Exam Details
Exam Code
:NSE7_SAC-6.2Exam Name
:Fortinet NSE 7 - Secure Access 6.2Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:30 Q&AsLast Updated
:Aug 05, 2025
Fortinet Fortinet Certifications NSE7_SAC-6.2 Questions & Answers
-
Question 11:
Examine the following RADIUS configuration:
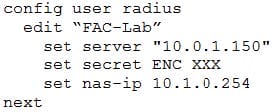
An administrator has configured a RADIUS server on FortiGate that points to FortiAuthenticator. FortiAuthenticator is acting as an authentication proxy and is configured to relay all authentication requests to a remote Windows AD server using LDAP.
While testing the configuration, the administrator notices that the diagnose test authservercommand works with PAP, however, authentication requests fail when using MSCHAPv2.
Which two changes should the administrator make to get MSCHAPv2 to work? (Choose two.)
A. Force FortiGate to use the PAP authentication method in the RADIUS server configuration.
B. Change the remote authentication server from LDAP to RADIUS on FortiAuthenticator.
C. Use MSCHAP instead of using MSCHAPv2
D. Enable Windows Active Directory Domain Authentication on FortiAuthenticator to add FortiAuthenticator to the Windows domain.
-
Question 12:
Refer to the exhibits.
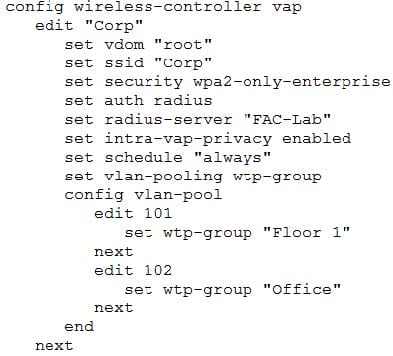
Examine the VAP configuration and the WiFi zones table shown in the exhibits.
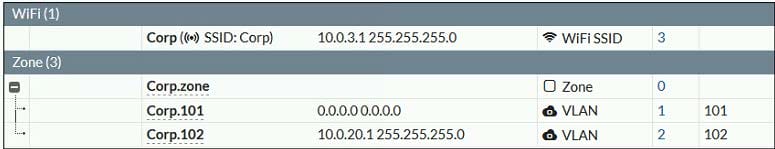
Which two statements describe FortiGate behavior regarding assignment of VLANs to wireless clients? (Choose two.)
A. FortiGate will load balance clients using VLAN 101 and VLAN 102 and assign them an IP address from the 10.0.3.0/24 subnet.
B. Clients connecting to APs in the Floor 1 group will not be able to receive an IP address.
C. All clients connecting to the Corp SSID will receive an IP address from the 10.0.3.1/24 subnet.
D. Clients connecting to APs in the Office group will be assigned an IP address from the 10.0.20.1/24 subnet.
-
Question 13:
What is the purpose of configuring the Windows Active Directory Domain Authentication feature?
A. Allows FortiAuthenticator to register itself as a Windows trusted device to proxy CHAP authentication using Kerberos.
B. Allows FortiAuthenticator to use Windows administrator credentials to perform an LDAP lookup for a user search.
C. Allows FortiAuthenticator to use a Windows CA certificate when authenticating RADIUS users.
D. Allows FortiAuthenticator to authenticate users listed on Windows AD. Enables single sign-on services for VPN and wireless users.
-
Question 14:
Refer to the exhibit.
Examine the partial debug output shown in the exhibit.
