Exam Details
Exam Code
:NSE7_ADA-6.3Exam Name
:Fortinet NSE 7 - Advanced Analytics 6.3Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:34 Q&AsLast Updated
:Aug 11, 2025
Fortinet Fortinet Certifications NSE7_ADA-6.3 Questions & Answers
-
Question 11:
Which syntax will register a collector to the supervisor?
A. phProvisionCollector --add
B. phProvisionCollector --add
C. phProvisionCollector --add
D. phProvisionCollector --add
-
Question 12:
Refer to the exhibit.
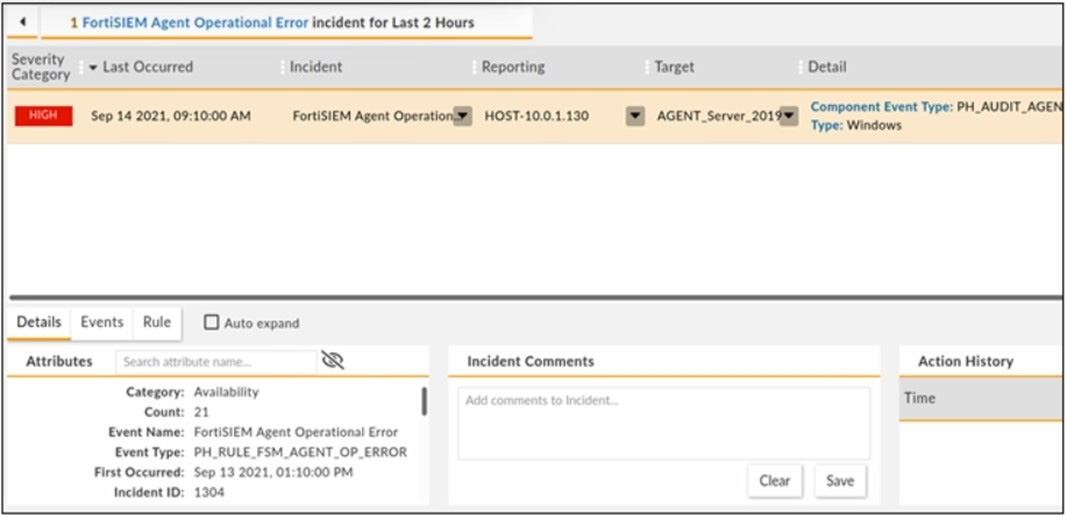
How long has the UEBA agent been operationally down?
A. 21 Hours
B. 9 Hours
C. 20 Hours
D. 2 Hours
-
Question 13:
Refer to the exhibit.
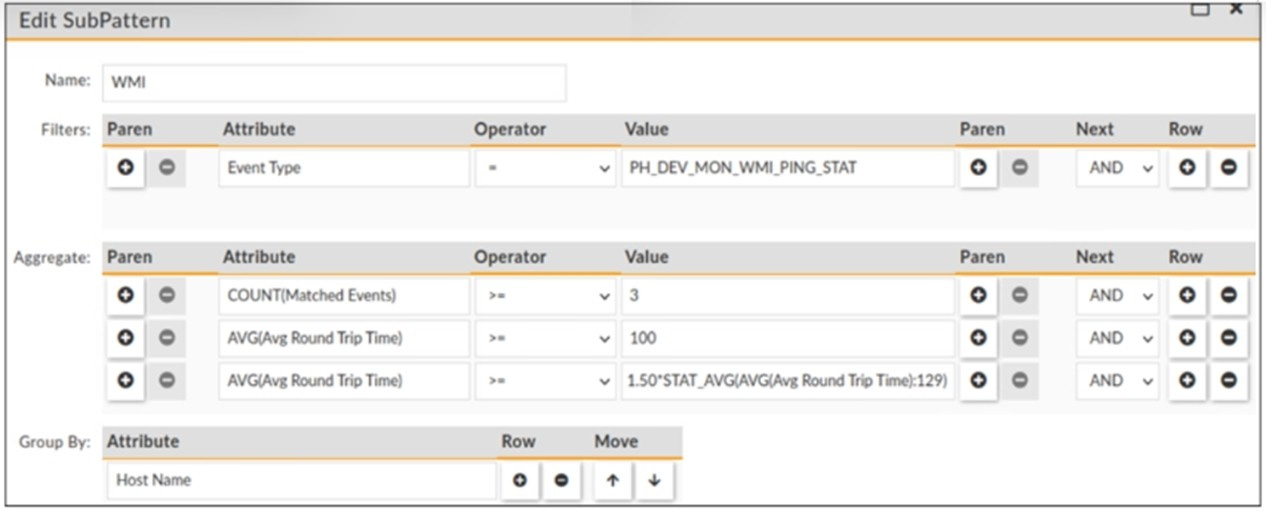
The window for this rule is 30 minutes. What is this rule tracking?
