Exam Details
Exam Code
:NSE4_FGT-6.4Exam Name
:Fortinet NSE 4 - FortiOS 6.4Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:163 Q&AsLast Updated
:Aug 07, 2025
Fortinet Fortinet Certifications NSE4_FGT-6.4 Questions & Answers
-
Question 61:
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
A. FortiGate automatically negotiates different local and remote addresses with the remote peer.
B. FortiGate automatically negotiates a new security association after the existing security association expires.
C. FortiGate automatically negotiates different encryption and authentication algorithms with the remote peer.
D. FortiGate automatically brings up the IPsec tunnel and keeps it up, regardless of activity on the IPsec tunnel.
-
Question 62:
Refer to the exhibit.
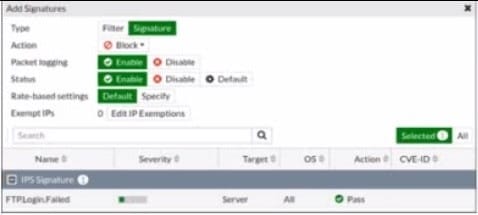
Review the Intrusion Prevention System (IPS) profile signature settings. Which statement is correct in adding the FTP.Login.Failed signature to the IPS sensor profile?
A. The signature setting uses a custom rating threshold.
B. The signature setting includes a group of other signatures.
C. Traffic matching the signature will be allowed and logged.
D. Traffic matching the signature will be silently dropped and logged.
-
Question 63:
An administrator has configured two-factor authentication to strengthen SSL VPN access. Which additional best practice can an administrator implement?
A. Configure Source IP Pools.
B. Configure split tunneling in tunnel mode.
C. Configure different SSL VPN realms.
D. Configure host check.
-
Question 64:
Refer to the exhibit, which contains a radius server configuration.
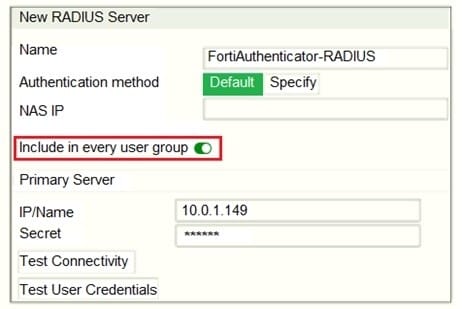
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option. What will be the impact of using Include in every user group option in a RADIUS configuration?
A. This option places the RADIUS server, and all users who can authenticate against that server, into every FortiGate user group.
B. This option places all FortiGate users and groups required to authenticate into the RADIUS server, which, in this case, is FortiAuthenticator.
C. This option places all users into every RADIUS user group, including groups that are used for the LDAP server on FortiGate.
D. This option places the RADIUS server, and all users who can authenticate against that server, into every RADIUS group.
-
Question 65:
Which two attributes are required on a certificate so it can be used as a CA certificate on SSL Inspection? (Choose two.)
A. The keyUsage extension must be set to keyCertSign.
B. The common name on the subject field must use a wildcard name.
C. The issuer must be a public CA.
D. The CA extension must be set to TRUE.
-
Question 66:
Which two statements are correct regarding FortiGate FSSO agentless polling mode? (Choose two.)
A. FortiGate points the collector agent to use a remote LDAP server.
B. FortiGate uses the AD server as the collector agent.
C. FortiGate uses the SMB protocol to read the event viewer logs from the DCs.
D. FortiGate queries AD by using the LDAP to retrieve user group information.
-
Question 67:
Refer to the exhibit.
