Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 351:
A security analyst needs to be able to search and correlate logs from multiple sources in a single tool
Which of the following would BEST allow a security analyst to have this ability?
A. SOAR
B. SIEM
C. Log collectors
D. Network-attached storage
-
Question 352:
After reluming from a conference, a user's laptop has been operating slower than normal and overheating and the fans have been running constantly Dunng the diagnosis process, an unknown piece of hardware is found connected to the laptop's motherboard
Which of the following attack vectors was exploited to install the hardware?
A. Removable media
B. Spear phishing
C. Supply chain
D. Direct access
-
Question 353:
Several users have opened tickets with the help desk. The help desk has reassigned the tickets to a secunty analyst for further review The security analyst reviews the following metrics:
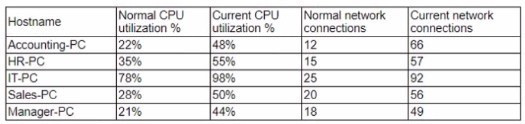
Which of the following is MOST likely the result of the security analyst's review?
A. The ISP is dropping outbound connections
B. The user of the Sales-PC fell for a phishing attack C. Corporate PCs have been turned into a botnet
D. An on-path attack is taking place between PCs and the router
-
Question 354:
A help desk technician receives a phone call from someone claiming to be a part of the organization's cybersecurity modem response team The caller asks the technician to verify the network's internal firewall IP address
Which of the following 15 the technician's BEST course of action?
A. Direct the caller to stop by the help desk in person and hang up declining any further requests from the caller
B. Ask for the callers name, verify the persons identity in the email directory and provide the requested information over the phone
C. Write down the phone number of the carter if possible, the name of the person requesting the information hang up. and notify the organization's cybersecurity officer
D. Request the caller send an email for identity verification and provide the requested information via email to the caller
-
Question 355:
Which of the following documents provides expectations at a technical level for quality, availability, and responsibilities?
A. EOL
B. SLA
C. MOU
D. EOSL
-
Question 356:
The Chief Information Security Officer wants to prevent exfiltration of sensitive information from employee cell phones when using public USB power charging stations. Which of the following would be the BEST solution to Implement?
A. DLP
B. USB data blocker
C. USB OTG
D. Disabling USB ports
-
Question 357:
Several universities are participating m a collaborative research project and need to share compute and storage resources Which of the following cloud deployment strategies would BEST meet this need?
A. Community
B. Private
C. Public
D. Hybrid
-
Question 358:
Digital signatures use asymmetric encryption. This means the message is encrypted with:
A. the sender's private key and decrypted with the sender's public key
B. the sender's public key and decrypted with the sender's private key
C. the sender's private key and decrypted with the recipient's public key.
D. the sender's public key and decrypted with the recipient's private key
-
Question 359:
An application developer accidentally uploaded a company's code-signing certificate private key to a public web server. The company is concerned about malicious use of its certificate. Which of the following should the company do FIRST?
A. Delete the private key from the repository.
B. Verify the public key is not exposed as well.
C. Update the DLP solution to check for private keys.
D. Revoke the code-signing certificate.
-
Question 360:
After multiple on premises security solutions were migrated to the cloud, the incident response time increased. The analyst are spending a long time to trace information on different cloud consoles and correlating data in different formats. Which of the following can be used to optimize the incident response time?
A. CASB
B. VPC
C. SWG
D. CMS
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.