Exam Details
Exam Code
:PSE-STRATAExam Name
:Palo Alto Networks System Engineer Professional - StrataCertification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:139 Q&AsLast Updated
:Aug 12, 2025
Palo Alto Networks Palo Alto Networks Certifications PSE-STRATA Questions & Answers
-
Question 21:
What action would address the sub-optimal traffic path shown in the figure?
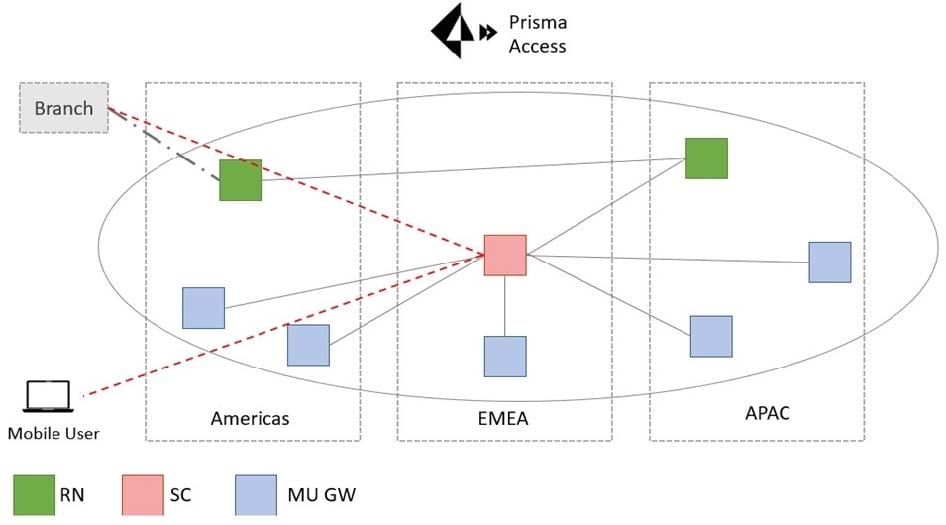
Key: RN -Remote Network SC -Service Connection MU GW -Mobile User Gateway
A. Onboard a Service Connection in the Americas region
B. Remove the Service Connection in the EMEA region
C. Onboard a Service Connection in the APAC region
D. Onboard a Remote Network location in the EMEA region
-
Question 22:
When having a customer pre-sales call, which aspects of the NGFW should be covered?
A. The NGFW simplifies your operations through analytics and automation while giving you consistent protection through exceptional visibility and control across the data center, perimeter, branch, mobile and cloud networks
B. The Palo Alto Networks-developed URL filtering database, PAN-DB provides high-performance local caching for maximum inline performance on URL lookups, and offers coverage against malicious URLs and IP addresses. As WildFire identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs), the PAN-DB database is updated with information on malicious URLs so that you can block malware downloads and disable Command and Control (C2) communications to protect your network from cyberthreats. URL categories that identify confirmed malicious content --malware, phishing, and C2 are updated every five minutes --to ensure that you can manage access to these sites within minutes of categorization
C. The NGFW creates tunnels that allow users/systems to connect securely over a public network, as if they were connecting over a local area network (LAN). To set up a VPN tunnel you need a pair of devices that can authenticate each other and encrypt the flow of information between them The devices can be a pair of Palo Alto Networks firewalls, or a Palo Alto Networks firewall along with a VPN-capable device from another vendor
D. Palo Alto Networks URL Filtering allows you to monitor and control the sites users can access, to prevent phishing attacks by controlling the sites to which users can submit valid corporate credentials, and to enforce safe search for search engines like Google and Bing
-
Question 23:
A customer is designing a private data center to host their new web application along with a separate headquarters for users.
Which cloud-delivered security service (CDSS) would be recommended for the headquarters only?
A. Threat Prevention
B. DNS Security
C. WildFire
D. Advanced URL Filtering (AURLF)
-
Question 24:
Access to a business site is blocked by URL Filtering inline machine learning (ML) and considered as a false-positive.
How should the site be made available?
A. Disable URL Filtering inline ML
B. Create a custom URL category and add it to the Security policy
C. Create a custom URL category and add it on exception of the inline ML profile
D. Change the action of real-time detection category on URL filtering profile
-
Question 25:
Which three features are used to prevent abuse of stolen credentials? (Choose three.)
A. multi-factor authentication
B. URL Filtering Profiles
C. WildFire Profiles
D. Prisma Access
E. SSL decryption rules
-
Question 26:
Which two methods are used to check for Corporate Credential Submissions? (Choose two.)
A. doman credentialiter
B. User-ID credential check
C. LDAP query
D. IP user mapping
-
Question 27:
Which two types of security chains are supported by the Decryption Broker? (Choose two.)
A. virtual wire
B. transparent bridge
C. Layer 3
D. Layer 2
-
Question 28:
What will best enhance security of a production online system while minimizing the impact for the existing network?
A. Layer 2 interfaces
B. active / active high availability (HA)
C. Virtual wire
D. virtual systems
-
Question 29:
What are two core values of the Palo Alto Network Security Operating Platform? (Choose two.}
A. prevention of cyber attacks
B. safe enablement of all applications
C. threat remediation
D. defense against threats with static security solution
-
Question 30:
Within the Five-Step Methodology of Zero Trust, in which step would application access and user access be defined?
A. Step 3: Architect a Zero Trust Network
B. Step 5. Monitor and Maintain the Network
C. Step 4: Create the Zero Trust Policy
D. Step 1: Define the Protect Surface
E. Step 2 Map the Protect Surface Transaction Flows
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PSE-STRATA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.