Exam Details
Exam Code
:RC0-501Exam Name
:CompTIA Security+ Recertification ExamCertification
:CompTIA Security+Vendor
:CompTIATotal Questions
:349 Q&AsLast Updated
:Jun 06, 2025
CompTIA CompTIA Security+ RC0-501 Questions & Answers
-
Question 41:
A company wants to host a publicity available server that performs the following functions:
Evaluates MX record lookup
Can perform authenticated requests for A and AAA records Uses RRSIG
Which of the following should the company use to fulfill the above requirements?
A. LDAPS
B. DNSSEC
C. SFTP
D. nslookup
E. dig
-
Question 42:
A system administrator wants to provide balance between the security of a wireless network and usability. The administrator is concerned with wireless encryption compatibility of older devices used by some employees. Which of the following would provide strong security and backward compatibility when accessing the wireless network?
A. Open wireless network and SSL VPN
B. WPA using a preshared key
C. WPA2 using a RADIUS back-end for 802.1x authentication
D. WEP with a 40-bit key
-
Question 43:
A company has three divisions, each with its own networks and services. The company decides to make its secure web portal accessible to all employees utilizing their existing usernames and passwords. The security administrator has elected to use SAML to support authentication. In this scenario, which of the following will occur when users try to authenticate to the portal? (Select two.)
A. The portal will function as a service provider and request an authentication assertion.
B. The portal will function as an identity provider and issue an authentication assertion.
C. The portal will request an authentication ticket from each network that is transitively trusted.
D. The back-end networks will function as an identity provider and issue an authentication assertion.
E. The back-end networks will request authentication tickets from the portal, which will act as the third-party service provider authentication store.
F. The back-end networks will verify the assertion token issued by the portal functioning as the identity provider.
-
Question 44:
When systems, hardware, or software are not supported by the original vendor, it is a vulnerability known as:
A. system sprawl
B. end-of-life systems
C. resource exhaustion
D. a default configuration
-
Question 45:
An analyst wants to implement a more secure wireless authentication for office access points. Which of the following technologies allows for encrypted authentication of wireless clients over TLS?
A. PEAP
B. EAP
C. WPA2
D. RADIUS
-
Question 46:
After a user reports stow computer performance, a systems administrator detects a suspicious file, which was installed as part of a freeware software package.
The systems administrator reviews the output below:
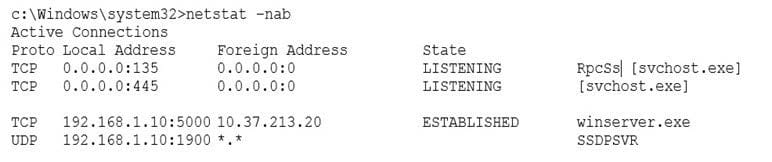
Based on the above information, which of the following types of malware was installed on the user's computer?
A. RAT
B. Keylogger
C. Spyware
D. Worm
E. Bot
-
Question 47:
Which of the following network vulnerability scan indicators BEST validates a successful, active scan?
A. The scan job is scheduled to run during off-peak hours.
B. The scan output lists SQL injection attack vectors.
C. The scan data identifies the use of privileged-user credentials.
D. The scan results identify the hostname and IP address.
-
Question 48:
A senior incident response manager receives a call about some external IPs communicating with internal computers during off hours. Which of the following types of malware is MOST likely causing this issue?
A. Botnet
B. Ransomware
C. Polymorphic malware
D. Armored virus
-
Question 49:
Which of the following technologies employ the use of SAML? (Select two.)
A. Single sign-on
B. Federation
C. LDAP
D. Secure token
E. RADIUS
-
Question 50:
Which of the following specifically describes the explogtation of an interactive process to access otherwise restricted areas of the OS?
A. Privilege escalation
B. Pivoting
C. Process affinity
D. Buffer overflow
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your RC0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.