Exam Details
Exam Code
:PROFESSIONAL-CLOUD-DEVELOPERExam Name
:Professional Cloud DeveloperCertification
:Google CertificationsVendor
:GoogleTotal Questions
:254 Q&AsLast Updated
:Jul 06, 2025
Google Google Certifications PROFESSIONAL-CLOUD-DEVELOPER Questions & Answers
-
Question 141:
You are developing an application that will handle requests from end users. You need to secure a Cloud Function called by the application to allow authorized end users to authenticate to the function via the application while restricting access to unauthorized users. You will integrate Google Sign-In as part of the solution and want to follow Google- recommended best practices. What should you do?
A. Deploy from a source code repository and grant users the roles/cloudfunctions.viewer role.
B. Deploy from a source code repository and grant users the roles/cloudfunctions.invoker role
C. Deploy from your local machine using gcloud and grant users the roles/cloudfunctions.admin role
D. Deploy from your local machine using gcloud and grant users the roles/cloudfunctions.developer role
-
Question 142:
This architectural diagram depicts a system that streams data from thousands of devices. You want to ingest data into a pipeline, store the data, and analyze the data using SQL statements. Which Google Cloud services should you use for steps 1, 2, 3, and 4?
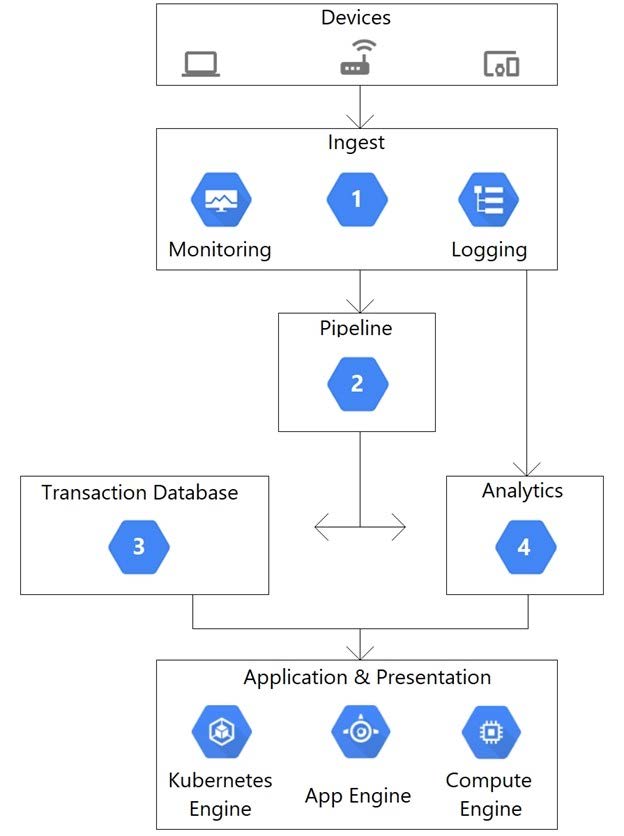
A. 1) App Engine 2) Pub/Sub 3) BigQuery 4) Firestore
B. 1) Dataflow 2) Pub/Sub 3) Firestore 4) BigQuery
C. 1) Pub/Sub 2) Dataflow 3) BigQuery 4) Firestore
D. 1) Pub/Sub 2) Dataflow 3) Firestore 4) BigQuery
-
Question 143:
You are developing a new application that has the following design requirements:
Creation and changes to the application infrastructure are versioned and auditable.
The application and deployment infrastructure uses Google-managed services as much as possible.
The application runs on a serverless compute platform. How should you design the application's architecture?
A. 1. Store the application and infrastructure source code in a Git repository.
2.
Use Cloud Build to deploy the application infrastructure with Terraform.
3.
Deploy the application to a Cloud Function as a pipeline step.
B. 1. Deploy Jenkins from the Google Cloud Marketplace, and define a continuous integration pipeline in Jenkins.
2.
Configure a pipeline step to pull the application source code from a Git repository.
3.
Deploy the application source code to App Engine as a pipeline step.
C. 1. Create a continuous integration pipeline on Cloud Build, and configure the pipeline to deploy the application infrastructure using Deployment Manager templates.
2.
Configure a pipeline step to create a container with the latest application source code.
3.
Deploy the container to a Compute Engine instance as a pipeline step.
D. 1. Deploy the application infrastructure using gcloud commands.
2.
Use Cloud Build to define a continuous integration pipeline for changes to the application source code.
3.
Configure a pipeline step to pull the application source code from a Git repository, and create a containerized application.
4.
Deploy the new container on Cloud Run as a pipeline step.
-
Question 144:
You support an application that uses the Cloud Storage API. You review the logs and discover multiple HTTP 503 Service Unavailable error responses from the API. Your application logs the error and does not take any further action. You want to implement Google-recommended retry logic to improve success rates. Which approach should you take?
A. Retry the failures in batch after a set number of failures is logged.
B. Retry each failure at a set time interval up to a maximum number of times.
C. Retry each failure at increasing time intervals up to a maximum number of tries.
D. Retry each failure at decreasing time intervals up to a maximum number of tries.
-
Question 145:
You are monitoring a web application that is written in Go and deployed in Google Kubernetes Engine. You notice an increase in CPU and memory utilization. You need to determine which source code is consuming the most CPU and memory resources. What should you do?
