Exam Details
Exam Code
:PAM-DEFExam Name
:CyberArk Defender - PAMCertification
:CyberArk CertificationsVendor
:CyberArkTotal Questions
:254 Q&AsLast Updated
:Jul 19, 2025
CyberArk CyberArk Certifications PAM-DEF Questions & Answers
-
Question 201:
Which utilities could you use to change debugging levels on the vault without having to restart the vault. Select all that apply.
A. PAR Agent
B. PrivateArk Server Central Administration
C. Edit DBParm.ini in a text editor.
D. Setup.exe
-
Question 202:
CyberArk recommends implementing object level access control on all Safes.
A. True
B. False
-
Question 203:
Within the Vault each password is encrypted by:
A. the server key
B. the recovery public key
C. the recovery private key
D. its own unique key
-
Question 204:
You have been asked to secure a set of shared accounts in CyberArk whose passwords will need to be used by end users. The account owner wants to be able to track who was using an account at any given moment.
Which security configuration should you recommend?
A. Configure one-time passwords for the appropriate platform in Master Policy.
B. Configure shared account mode on the appropriate safe.
C. Configure both one-time passwords and exclusive access for the appropriate platform in Master Policy.
D. Configure object level access control on the appropriate safe.
-
Question 205:
You have been asked to identify the up or down status of Vault services.
Which CyberArk utility can you use to accomplish this task?
A. Vault Replicator
B. PAS Reporter
C. Remote Control Agent
D. Syslog
-
Question 206:
What is the maximum number of levels of authorization you can set up in Dual Control?
A. 1
B. 2
C. 3
D. 4
-
Question 207:
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password. What is the least intrusive way to accomplish this?
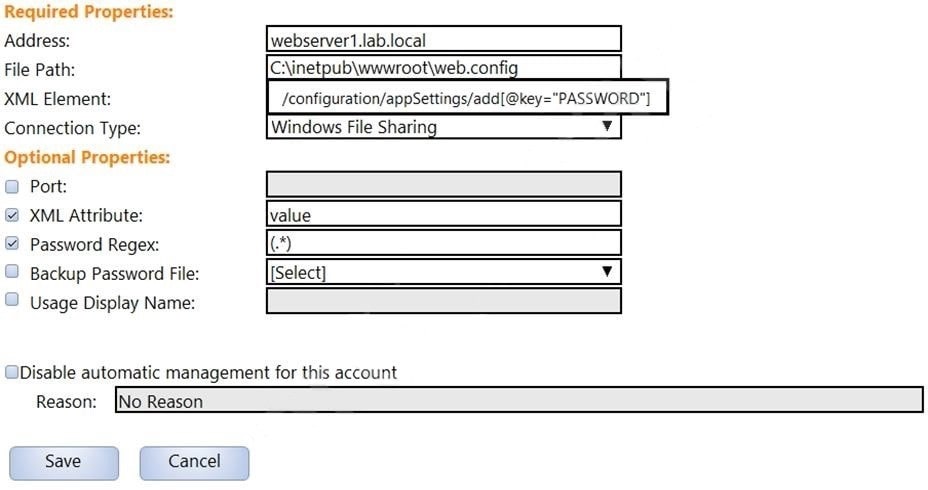
A. Use the "change" button on the usage's details page.
B. Use the "change" button on the parent account's details page.
C. Use the "sync" button on the usage's details page.
D. Use the "reconcile" button on the parent account's details page.
-
Question 208:
When managing SSH keys, the CPM stores the Public Key
A. In the Vault
B. On the target server
C. A and B
D. Nowhere because the public key can always be generated from the private key.
-
Question 209:
Which of the following statements are NOT true when enabling PSM recording for a target Windows server? (Choose all that apply)
A. The PSM software must be instated on the target server
B. PSM must be enabled in the Master Policy (either directly, or through exception)
C. PSMConnect must be added as a local user on the target server
D. RDP must be enabled on the target server
-
Question 210:
What is the purpose of the Interval setting in a CPM policy?
A. To control how often the CPM looks for System Initiated CPM work.
B. To control how often the CPM looks for User Initiated CPM work.
C. To control how long the CPM rests between password changes.
D. To control the maximum amount of time the CPM will wait for a password change to complete.
Related Exams:
CAU201
CyberArk DefenderCAU301
CyberArk SentryCAU302
CyberArk Defender - SentryCAU305
Sentry (Combined) CAU305 - CyberArk CDE RecertificationCPC-SEN
CyberArk Sentry - Privilege CloudEPM-DEF
CyberArk Defender - EPMPAM-CDE-RECERT
CyberArk CDE RecertificationPAM-DEF
CyberArk Defender - PAMPAM-SEN
CyberArk Sentry PAMSECRET-SEN
CyberArk Sentry - Secrets Manager
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CyberArk exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PAM-DEF exam preparations and CyberArk certification application, do not hesitate to visit our Vcedump.com to find your solutions here.