A. A sudden 50% increase in WMI response times over a 30-minute time window
B. A sudden 1.50 times increase in WMI response times over a 30-minute time window
C. A sudden 75% increase in WMI response times over a 30-minute time window
D. A sudden 150% increase in WMI response times over a 30-minute time window
-
Question 14:
Refer to the exhibit. Click on the calculator button.
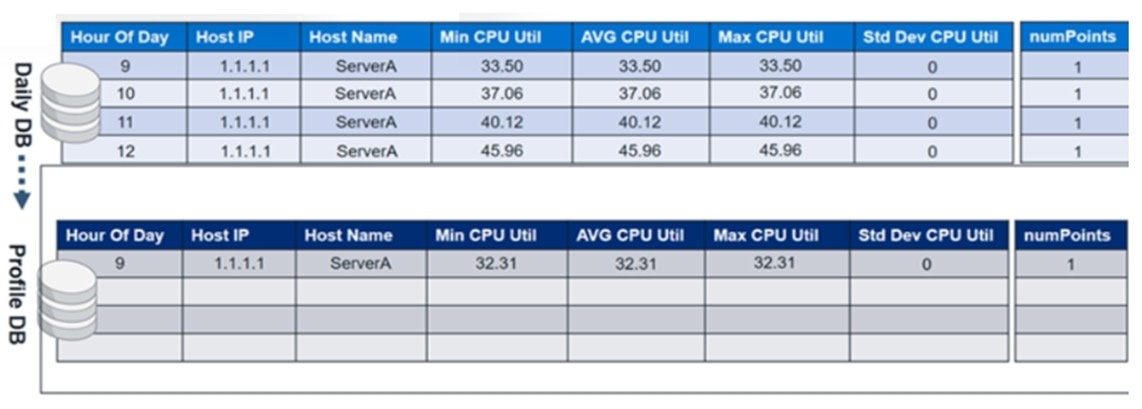
The profile database contains CPU utilization values from day one. At midnight on the second day, the CPU utilization values from the daily database will be merged with the profile database.
In the profile database, in the Hour of Day column where 9 is the value, what will be the updated minimum, maximum, and average CPU utilization values?
A. Min CPU Util=32.31, Max CPU Ucil=33.50 and AVG CPU Util=33.50
B. Min CPU Util=32.31, Max CPU Ucil=33.50 and AVG CPU Util=32.67
C. Min CPU Util=32.31, Max CPU Ucil=32.31 and AVG CPU Util=32.31
D. Min CPU Util=33.50, Max CPU Ucil=33.50 and AVG CPU Util=33.50
-
Question 15:
Which of the following are two Tactics in the MITRE ATTandCK framework? (Choose two.)
A. Root kit
B. Reconnaissance
C. Discovery
D. BITS Jobs
E. Phishing
-
Question 16:
Refer to the exhibit.
