Exam Details
Exam Code
:NSE4_FGT-7.0Exam Name
:Fortinet NSE 4 - FortiOS 7.0Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:172 Q&AsLast Updated
:Aug 11, 2025
Fortinet Fortinet Certifications NSE4_FGT-7.0 Questions & Answers
-
Question 61:
Which of the following SD-WAN load 璪alancing method use interface weight value to distribute traffic? (Choose two.)
A. Source IP
B. Spillover
C. Volume
D. Session
-
Question 62:
Examine the network diagram shown in the exhibit, then answer the following question: Which one of the following routes is the best candidate route for FGT1 to route traffic from the Workstation to the Web server?
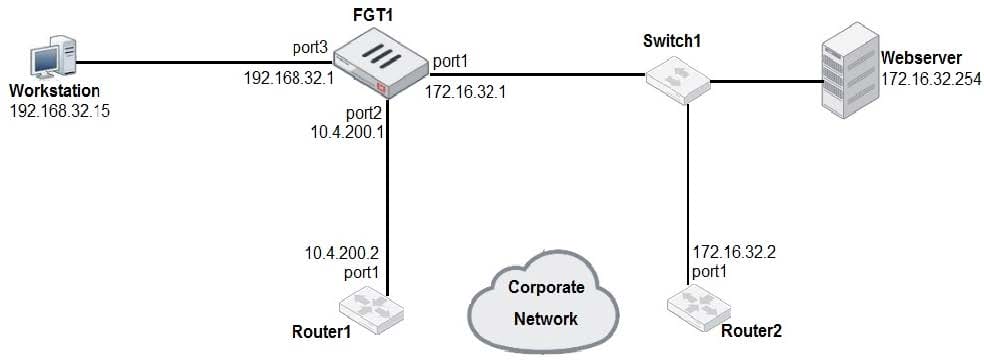
A. 172.16.0.0/16 [50/0] via 10.4.200.2, port2 [5/0]
B. 0.0.0.0/0 [20/0] via 10.4.200.2, port2
C. 10.4.200.0/30 is directly connected, port2
D. 172.16.32.0/24 is directly connected, port1
-
Question 63:
In consolidated firewall policies, IPv4 and IPv6 policies are combined in a single consolidated policy. Instead of separate policies. Which three statements are true about consolidated IPv4 and IPv6 policy configuration? (Choose three.)
A. The IP version of the sources and destinations in a firewall policy must be different.
B. The Incoming Interface. Outgoing Interface. Schedule, and Service fields can be shared with both IPv4 and IPv6.
C. The policy table in the GUI can be filtered to display policies with IPv4, IPv6 or IPv4 and IPv6 sources and destinations.
D. The IP version of the sources and destinations in a policy must match.
E. The policy table in the GUI will be consolidated to display policies with IPv4 and IPv6 sources and destinations.
-
Question 64:
Which three statements about security associations (SA) in IPsec are correct? (Choose three.)
A. Phase 2 SAs are used for encrypting and decrypting the data exchanged through the tunnel.
B. An SA never expires.
C. A phase 1 SA is bidirectional, while a phase 2 SA is directional.
D. Phase 2 SA expiration can be time-based, volume-based, or both.
E. Both the phase 1 SA and phase 2 SA are bidirectional.
-
Question 65:
Refer to the exhibit.
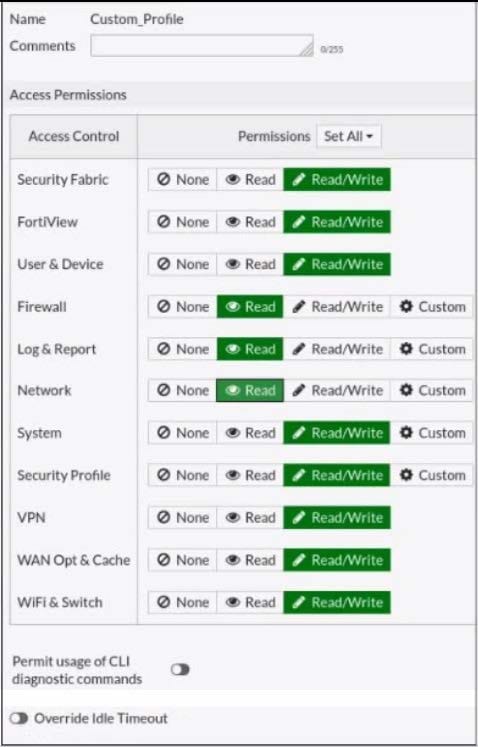
Based on the administrator profile settings, what permissions must the administrator set to run the diagnose firewall auth list CLI command on FortiGate?
