Exam Details
Exam Code
:NSE4_FGT-6.4Exam Name
:Fortinet NSE 4 - FortiOS 6.4Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:163 Q&AsLast Updated
:Aug 07, 2025
Fortinet Fortinet Certifications NSE4_FGT-6.4 Questions & Answers
-
Question 121:
Examine this FortiGate configuration:

Examine the output of the following debug command:

Based on the diagnostic outputs above, how is the FortiGate handling the traffic for new sessions that require inspection?
A. It is allowed, but with no inspection
B. It is allowed and inspected as long as the inspection is flow based
C. It is dropped.
D. It is allowed and inspected, as long as the only inspection required is antivirus.
-
Question 122:
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).
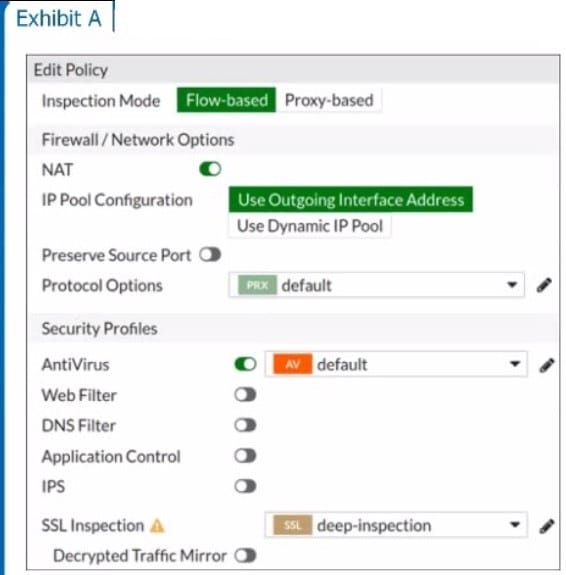
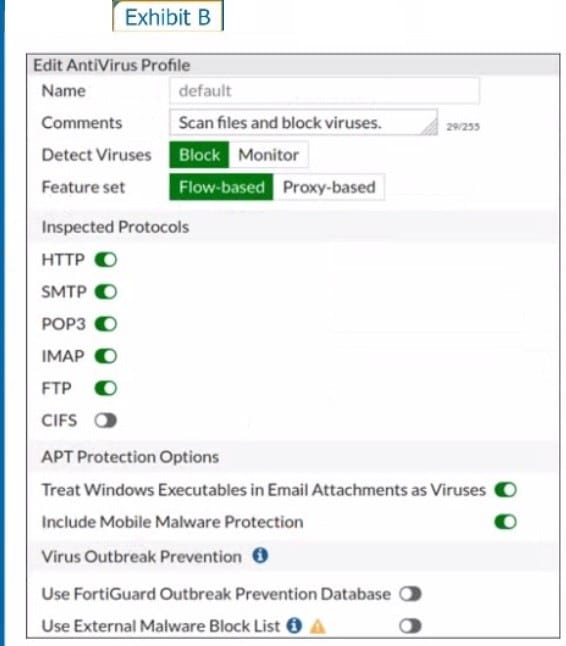
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
A. The firewall policy performs the full content inspection on the file.
B. The flow-based inspection is used, which resets the last packet to the user.
C. The volume of traffic being inspected is too high for this model of FortiGate.
D. The intrusion prevention security profile needs to be enabled when using flow-based inspection mode.
-
Question 123:
Refer to the exhibit.
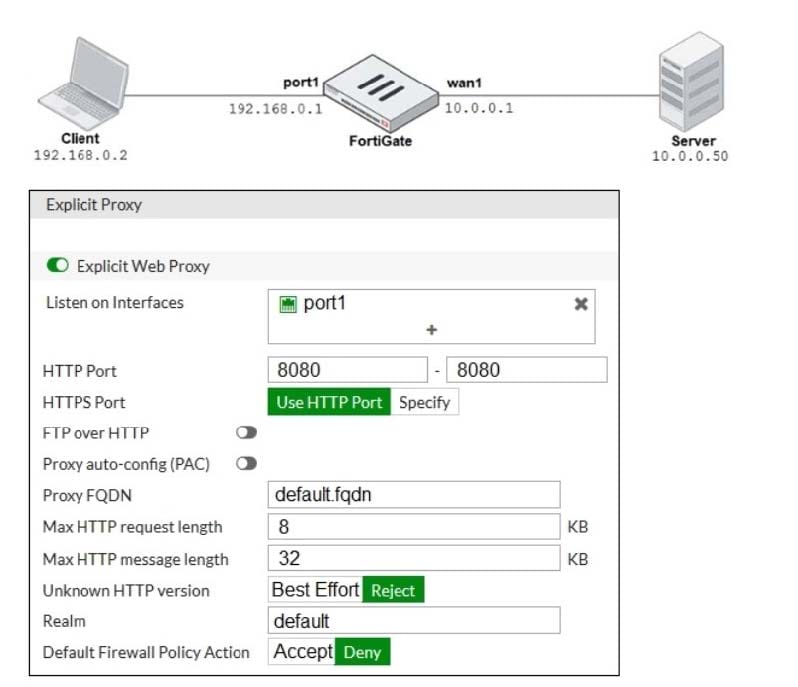
The exhibits show a network diagram and the explicit web proxy configuration.
In the command diagnose sniffer packet, what filter can you use to capture the traffic between the client and the explicit web proxy?
A. `host 192.168.0.2 and port 8080'
B. `host 10.0.0.50 and port 80'
C. `host 192.168.0.1 and port 80'
D. `host 10.0.0.50 and port 8080'
-
Question 124:
FortiGate is configured as a policy-based next-generation firewall (NGFW) and is applying web filtering and application control directly on the security policy.
Which two other security profiles can you apply to the security policy? (Choose two.)
A. Antivirus scanning
B. File filter
C. DNS filter
D. Intrusion prevention
-
Question 125:
Refer to the exhibit.
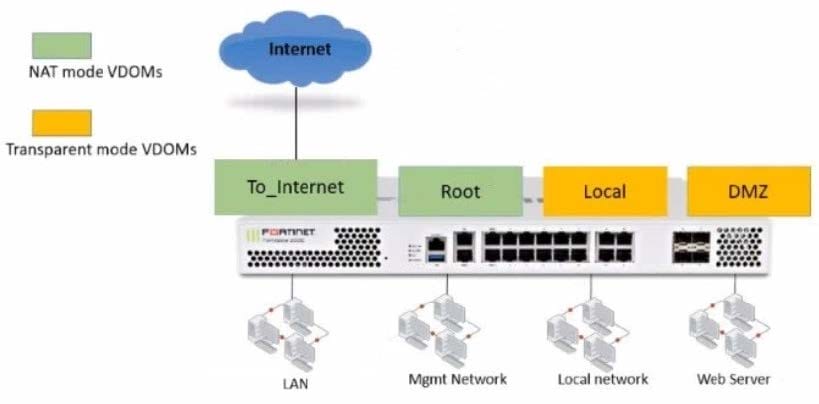
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the Internet. The To_Internet VDOM is the only VDOM with internet access and is directly connected to ISP modem.
