Exam Details
Exam Code
:RC0-501Exam Name
:CompTIA Security+ Recertification ExamCertification
:CompTIA Security+Vendor
:CompTIATotal Questions
:349 Q&AsLast Updated
:Jun 14, 2025
CompTIA CompTIA Security+ RC0-501 Questions & Answers
-
Question 231:
A development team has adopted a new approach to projects in which feedback is iterative and multiple iterations of deployments are provided within an application's full life cycle. Which of the following software development methodologies is the development team using?
A. Waterfall
B. Agile
C. Rapid
D. Extreme
-
Question 232:
A black hat hacker is enumerating a network and wants to remain convert during the process. The hacker initiates a vulnerability scan. Given the task at hand the requirement of being convert, which of the following statements BEST indicates that the vulnerability scan meets these requirements?
A. The vulnerability scanner is performing an authenticated scan.
B. The vulnerability scanner is performing local file integrity checks.
C. The vulnerability scanner is performing in network sniffer mode.
D. The vulnerability scanner is performing banner grabbing.
-
Question 233:
Which of the following vulnerability types would the type of hacker known as a script kiddie be MOST dangerous against?
A. Passwords written on the bottom of a keyboard
B. Unpatched exploitable Internet-facing services
C. Unencrypted backup tapes
D. Misplaced hardware token
-
Question 234:
An in-house penetration tester is using a packet capture device to listen in on network communications. This is an example of: A. Passive reconnaissance
B. Persistence
C. Escalation of privileges
D. Explogting the switch
-
Question 235:
A security engineer is configuring a wireless network that must support mutual authentication of the wireless client and the authentication server before users provide credentials. The wireless network must also support authentication with usernames and passwords. Which of the following authentication protocols MUST the security engineer select?
A. EAP-FAST
B. EAP-TLS
C. PEAP
D. EAP
-
Question 236:
A system's administrator has finished configuring firewall ACL to allow access to a new web server.
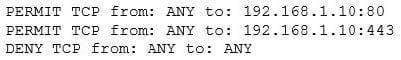
The security administrator confirms form the following packet capture that there is network traffic from the internet to the web server:
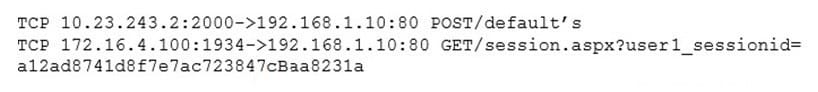
The company's internal auditor issues a security finding and requests that immediate action be taken. With which of the following is the auditor MOST concerned?
A. Misconfigured firewall
B. Clear text credentials
C. Implicit deny
D. Default configuration
-
Question 237:
A security analyst is performing a quantitative risk analysis. The risk analysis should show the potential monetary loss each time a threat or event occurs. Given this requirement, which of the following concepts would assist the analyst in determining this value? (Select two.)
A. ALE
B. AV
C. ARO
D. EF
E. ROI
-
Question 238:
Which of the following AES modes of operation provide authentication? (Select two.)
A. CCM
B. CBC
C. GCM
D. DSA
E. CFB
-
Question 239:
An audit takes place after company-wide restricting, in which several employees changed roles. The following deficiencies are found during the audit regarding access to confidential data:
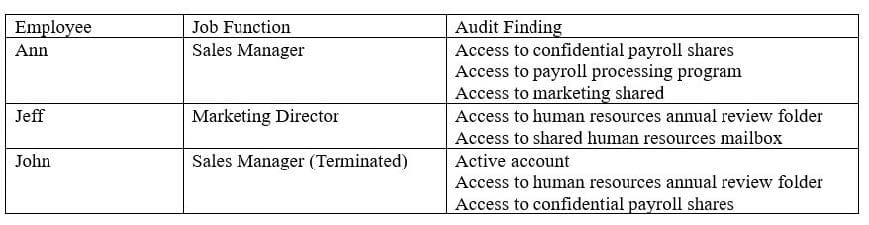
Which of the following would be the BEST method to prevent similar audit findings in the future?
A. Implement separation of duties for the payroll department.
B. Implement a DLP solution on the payroll and human resources servers.
C. Implement rule-based access controls on the human resources server.
D. Implement regular permission auditing and reviews.
-
Question 240:
An audit has revealed that database administrators are also responsible for auditing database changes and backup logs. Which of the following access control methodologies would BEST mitigate this concern?
A. Time of day restrictions
B. Principle of least privilege
C. Role-based access control
D. Separation of duties
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your RC0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.