Exam Details
Exam Code
:PCCSAExam Name
:Palo Alto Networks Certified Cybersecurity Associate (PCCSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:79 Q&AsLast Updated
:Aug 16, 2025
Palo Alto Networks Palo Alto Networks Certifications PCCSA Questions & Answers
-
Question 21:
Which two reconnaissance tools might an attacker use to scan for vulnerable network services and settings? (Choose two.)
A. bandwidth analyzer
B. intrusion detection
C. port scanner
D. password cracker
-
Question 22:
During which step of the cyber-attack lifecycle is a user's web browser redirected to a webpage that automatically downloads malware to the endpoint?
A. delivery
B. weaponization
C. reconnaissance
D. command-and-control
-
Question 23:
Review the exhibit and identify the type of vulnerability or attack.
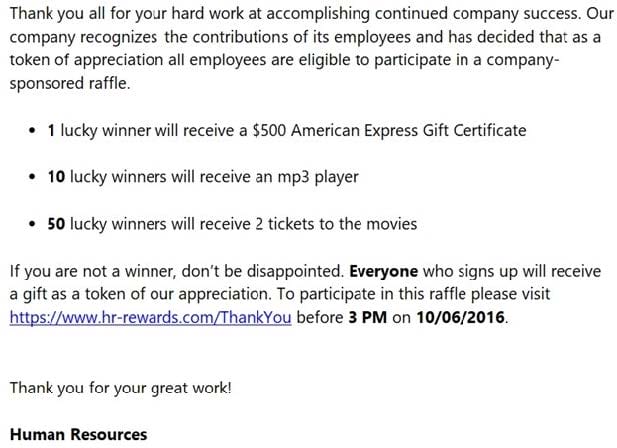
A. botnet
B. man-in-the-middle
C. spear phishing
D. buffer overflow
-
Question 24:
Which type of cloud computing deployment makes resources exclusively available to members of a single organization?
A. local
B. private
C. hybrid
D. public
-
Question 25:
In the context of a mobile device management solution, what is a function of the "policy enforcement" feature?
A. controls which websites can be accessed when connected to Wi-Fi
B. controls which Wi-Fi networks can be accessed
C. controls which phone numbers can be dialed
D. controls which password/passcode settings are allowed
-
Question 26:
What method can be used to guarantee that a document originates from you and no one else?
A. public key encryption, encrypting the document with the private key and making the public key available to others
B. symmetric encryption, ecnrypting the document with the secret key and making a different secret key available to others
C. symmetric encryption, ecnrypting the document with the secret key and making the same secret kay available to others
D. public key encryption, encrypting the document with the private key and making the private key available to others
-
Question 27:
Company policy allows employees to access the internet. While searching for office supplies on the internet, a corporate user mistypes a URL, connects to a malicious website, and unknowingly downloads malware.
Which action should have been taken to prevent the malware download but still allow user access to the internet?
A. deploy a firewall with content filtering capabilities on the corporate perimeter
B. allow only encrypted HTTPS access to the internet
C. configure digital certificates for all users to authenticate internet downloads
D. permit web connections only to TCP port 443
-
Question 28:
Assume that it is your responsibility to secure the software functioning at all layers in the exhibit.
Which cloud service model type is represented?
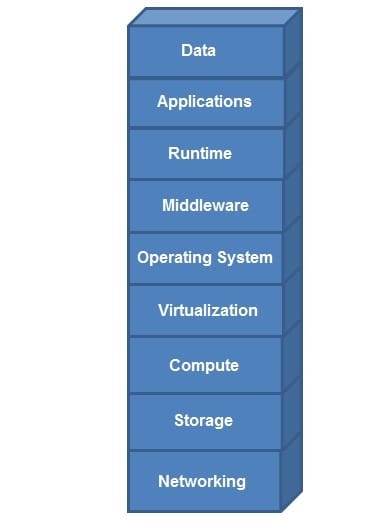
A. software as a service
B. platform as a service
C. infrastructure as a service
D. on-premises
-
Question 29:
Which security principle describes the practice of giving users the minimum rights to access the resources necessary to do their jobs?
A. known privilege
B. least privilege
C. user privilege
D. lowest privilege
-
Question 30:
An attacker emails a malicious URL links to 50,000 email addresses. The email states that users can click the link to view the latest celebrity news, but the link also secretly infects the user's laptop. This scenario describes which type of attack?
A. whailing
B. phishing
C. drive-by download
D. pharming
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCCSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.