Exam Details
Exam Code
:NSE4_FGT-6.4Exam Name
:Fortinet NSE 4 - FortiOS 6.4Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:163 Q&AsLast Updated
:Aug 07, 2025
Fortinet Fortinet Certifications NSE4_FGT-6.4 Questions & Answers
-
Question 91:
Refer to the exhibit.
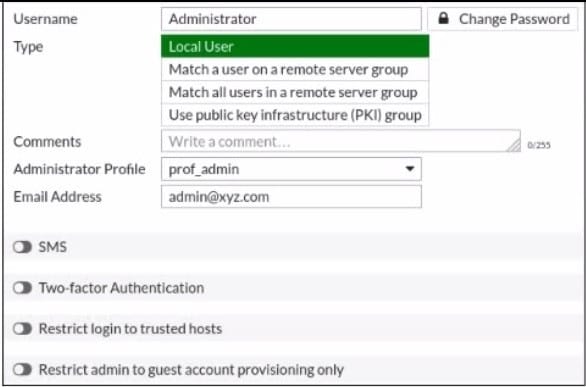
The global settings on a FortiGate device must be changed to align with company security policies. What does the Administrator account need to access the FortiGate global settings?
A. Change password
B. Enable restrict access to trusted hosts
C. Change Administrator profile
D. Enable two-factor authentication
-
Question 92:
An administrator has configured a route-based IPsec VPN between two FortiGate devices. Which statement about this IPsec VPN configuration is true?
A. A phase 2 configuration is not required.
B. This VPN cannot be used as part of a hub-and-spoke topology.
C. A virtual IPsec interface is automatically created after the phase 1 configuration is completed.
D. The IPsec firewall policies must be placed at the top of the list.
-
Question 93:
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
A. A CRL
B. A person
C. A subordinate CA
D. A root CA
-
Question 94:
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
A. The collector agent uses a Windows API to query DCs for user logins.
B. NetAPI polling can increase bandwidth usage in large networks.
C. The collector agent must search security event logs.
D. The NetSession Enum function is used to track user logouts.
-
Question 95:
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?
A. Antivirus engine
B. Intrusion prevention system engine
C. Flow engine
D. Detection engine
-
Question 96:
Refer to the exhibit.
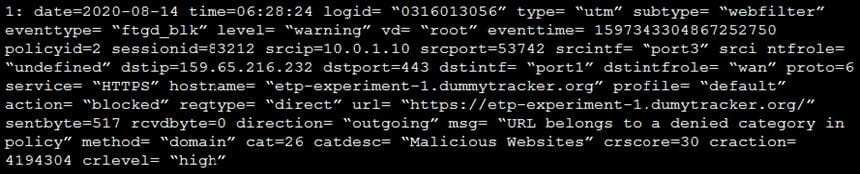
Based on the raw log, which two statements are correct? (Choose two.)
A. Traffic is blocked because Action is set to DENY in the firewall policy.
B. Traffic belongs to the root VDOM.
C. This is a security log.
D. Log severity is set to error on FortiGate.
-
Question 97:
Which of the following are valid actions for FortiGuard category based filter in a web filter profile ui proxy-based inspection mode? (Choose two.)
A. Warning
B. Exempt
C. Allow
D. Learn
-
Question 98:
Which security feature does FortiGate provide to protect servers located in the internal networks from attacks such as SQL injections?
A. Denial of Service
B. Web application firewall
C. Antivirus
D. Application control
-
Question 99:
Which three authentication timeout types are availability for selection on FortiGate? (Choose three.)
A. hard-timeout
B. auth-on-demand
C. soft-timeout
D. new-session
E. Idle-timeout
-
Question 100:
Refer to the exhibits.
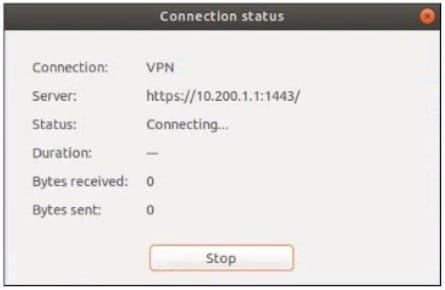
The SSL VPN connection fails when a user attempts to connect to it. What should the user do to successfully connect to SSL VPN?
A. Change the SSL VPN port on the client.
B. Change the Server IP address.
C. Change the idle-timeout.
D. Change the SSL VPN portal to the tunnel.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4_FGT-6.4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.