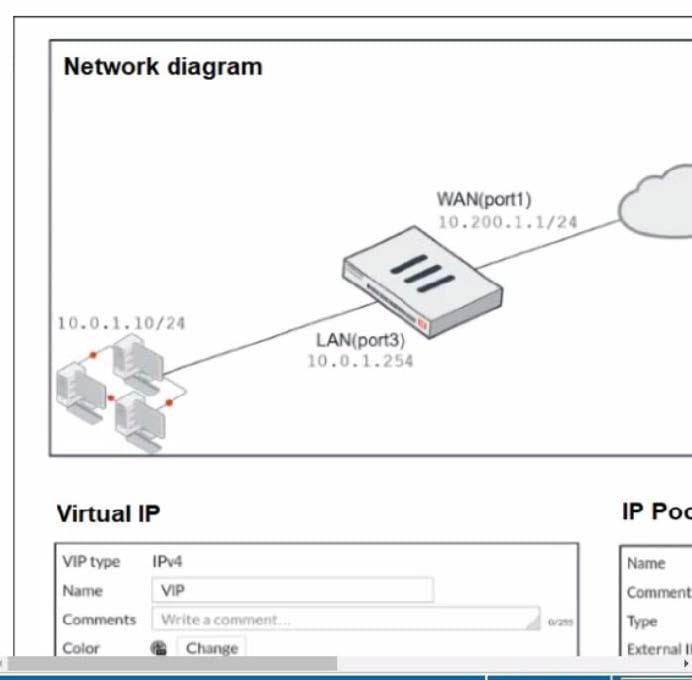
The exhibit contains a network diagram, virtual IP, IP pool, and firewall policies configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port3) interface has the IP address
10 .0.1.254. /24.
The first firewall policy has NAT enabled using IP Pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the internet traffic coming from a workstation with the IP
address 10.0.1.10?
A. 10.200.1.1
B. 10.200.3.1
C. 10.200.1.100
D. 10.200.1.10
-
Question 68:
Refer to the exhibit to view the application control profile.
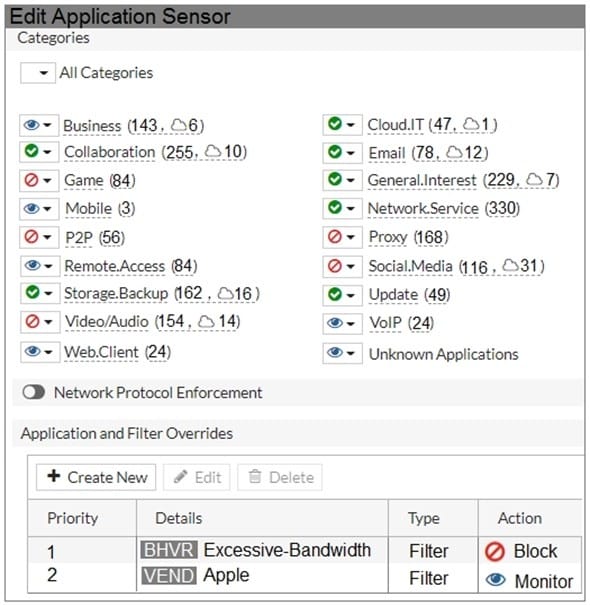
Users who use Apple FaceTime video conferences are unable to set up meetings. In this scenario, which statement is true?
A. Apple FaceTime belongs to the custom monitored filter.
B. The category of Apple FaceTime is being monitored.
C. Apple FaceTime belongs to the custom blocked filter.
D. The category of Apple FaceTime is being blocked.
-
Question 69:
Refer to the exhibit.