A. Custom permission for Network
B. Read/Write permission for Log and Report
C. CLI diagnostics commands permission
D. Read/Write permission for Firewall
-
Question 66:
An administrator is configuring an Ipsec between site A and siteB. The Remotes Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192.16.1.0/24 and the remote quick mode selector is 192.16.2.0/24. How must the administrator configure the local quick mode selector for site B?
A. 192.168.3.0/24
B. 192.168.2.0/24
C. 192.168.1.0/24
D. 192.168.0.0/8
-
Question 67:
Examine this FortiGate configuration:
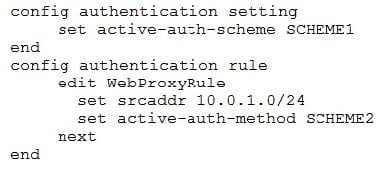
How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
A. It always authorizes the traffic without requiring authentication.
B. It drops the traffic.
C. It authenticates the traffic using the authentication scheme SCHEME2.
D. It authenticates the traffic using the authentication scheme SCHEME1.
-
Question 68:
Refer to the exhibit.
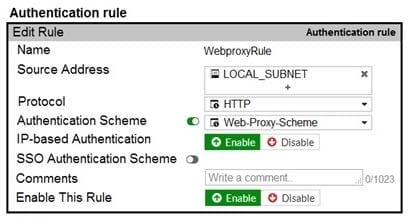
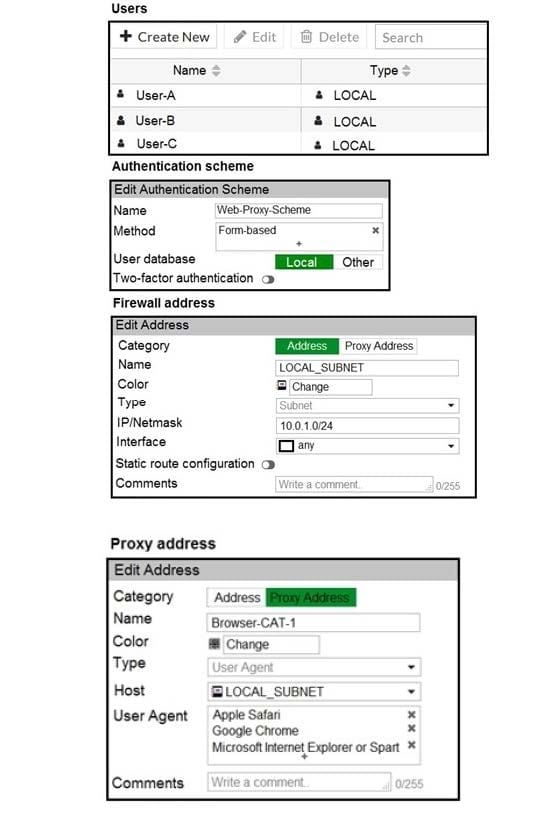
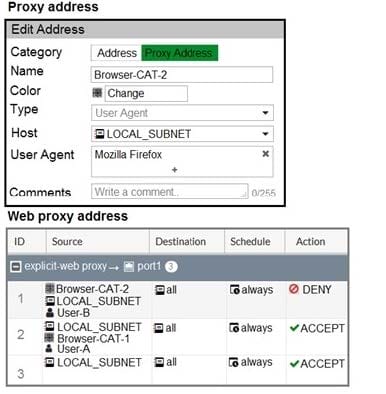
The exhibit shows proxy policies and proxy addresses, the authentication rule and authentication scheme, users, and firewall address.
An explicit web proxy is configured for subnet range 10.0.1.0/24 with three explicit web proxy policies. The authentication rule is configured to authenticate HTTP requests for subnet range 10.0.1.0/24 with a form-based authentication scheme for the FortiGate local user database.
Users will be prompted for authentication.
How will FortiGate process the traffic when the HTTP request comes from a machine with the source IP
10.0.1.10 to the destination http://www.fortinet.com? (Choose two.)
A. If a Mozilla Firefox browser is used with User-B credentials, the HTTP request will be allowed.
B. If a Google Chrome browser is used with User-B credentials, the HTTP request will be allowed.
C. If a Mozilla Firefox browser is used with User-A credentials, the HTTP request will be allowed.
D. If a Microsoft Internet Explorer browser is used with User-B credentials, the HTTP request will be allowed.
-
Question 69:
Which three methods are used by the collector agent for AD polling? (Choose three.)
A. FortiGate polling
B. NetAPI
C. Novell API
D. WMI
E. WinSecLog
-
Question 70:
Which two statements are true about collector agent advanced mode? (Choose two.)
A. Advanced mode uses Windows convention--NetBios: Domain\Username.
B. FortiGate can be configured as an LDAP client and group filters can be configured on FortiGate
C. Advanced mode supports nested or inherited groups
D. Security profiles can be applied only to user groups, not individual users.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4_FGT-7.0 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.