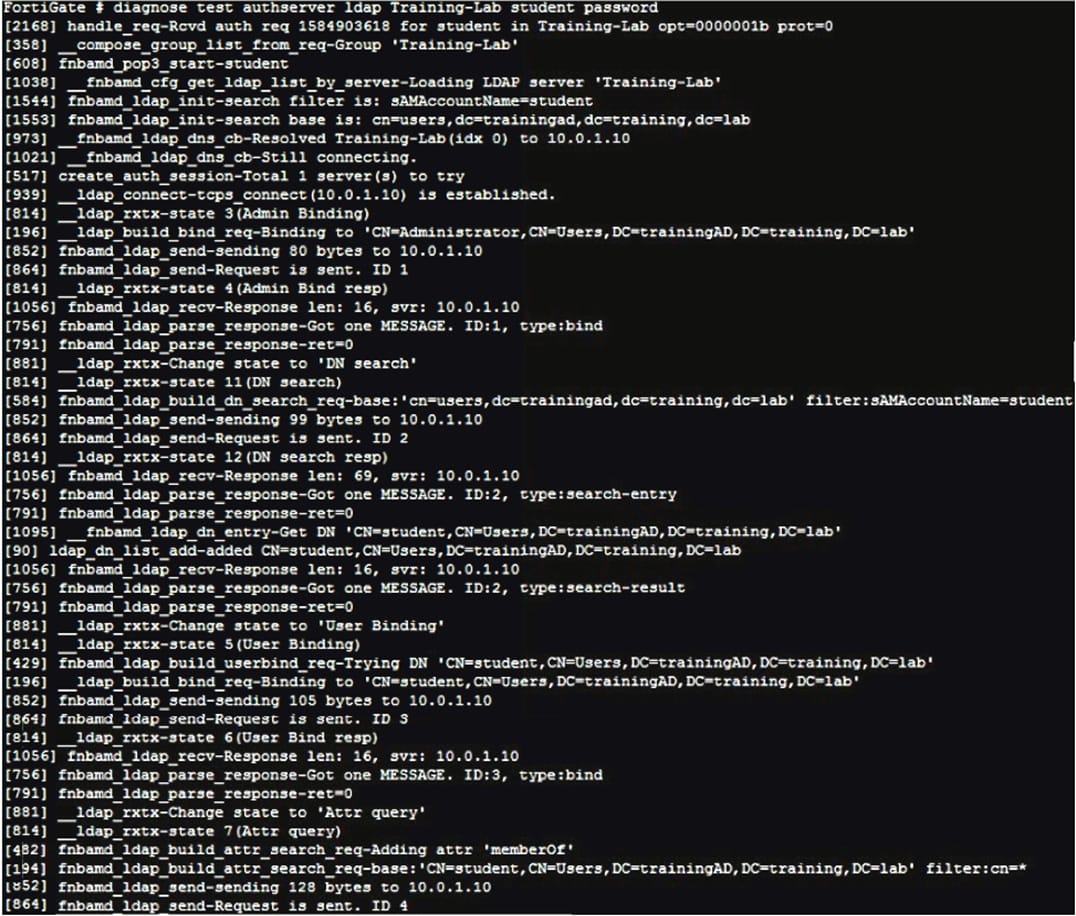
Which two statements about the debug output are true? (Choose two.)
A. The connection to the LDAP server timed out.
B. The user authenticated successfully.
C. The LDAP server is configured to use regular bind.
D. The debug output shows multiple user authentications.
-
Question 15:
Refer to the exhibit.
Examine the packet capture shown in the exhibit, which contains a RADIUS access request packet sent by FortiSwitch to a RADIUS server.
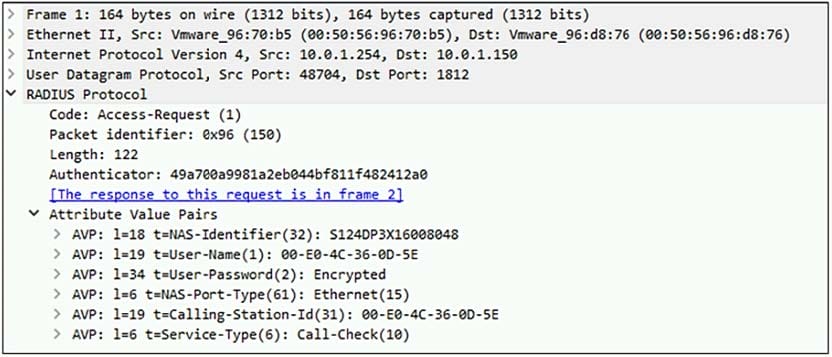
Why does the User-Name field in the RADIUS access request packet contain a MAC address?
A. The FortiSwitch interface is configured for 802.1X port authentication with MAC address bypass, and the connected device does not support 802.1X.
B. FortiSwitch authenticates itself using its MAC address as the user name.
C. The connected device is doing machine authentication.
D. FortiSwitch is replying to an access challenge packet sent by the RADIUS server and requesting the client MAC address.
-
Question 16:
Refer to the exhibits.
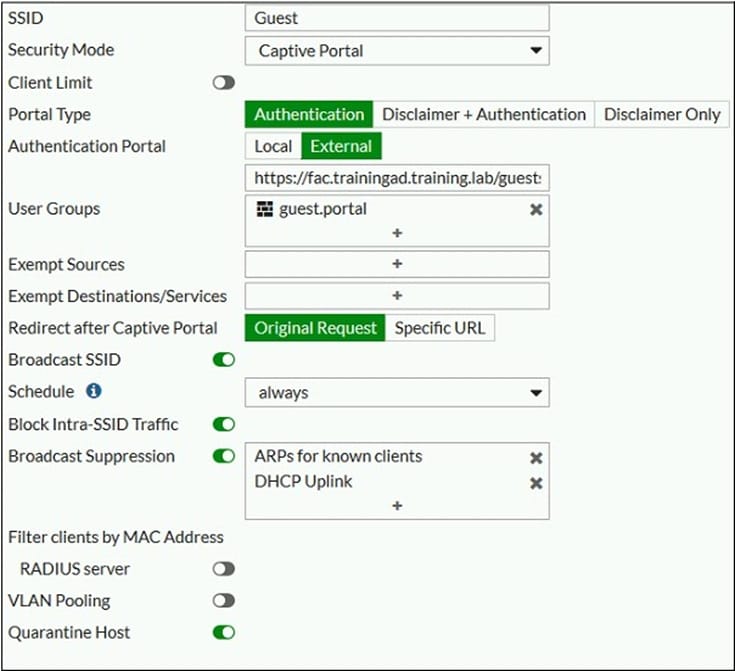
Examine the firewall policy configuration and SSID settings.