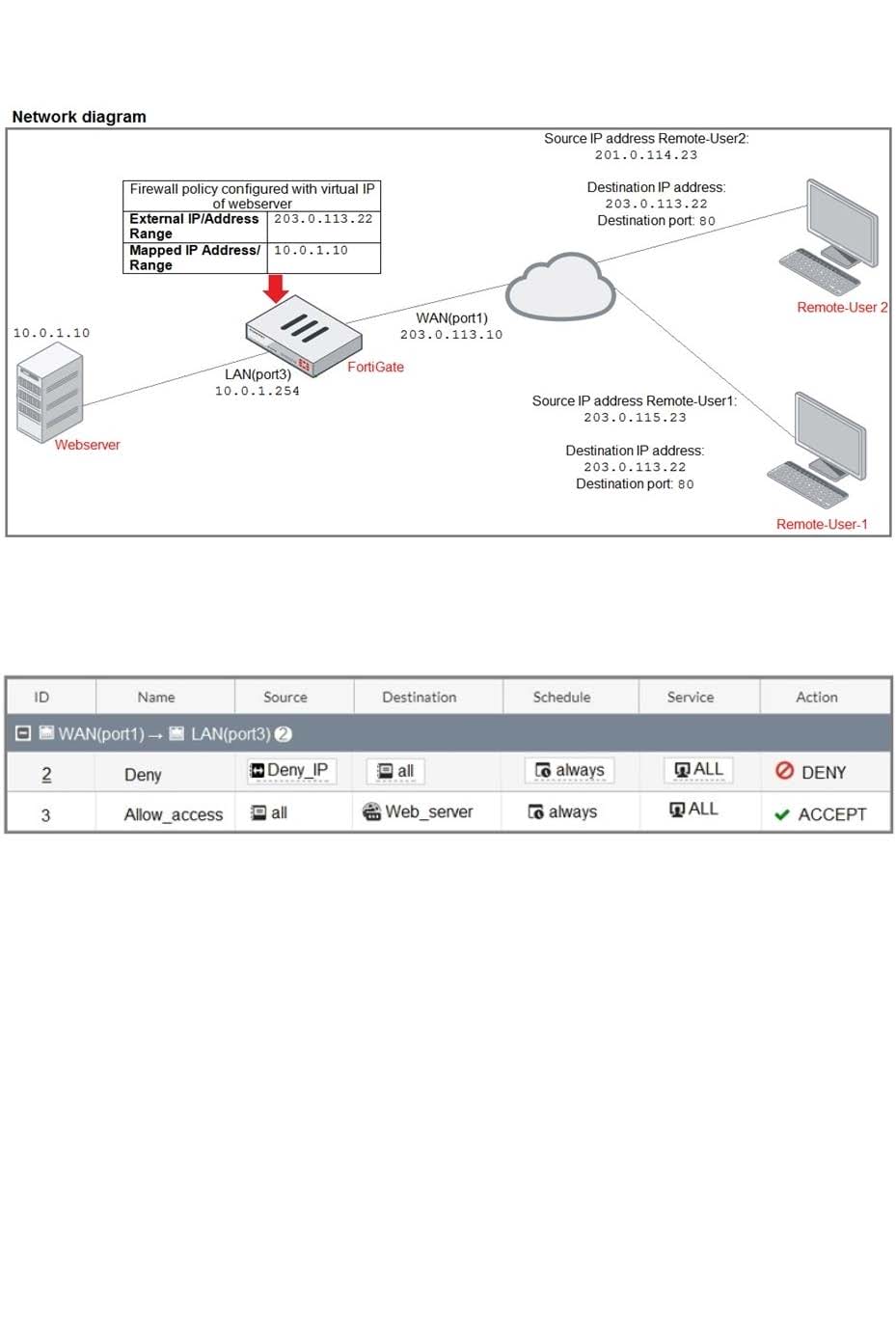
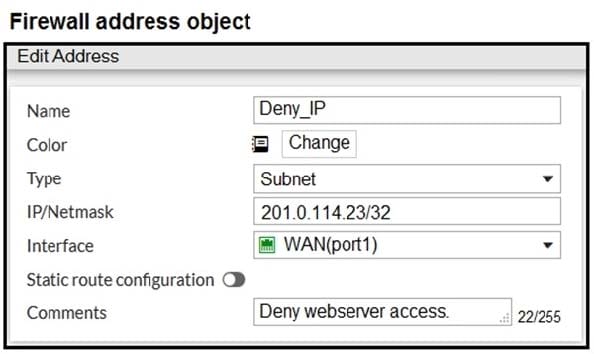
The exhibit contains a network diagram, firewall policies, and a firewall address object configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-user2. Remote-user2 is still able to access Webserver.
Which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose two.)
A. Disable match-vip in the Deny policy.
B. Set the Destination address as Deny_IP in the Allow-access policy.
C. Enable match vip in the Deny policy.
D. Set the Destination address as Web_server in the Deny policy.
-
Question 70:
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
A. SSH
B. HTTPS
C. FTM
D. FortiTelemetry
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4_FGT-6.4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.