A. Download, install, and start the Snapshot Debugger agent in your VM. Take debug snapshots of the functions that take the longest time. Review the call stack frame, and identify the local variables at that level in the stack.
B. Import the Cloud Profiler package into your application, and initialize the Profiler agent. Review the generated flame graph in the Google Cloud console to identify time-intensive functions.
C. Import OpenTelemetry and Trace export packages into your application, and create the trace provider. Review the latency data for your application on the Trace overview page, and identify where bottlenecks are occurring.
D. Create a Cloud Logging query that gathers the web application's logs. Write a Python script that calculates the difference between the timestamps from the beginning and the end of the application's longest functions to identity time-intensive functions.
-
Question 146:
You are developing a microservice-based application that will run on Google Kubernetes Engine (GKE). Some of the services need to access different Google Cloud APIs. How should you set up authentication of these services in the cluster following Google- recommended best practices? (Choose two.)
A. Use the service account attached to the GKE node.
B. Enable Workload Identity in the cluster via the gcloud command-line tool.
C. Access the Google service account keys from a secret management service.
D. Store the Google service account keys in a central secret management service.
E. Use gcloud to bind the Kubernetes service account and the Google service account using roles/iam.workloadIdentity.
-
Question 147:
Users are complaining that your Cloud Run-hosted website responds too slowly during traffic spikes. You want to provide a better user experience during traffic peaks. What should you do?
A. Read application configuration and static data from the database on application startup.
B. Package application configuration and static data into the application image during build time.
C. Perform as much work as possible in the background after the response has been returned to the user.
D. Ensure that timeout exceptions and errors cause the Cloud Run instance to exit quickly so a replacement instance can be started.
-
Question 148:
Your company has a BigQuery dataset named "Master" that keeps information about employee travel and
expenses. This information is organized by employee department. That means employees should only be able
to view information for their department. You want to apply a security framework to enforce this requirement
with the minimum number of steps.
What should you do?
A. Create a separate dataset for each department. Create a view with an appropriate WHERE clause to select records from a particular dataset for the specific department. Authorize this view to access records from your Master dataset. Give employees the permission to this department-specific dataset.
B. Create a separate dataset for each department. Create a data pipeline for each department to copy appropriate information from the Master dataset to the specific dataset for the department.
Give employees
the permission to this department-specific dataset.
C. Create a dataset named Master dataset. Create a separate view for each department in the Master dataset. Give employees access to the specific view for their department.
D. Create a dataset named Master dataset. Create a separate table for each department in the Master dataset. Give employees access to the specific table for their department.
-
Question 149:
Your web application is deployed to the corporate intranet. You need to migrate the web application to Google Cloud. The web application must be available only to company employees and accessible to employees as they travel. You need to ensure the security and accessibility of the web application while minimizing application changes. What should you do?
A. Configure the application to check authentication credentials for each HTTP(S) request to the application.
B. Configure Identity-Aware Proxy to allow employees to access the application through its public IP address.
C. Configure a Compute Engine instance that requests users to log in to their corporate account. Change the web application DNS to point to the proxy Compute Engine instance. After authenticating, the Compute Engine instance forwards requests to and from the web application.
D. Configure a Compute Engine instance that requests users to log in to their corporate account. Change the web application DNS to point to the proxy Compute Engine instance. After authenticating, the Compute Engine issues an HTTP redirect to a public IP address hosting the web application.
-
Question 150:
You work at a rapidly growing financial technology startup. You manage the payment processing application written in Go and hosted on Cloud Run in the Singapore region (asia-southeast1). The payment processing application processes data stored in a Cloud Storage bucket that is also located in the Singapore region. The startup plans to expand further into the Asia Pacific region. You plan to deploy the Payment Gateway in Jakarta, Hong Kong, and Taiwan over the next six months. Each location has data residency requirements that require customer data to reside in the country where the transaction was made. You want to minimize the cost of these deployments. What should you do?
A. Create a Cloud Storage bucket in each region, and create a Cloud Run service of the payment processing application in each region.
B. Create a Cloud Storage bucket in each region, and create three Cloud Run services of the payment processing application in the Singapore region.
C. Create three Cloud Storage buckets in the Asia multi-region, and create three Cloud Run services of the payment processing application in the Singapore region.
D. Create three Cloud Storage buckets in the Asia multi-region, and create three Cloud Run revisions of the payment processing application in the Singapore region.
Related Exams:
ADWORDS-DISPLAY
Google AdWords: Display AdvertisingADWORDS-FUNDAMENTALS
Google AdWords: FundamentalsADWORDS-MOBILE
Google AdWords: Mobile AdvertisingADWORDS-REPORTING
Google AdWords: ReportingADWORDS-SEARCH
Google AdWords: Search AdvertisingADWORDS-SHOPPING
Google AdWords: Shopping AdvertisingADWORDS-VIDEO
Google AdWords: Video AdvertisingAPIGEE-API-ENGINEER
Apigee Certified API EngineerASSOCIATE-ANDROID-DEVELOPER
Associate Android Developer (Kotlin and Java)ASSOCIATE-CLOUD-ENGINEER
Associate Cloud Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Google exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PROFESSIONAL-CLOUD-DEVELOPER exam preparations and Google certification application, do not hesitate to visit our Vcedump.com to find your solutions here.