NSE5_FCT-7.0 Exam Details
-
Exam Code
:NSE5_FCT-7.0 -
Exam Name
:Fortinet NSE 5 - FortiClient EMS 7.0 -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:49 Q&As -
Last Updated
:Jan 15, 2026
Fortinet NSE5_FCT-7.0 Online Questions & Answers
-
Question 1:
Refer to the exhibit.
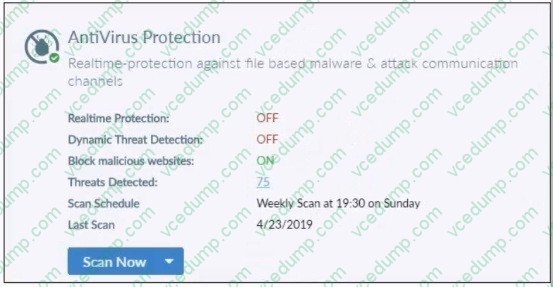
Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?
A. Blocks the infected files as it is downloading
B. Quarantines the infected files and logs all access attempts
C. Sends the infected file to FortiGuard for analysis
D. Allows the infected file to download without scan -
Question 2:
An administrator is required to maintain a software inventory on the endpoints. without showing the feature on the FortiClient dashboard What must the administrator do to achieve this requirement?
A. The administrator must use default endpoint profile
B. The administrator must not select the vulnerability scan feature in the deployment package.
C. The administrator must select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
D. The administrator must click the hide icon on the vulnerability scan tab -
Question 3:
Refer to the exhibits.
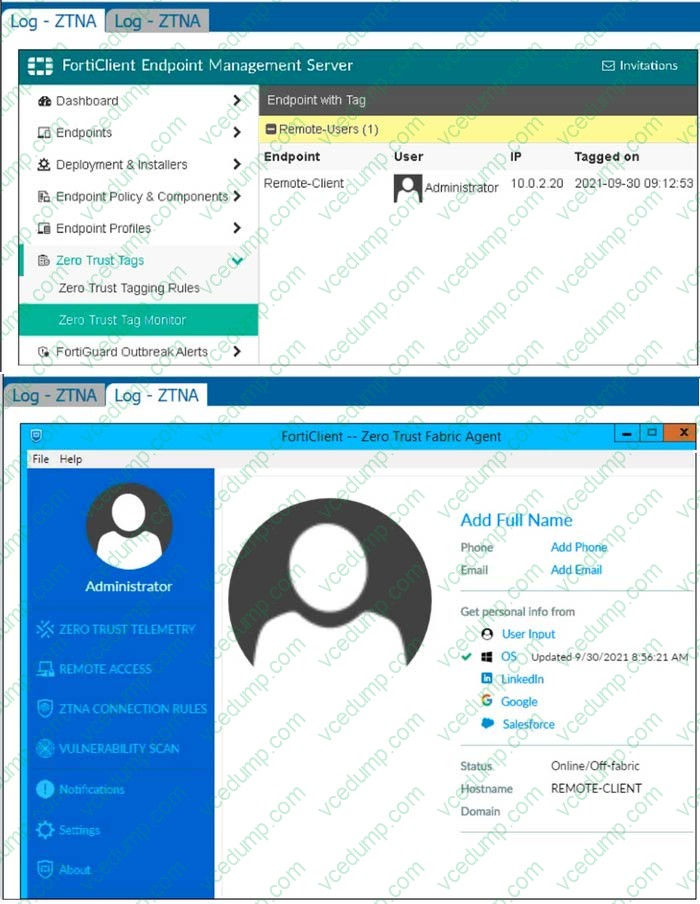
Which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
A. Update tagging rule logic to enable tag visibility
B. Change the FortiClient system settings to enable tag visibility
C. Change the endpoint control setting to enable tag visibility
D. Change the user identity settings to enable tag visibility -
Question 4:
Refer to the exhibit.
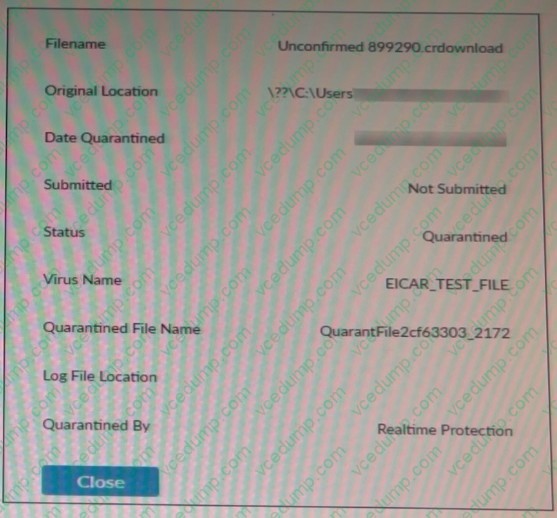
Based on the FortiClient log details shown in the exhibit, which two statements are true? (Choose two.)
