Exam Details
Exam Code
:NSE6_FWB-6.4Exam Name
:Fortinet NSE 6 - FortiWeb 6.4Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:56 Q&AsLast Updated
:Jul 12, 2025
Fortinet Fortinet Certifications NSE6_FWB-6.4 Questions & Answers
-
Question 41:
Which two statements about the anti-defacement feature on FortiWeb are true? (Choose two.)
A. Anti-defacement can redirect users to a backup web server, if it detects a change.
B. Anti-defacement downloads a copy of your website to RAM, in order to restore a clean image, if it detects defacement.
C. FortiWeb will only check to see if there are changes on the web server; it will not download the whole file each time.
D. Anti-defacement does not make a backup copy of your databases.
-
Question 42:
A client is trying to start a session from a page that would normally be accessible only after the client has logged in. When a start page rule detects the invalid session access, what can FortiWeb do? (Choose three.)
A. Display an access policy message, then allow the client to continue
B. Redirect the client to the login page
C. Allow the page access, but log the violation
D. Prompt the client to authenticate
E. Reply with a 403 Forbidden HTTP error
-
Question 43:
Refer to the exhibit.
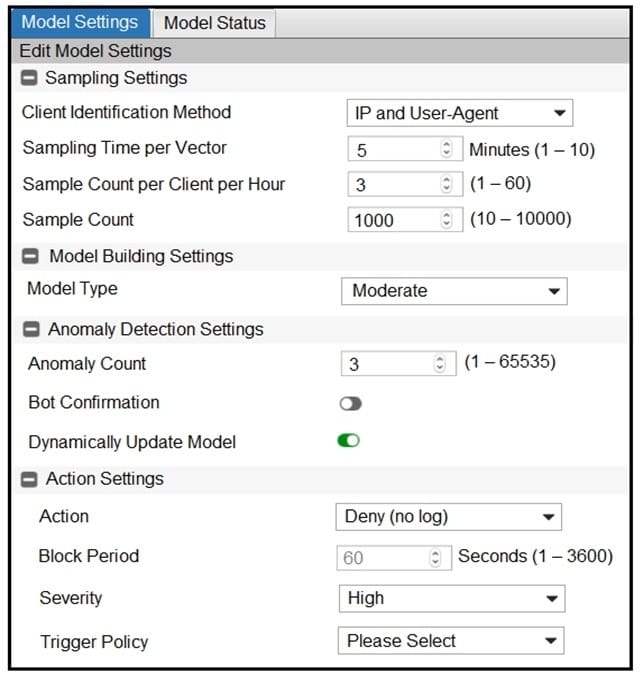
Many legitimate users are being identified as bots. FortiWeb bot detection has been configured with the settings shown in the exhibit. The FortiWeb administrator has already verified that the current model is accurate.
What can the administrator do to fix this problem, making sure that real bots are not allowed through FortiWeb?
A. Change Model Type to Strict
B. Change Action under Action Settings to Alert
C. Disable Dynamically Update Model
D. Enable Bot Confirmation
-
Question 44:
Refer to the exhibit.
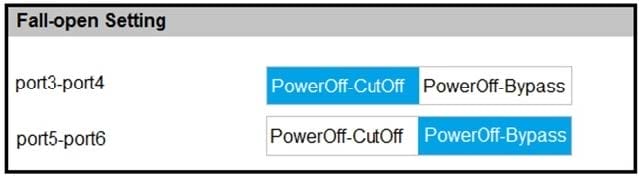
Based on the configuration, what would happen if this FortiWeb were to lose power? (Choose two.)
A. Traffic that passes between port5 and port6 will be inspected.
B. Traffic will be interrupted between port3 and port4.
C. All traffic will be interrupted.
D. Traffic will pass between port5 and port6 uninspected.
-
Question 45:
How does FortiWeb protect against defacement attacks?
A. It keeps a complete backup of all files and the database.
B. It keeps hashes of files and periodically compares them to the server.
C. It keeps full copies of all files and directories.
D. It keeps a live duplicate of the database.
-
Question 46:
The FortiWeb machine learning (ML) feature is a two-phase analysis mechanism. Which two functions does the first layer perform? (Choose two.)
A. Determines whether an anomaly is a real attack or just a benign anomaly that should be ignored
B. Builds a threat model behind every parameter and HTTP method
C. Determines if a detected threat is a false-positive or not
D. Determines whether traffic is an anomaly, based on observed application traffic over time
-
Question 47:
Which would be a reason to implement HTTP rewriting?
A. The original page has moved to a new URL
B. To replace a vulnerable function in the requested URL
C. To send the request to secure channel
D. The original page has moved to a new IP address
-
Question 48:
An e-commerce web app is used by small businesses. Clients often access it from offices behind a router, where clients are on an IPv4 private network LAN. You need to protect the web application from denial of service attacks that use request floods.
What FortiWeb feature should you configure?
A. Enable "Shared IP" and configure the separate rate limits for requests from NATted source IPs.
B. Configure FortiWeb to use "X-Forwarded-For:" headers to find each client's private network IP, and to block attacks using that.
C. Enable SYN cookies.
D. Configure a server policy that matches requests from shared Internet connections.
-
Question 49:
Refer to the exhibit.
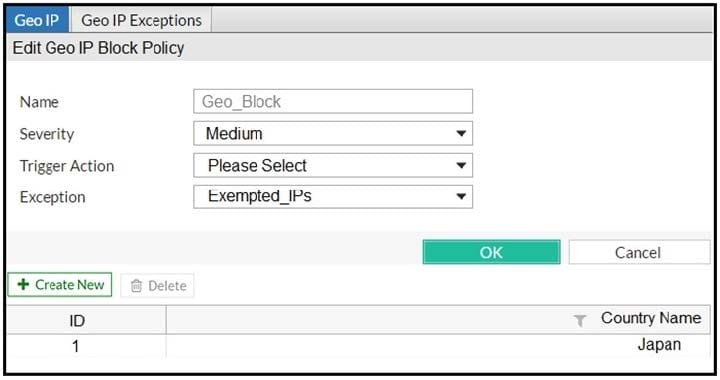
FortiWeb is configured to block traffic from Japan to your web application server. However, in the logs, the administrator is seeing traffic allowed from one particular IP address which is geo-located in Japan. What can the administrator do to solve this problem? (Choose two.)
A. Manually update the geo-location IP addresses for Japan.
B. If the IP address is configured as a geo reputation exception, remove it.
C. Configure the IP address as a blacklisted IP address.
D. If the IP address is configured as an IP reputation exception, remove it.
-
Question 50:
Which of the following FortiWeb features is part of the mitigation tools against OWASP A4 threats?
A. Sensitive info masking
B. Poison Cookie detection
C. Session Management
D. Brute Force blocking
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE6_FWB-6.4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.