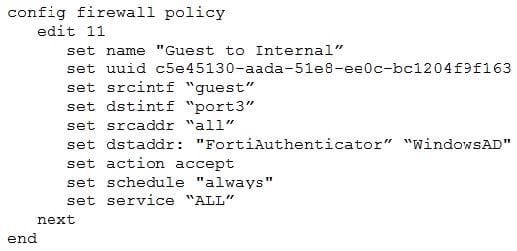
An administrator has configured a guest wireless network on FortiGate using the external captive portal. The administrator has verified that the external captive portal URL is correct. However, wireless users are not able to see the captive portal login page.
Given the configuration shown in the exhibit and the SSID settings, which configuration change should the administrator make to fix the problem?
A. Enable the captive-portal-exemptoption in the firewall policy with the ID 11.
B. Apply a guest.portal user group in the firewall policy with the ID 11.
C. Disable the user group from the SSID configuration.
D. Include the wireless client subnet range in the Exempt Source section.
-
Question 17:
Refer to the exhibit.
Examine the configuration of the FortiSwitch security policy profile.
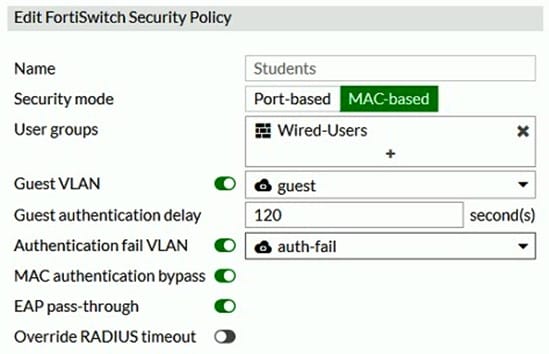
If the security profile shown in the exhibit is assigned on the FortiSwitch port for 802.1X.port authentication, which statement is correct?
A. Host machines that do support 802.1X authentication, but have failed authentication, will be assigned the guest VLAN.
B. All unauthenticated users will be assigned the auth-fail VLAN.
C. Authenticated users that are part of the wired-users group will be assigned the guest VLAN.
D. Host machines that do not support 802.1X authentication will be assigned the guest VLAN.
-
Question 18:
Which statement correctly describes the quest portal behavior on FortiAuthenticator?
A. Sponsored accounts cannot authenticate using guest portals.
B. FortiAuthenticator uses POST parameters and a RADIUS client configuration to map the request to a guest portal for authentication.
C. All guest accounts must be activated using SMS or email activation codes.
D. All self-registered and sponsored accounts are listed on the local Users GUI page on FortiAuthenticator.
-
Question 19:
Examine the sections of the configuration shown in the following output:
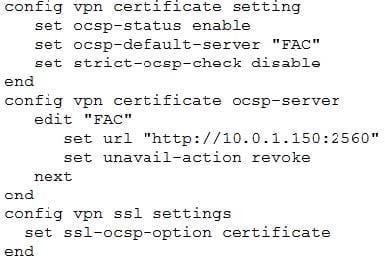
What action will the FortiGate take when using OCSP certificate validation?
A. FortiGate will reject the certificate if the OCSP server replies that the certificate is unknown.
B. FortiGate will use the OCSP server 10.0.1.150 even when the OCSP URL field in the user certificate
contains a different OCSP server IP address.
C. FortiGate will use the OCSP server 10.0.1.150 even when there is a different OCSP IP address in the ocsp-override-serveroption under config user peer.
D. FortiGate will invalidate the certificate if the OSCP server is unavailable.
-
Question 20:
What does DHCP snooping MAC verification do?
A. Drops DHCP release packets on untrusted ports
B. Drops DHCP packets with no relay agent information (option 82) on untrusted ports
C. Drops DHCP offer packets on untrusted ports
D. Drops DHCP packets on untrusted ports when the client hardware address does not match the source MAC address
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE7_SAC-6.2 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.