A. The file status is Quarantined
B. The filename is sent to ForuSandbox for further inspection.
C. The file location IS \??\D:\Users\.
D. The filename is Unconfirmed 899290 .crdownload. -
Question 5:
Refer to the exhibit.
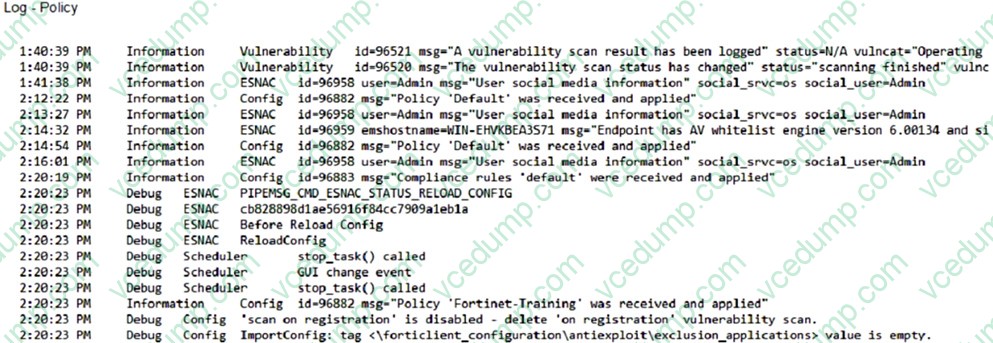
Based on the FortiClient logs shown in the exhibit which endpoint profile policy is currently applied to the FortiClient endpoint from the EMS server?
A. Default
B. Compliance rules default
C. Fortinet- Training
D. Default configuration policy -
Question 6:
Why does FortiGate need the root CA certificate of FortiClient EMS?
A. To sign FortiClient CSR requests
B. To revoke FortiClient client certificates
C. To trust certificates issued by FortiClient EMS
D. To update FortiClient client certificates -
Question 7:
Refer to the exhibit.
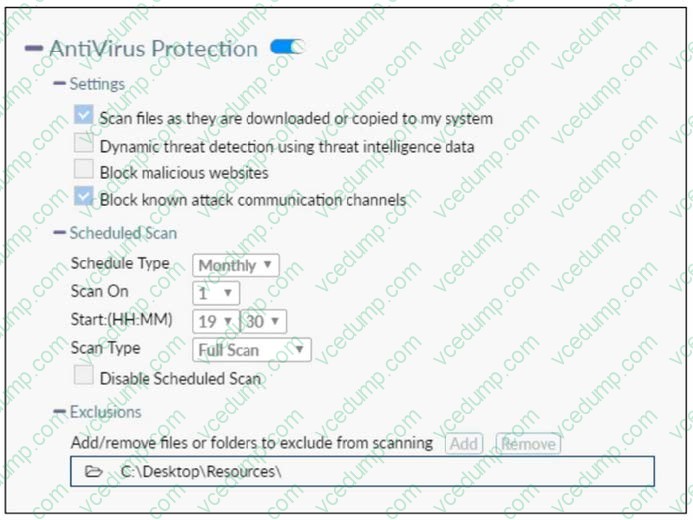
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
A. FortiClient quarantines infected files and reviews later, after scanning them.
B. FortiClient blocks and deletes infected files after scanning them.
C. FortiClient scans infected files when the user copies files to the Resources folder
D. FortiClient copies infected files to the Resources folder without scanning them. -
Question 8:
Which two statements are true about ZTNA? (Choose two.)
A. ZTNA provides role-based access
B. ZTNA manages access for remote users only
C. ZTNA manages access through the client only
D. ZTNA provides a security posture check -
Question 9:
What action does FortiClient anti-exploit detection take when it detects exploits?
A. Blocks memory allocation to the compromised application process
B. Patches the compromised application process
C. Deletes the compromised application process
D. Terminates the compromised application process -
Question 10:
Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
A. Microsoft Windows Installer
B. Microsoft SCCM
C. Microsoft Active Directory GPO
D. QR code generator
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE5_FCT-7.0 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.