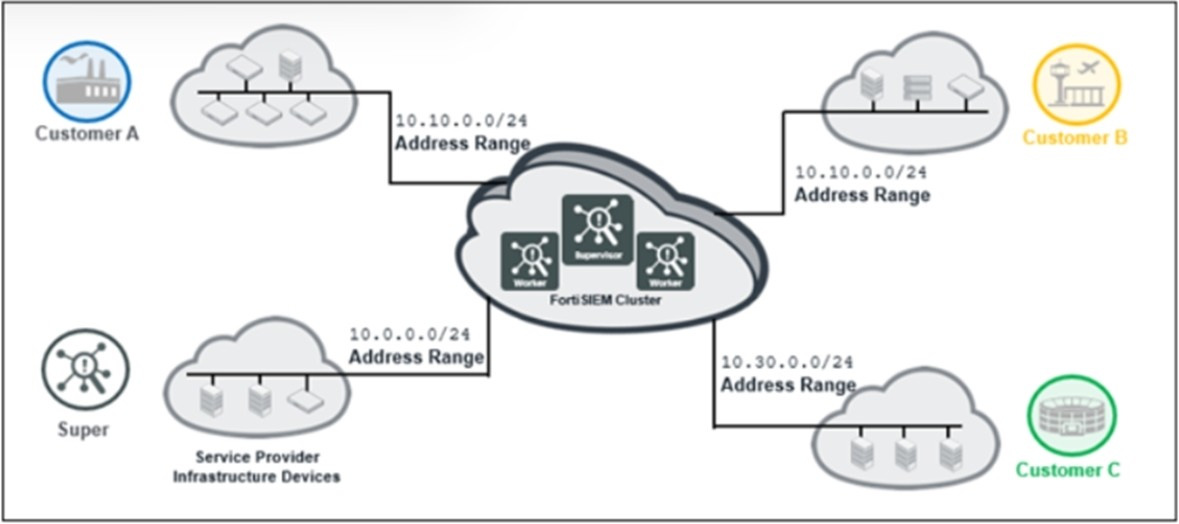
The service provider deployed FortiSIEM without a collector and added three customers on the supervisor. What mistake did the administrator make?
A. Customer A and customer B have overlapping IP addresses.
B. Collectors must be deployed on all customer premises before they are added to organizations on the supervisor.
C. The number of workers on the FortiSIEM cluster must match the number of customers added.
D. At least one collector must be deployed to collect logs from service provider infrastructure devices.
-
Question 17:
How can you invoke an integration policy on FortiSIEM rules?
A. Through Notification Policy settings
B. Through Incident Notification settings
C. Through remediation scripts
D. Through External Authentication settings
-
Question 18:
Refer to the exhibit.
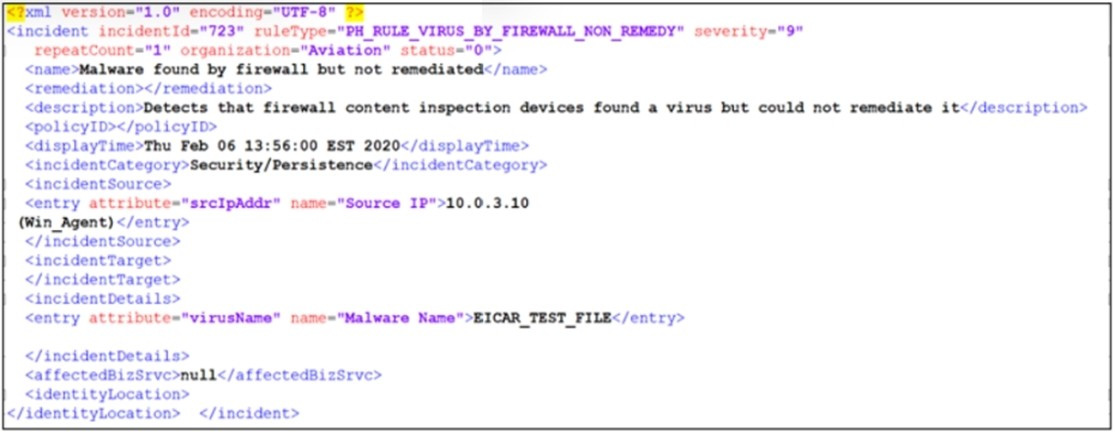
An administrator wants to remediate the incident from FortiSIEM shown in the exhibit.
What option is available to the administrator?
A. Quarantine IP FortiClient
B. Run the block MAC FortiOS.
C. Run the block IP FortiOS 5.4
D. Run the block domain Windows DNS
-
Question 19:
What is Tactic in the MITRE ATTandCK framework?
A. Tactic is how an attacker plans to execute the attack
B. Tactic is what an attacker hopes to achieve
C. Tactic is the tool that the attacker uses to compromise a system
D. Tactic is a specific implementation of the technique
-
Question 20:
How can you empower SOC by deploying FortiSOAR? (Choose three.)
A. Aggregate logs from distributed systems
B. Collaborative knowledge sharing
C. Baseline user and traffic behavior
D. Reduce human error
E. Address analyst skills gap
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE7_ADA-6.3 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.