Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Aug 15, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 1001:
A small business office is setting up a wireless infrastructure with primary requirements centered around protecting customer information and preventing unauthorized access to the business network.
Which of the following would BEST support the office's business needs? (Select TWO)
A. Installing WAPs with strategic placement
B. Configuring access using WPAs
C. Installing a WIDS
D. Enabling MAC filtering
E. Changing the WiFi password every 30 days
F. Reducing WiFi transmit power throughout the office
-
Question 1002:
During a forensic investigation, a security analyst discovered that the following command was run on a compromised host:

Which of the following attacks occurred?
A. Buffer overflow
B. Pass the hash
C. SQL injection
D. Replay attack
-
Question 1003:
A security administrator is trying to determine whether a server is vulnerable to a range of attacks. After using a tool, the administrator obtains the following output:
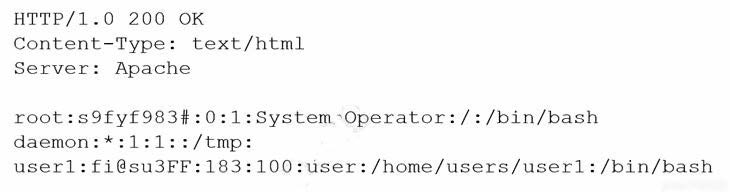
Which of the following attacks was successfully implemented based on the output?
A. Memory leak
B. Race conditions
C. SQL injection
D. Directory traversal
-
Question 1004:
Which of the following controls would provide the BEST protection against tailgating?
A. Access control vestibule
B. Closed-circuit television
C. Proximity card reader
D. Faraday cage
-
Question 1005:
An employee's company account was used in a data breach Interviews with the employee revealed:
The employee was able to avoid changing passwords by using a previous password again. The account was accessed from a hostile, foreign nation, but the employee has never traveled to any other countries.
Which of the following can be implemented to prevent these issues from reoccuring? (Select TWO)
A. Geographic dispersal
B. Password complexity
C. Password history
D. Geotagging
E. Password lockout
F. Geofencing
-
Question 1006:
Which of the following roles would MOST likely have direct access to the senior management team?
A. Data custodian
B. Data owner
C. Data protection officer
D. Data controller
-
Question 1007:
As part of annual audit requirements, the security team performed a review of exceptions to the company policy that allows specific users the ability to use USB storage devices on their laptops. The review yielded the following results. The exception process and policy have been correctly followed by the majority of users A small number of users did not create tickets for the requests but were granted access All access had been approved by supervisors. Valid requests for the access sporadically occurred across multiple departments. Access, in most cases, had not been removed when it was no longer needed
Which of the following should the company do to ensure that appropriate access is not disrupted but unneeded access is removed in a reasonable time frame?
A. Create an automated, monthly attestation process that removes access if an employee's supervisor denies the approval
B. Remove access for all employees and only allow new access to be granted if the employee's supervisor approves the request
C. Perform a quarterly audit of all user accounts that have been granted access and verify the exceptions with the management team
D. Implement a ticketing system that tracks each request and generates reports listing which employees actively use USB storage devices
-
Question 1008:
Which of the following is a physical security control that ensures onty the authorized user is present when gaining access to a secured area?
A. A biometric scanner
B. A smart card reader
C. APKItoken
D. A PIN pad
-
Question 1009:
Which of the following should customers who are involved with Ul developer agreements be concerned with when considering the use of these products on highly sensitive projects?
A. Weak configurations
B. Integration activities
C. Unsecure user accounts
D. Outsourced code development
-
Question 1010:
A security administrator is working on a solution to protect passwords stored in a database against rainbow table attacks. Which of the following should the administrator consider?
A. Hashing
B. Salting
C. Lightweight cryptography
D. Steganography
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.