastructure
C. Implementing a robust patch management solution
D. Designing new detective security controls
-
Question 525:
A junior security analyst is conducting an analysis after passwords were changed on multiple accounts without users' interaction. The SIEM have multiple login entries with the following text:
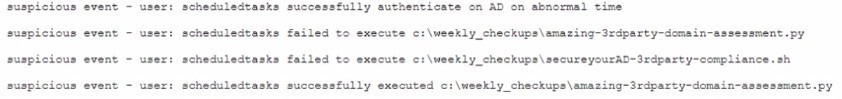
suspicious event - user: scheduledtasks successfully authenticate on AD on abnormal time suspicious event - user: scheduledtasks failed to execute c:\weekly_checkups\amazing-3rdparty-domain-assessment.py suspicious event - user: scheduledtasks failed to execute c:\weekly_checkups\secureyourAD-3rdparty-compliance.sh suspicious event - user: scheduledtasks successfully executed c:\weekly_checkups\amazing-3rdparty-domain-assessment.py
Which of Ihe following is the MOST likely attack conducted on the environment?
A. Malicious script
B. Privilege escalation
C. Doman hijacking
D. DNS poisoning
-
Question 526:
A software company adopted the following processes before releasing software to production;
1.
Peer review
2.
Static code scanning
3.
Signing
A considerable number of vulnerabilities are still being detected when code is executed on production Which of the following security tools can improve vulnerability detection on this environment?
A. File integrity monitoring for the source code
B. Dynamic code analysis tool
C. Encrypted code repository
D. Endpoint detection and response solution
-
Question 527:
A company labeled some documents with the public sensitivity classification This means the documents can be accessed by:
A. employees of other companies and the press
B. all members of the department that created the documents
C. only the company's employees and those listed in the document
D. only the individuate listed in the documents
-
Question 528:
A company wants to improve end users experiences when they tog in to a trusted partner website The company does not want the users to be issued separate credentials for the partner website Which of the following should be implemented to allow users to authenticate using their own credentials to log in to the trusted partner's website?
A. Directory service
B. AAA server
C. Federation
D. Multifactor authentication
-
Question 529:
A DBA reports that several production server hard drives were wiped over the weekend. The DBA also reports that several Linux servers were unavailable due to system files being deleted unexpectedly. A security analyst verified that software was configured to delete data deliberately from those servers. No backdoors to any servers were found.
Which of the following attacks was MOST likely used to cause the data toss?
A. Logic bomb
B. Ransomware
C. Fileless virus
D. Remote access Trojans
E. Rootkit
-
Question 530:
A company wants to restrict emailing of PHI documents. The company is implementing a DLP solution. In order to restrict PHI documents, which of the following should be performed FIRST?
A. Retention
B. Governance
C. Classification
D. Change management
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.