Which two statements are true? (Choose two.)
A. Inter-VDOM links are required to allow traffic between the Local and Root VDOMs.
B. A static route is required on the To_Internet VDOM to allow LAN users to access the internet.
C. Inter-VDOM links are required to allow traffic between the Local and DMZ VDOMs.
D. Inter-VDOM links are not required between the Root and To_Internet VDOMs because the Root VDOM is used only as a management VDOM.
-
Question 126:
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
A. The firmware image must be manually uploaded to each FortiGate.
B. Only secondary FortiGate devices are rebooted.
C. Uninterruptable upgrade is enabled by default.
D. Traffic load balancing is temporally disabled while upgrading the firmware.
-
Question 127:
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
A. To detect intermediary NAT devices in the tunnel path.
B. To dynamically change phase 1 negotiation mode aggressive mode.
C. To encapsulation ESP packets in UDP packets using port 4500.
D. To force a new DH exchange with each phase 2 rekey.
-
Question 128:
Refer to the exhibit, which contains a static route configuration.
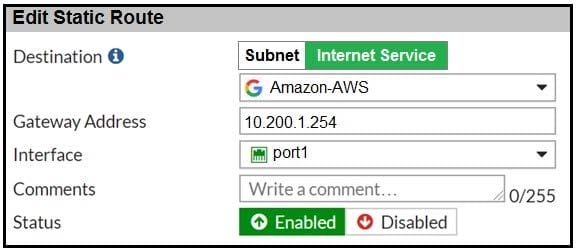
An administrator created a static route for Amazon Web Services. What CLI command must the administrator use to view the route?
A. get router info routing-table all
B. get internet service route list
C. get router info routing-table database
D. diagnose firewall proute list
-
Question 129:
Which two statements are correct about a software switch on FortiGate? (Choose two.)
A. It can be configured only when FortiGate is operating in NAT mode
B. Can act as a Layer 2 switch as well as a Layer 3 router
C. All interfaces in the software switch share the same IP address
D. It can group only physical interfaces
-
Question 130:
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
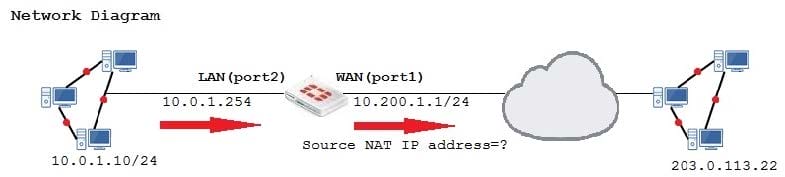

The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address 10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0.1.10/24?
A. 10.200.1.10
B. Any available IP address in the WAN (port1) subnet 10.200.1.0/24
C. 10.200.1.1
D. 10.0.1.254
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4_FGT-6.4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.