Exam Details
Exam Code
:PROFESSIONAL-CLOUD-DEVELOPERExam Name
:Professional Cloud DeveloperCertification
:Google CertificationsVendor
:GoogleTotal Questions
:254 Q&AsLast Updated
:Jun 28, 2025
Google Google Certifications PROFESSIONAL-CLOUD-DEVELOPER Questions & Answers
-
Question 221:
HipLocal has connected their Hadoop infrastructure to GCP using Cloud Interconnect in order to query data stored on persistent disks. Which IP strategy should they use?
A. Create manual subnets.
B. Create an auto mode subnet.
C. Create multiple peered VPCs.
D. Provision a single instance for NAT.
-
Question 222:
For this question, refer to the HipLocal case study.
How should HipLocal redesign their architecture to ensure that the application scales to support a large increase in users?
A. Use Google Kubernetes Engine (GKE) to run the application as a microservice. Run the MySQL database on a dedicated GKE node.
B. Use multiple Compute Engine instances to run MySQL to store state information. Use a Google Cloud-managed load balancer to distribute the load between instances. Use managed instance groups for scaling.
C. Use Memorystore to store session information and CloudSQL to store state information. Use a Google Cloud-managed load balancer to distribute the load between instances. Use managed instance groups for scaling.
D. Use a Cloud Storage bucket to serve the application as a static website, and use another Cloud Storage bucket to store user state information.
-
Question 223:
HipLocal's.net-based auth service fails under intermittent load. What should they do?
A. Use App Engine for autoscaling.
B. Use Cloud Functions for autoscaling.
C. Use a Compute Engine cluster for the service.
D. Use a dedicated Compute Engine virtual machine instance for the service.
-
Question 224:
HipLocal's data science team wants to analyze user reviews. How should they prepare the data?
A. Use the Cloud Data Loss Prevention API for redaction of the review dataset.
B. Use the Cloud Data Loss Prevention API for de-identification of the review dataset.
C. Use the Cloud Natural Language Processing API for redaction of the review dataset.
D. Use the Cloud Natural Language Processing API for de-identification of the review dataset.
-
Question 225:
Your team is responsible for maintaining an application that aggregates news articles from many different sources. Your monitoring dashboard contains publicly accessible real-time reports and runs on a Compute Engine instance as a web application. External stakeholders and analysts need to access these reports via a secure channel without authentication. How should you configure this secure channel?
A. Add a public IP address to the instance. Use the service account key of the instance to encrypt the traffic.
B. Use Cloud Scheduler to trigger Cloud Build every hour to create an export from the reports. Store the reports in a public Cloud Storage bucket.
C. Add an HTTP(S) load balancer in front of the monitoring dashboard. Configure Identity- Aware Proxy to secure the communication channel.
D. Add an HTTP(S) load balancer in front of the monitoring dashboard. Set up a Google- managed SSL certificate on the load balancer for traffic encryption.
-
Question 226:
You are a developer working on an internal application for payroll processing. You are building a component of the application that allows an employee to submit a timesheet, which then initiates several steps:
?An email is sent to the employee and manager, notifying them that the timesheet was submitted.
?A timesheet is sent to payroll processing for the vendor's API.
?A timesheet is sent to the data warehouse for headcount planning.
These steps are not dependent on each other and can be completed in any order. New steps are being considered and will be implemented by different development teams. Each development team will implement the error handling specific
to their step. What should you do?
A. Deploy a Cloud Function for each step that calls the corresponding downstream system to complete the required action.
B. Create a Pub/Sub topic for each step. Create a subscription for each downstream development team to subscribe to their step's topic.
C. Create a Pub/Sub topic for timesheet submissions. Create a subscription for each downstream development team to subscribe to the topic.
D. Create a timesheet microservice deployed to Google Kubernetes Engine. The microservice calls each downstream step and waits for a successful response before calling the next step.
-
Question 227:
You are designing a schema for a Cloud Spanner customer database. You want to store a phone number array field in a customer table. You also want to allow users to search customers by phone number. How should you design this schema?
A. Create a table named Customers. Add an Array field in a table that will hold phone numbers for the customer.
B. Create a table named Customers. Create a table named Phones. Add a CustomerId field in the Phones table to find the CustomerId from a phone number.
C. Create a table named Customers. Add an Array field in a table that will hold phone numbers for the customer. Create a secondary index on the Array field.
D. Create a table named Customers as a parent table. Create a table named Phones, and interleave this table into the Customer table. Create an index on the phone number field in the Phones table.
-
Question 228:
You are working on a social media application. You plan to add a feature that allows users to upload images. These images will be 2 MB ?1 GB in size. You want to minimize their infrastructure operations overhead for this feature. What should you do?
A. Change the application to accept images directly and store them in the database that stores other user information.
B. Change the application to create signed URLs for Cloud Storage. Transfer these signed URLs to the client application to upload images to Cloud Storage.
C. Set up a web server on GCP to accept user images and create a file store to keep uploaded files. Change the application to retrieve images from the file store.
D. Create a separate bucket for each user in Cloud Storage. Assign a separate service account to allow write access on each bucket. Transfer service account credentials to the client application based on user information. The application
uses this service account to upload images to Cloud Storage.
-
Question 229:
You have an application written in Python running in production on Cloud Run. Your application needs to read/write data stored in a Cloud Storage bucket in the same project. You want to grant access to your application following the principle of least privilege. What should you do?
A. Create a user-managed service account with a custom Identity and Access Management (IAM) role.
B. Create a user-managed service account with the Storage Admin Identity and Access Management (IAM) role.
C. Create a user-managed service account with the Project Editor Identity and Access Management (IAM) role.
D. Use the default service account linked to the Cloud Run revision in production.
-
Question 230:
You have an application running in App Engine. Your application is instrumented with Stackdriver Trace. The /product-details request reports details about four known unique products at /sku-details as shown below. You want to reduce the time it takes for the request to complete. What should you do?
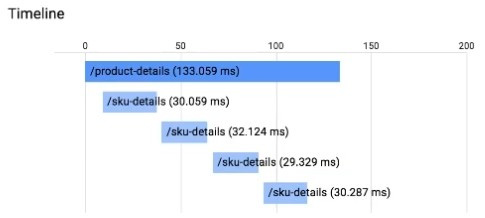
A. Increase the size of the instance class.
B. Change the Persistent Disk type to SSD.
C. Change /product-details to perform the requests in parallel.
D. Store the /sku-details information in a database, and replace the webservice call with a database query.
Related Exams:
ADWORDS-DISPLAY
Google AdWords: Display AdvertisingADWORDS-FUNDAMENTALS
Google AdWords: FundamentalsADWORDS-MOBILE
Google AdWords: Mobile AdvertisingADWORDS-REPORTING
Google AdWords: ReportingADWORDS-SEARCH
Google AdWords: Search AdvertisingADWORDS-SHOPPING
Google AdWords: Shopping AdvertisingADWORDS-VIDEO
Google AdWords: Video AdvertisingAPIGEE-API-ENGINEER
Apigee Certified API EngineerASSOCIATE-ANDROID-DEVELOPER
Associate Android Developer (Kotlin and Java)ASSOCIATE-CLOUD-ENGINEER
Associate Cloud Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Google exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PROFESSIONAL-CLOUD-DEVELOPER exam preparations and Google certification application, do not hesitate to visit our Vcedump.com to find your solutions here.