Exam Details
Exam Code
:NSE4Exam Name
:Fortinet Network Security Expert 4 Written Exam (400)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:301 Q&AsLast Updated
:Apr 21, 2024
Fortinet Fortinet Certifications NSE4 Questions & Answers
-
Question 181:
Which statement is in advantage of using a hub and spoke IPsec VPN configuration instead of a fully-meshed set of IPsec tunnels?
A. Using a hub and spoke topology provides full redundancy.
B. Using a hub and spoke topology requires fewer tunnels.
C. Using a hub and spoke topology uses stronger encryption protocols.
D. Using a hub and spoke topology requires more routes.
-
Question 182:
A FortiGate device is configure to perform an AV and IPS scheduled update every hour.
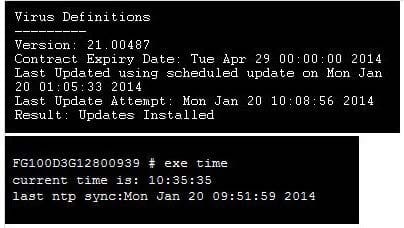
Given the information in the exhibit, when will the next update happen?
A. 01:00
B. 02:05
C. 11:00
D. 11:08
-
Question 183:
On your FortiGate 60D, you've configured firewall policies. They port forward traffic to your Linux Apache web server. Select the best way to protect your web server by using the IPS engine.
A. Enable IPS signatures for Linux servers with HTTP, TCP and SSL protocols and Apache applications. Configured DLP to block HTTP GET request with credit card numbers.
B. Enable IPS signatures for Linux servers with HTTP, TCP and SSL protocols and Apache applications. Configure DLP to block HTTP GET with credit card numbers. Also configure a DoS policy to prevent TCP SYn floods and port scans.
C. None. FortiGate 60D is a desktop model, which does not support IPS.
D. Enable IPS signatures for Linux and windows servers with FTP, HTTP, TCP, and SSL protocols and Apache and PHP applications.
-
Question 184:
Which of the following statements are true regarding DLP File Type Filtering? (Choose two.)
A. Filters based on file extension
B. Filters based on fingerprints
C. Filters based on file content
D. File types are hard coded in the FortiOS
-
Question 185:
What is longest length of time allowed on a FortiGate device for the virus scan to complete?
A. 20 seconds
B. 30 seconds
C. 45 seconds
D. 10 seconds
-
Question 186:
What are required to be the same for two FortiGate units to form an HA cluster? (Choose two)
A. Firmware.
B. Model.
C. Hostname.
D. System time zone.
-
Question 187:
What are the requirements for a HA cluster to maintain TCP connections after device or link failover? (Choose two.)
A. Enable session pick-up.
B. Enable override.
C. Connections must be UDP or ICMP.
D. Connections must not be handled by a proxy.
-
Question 188:
Which are the three different types of Conserve Mode that can occur on a FortiGate device? (Choose three.)
A. Proxy
B. Operating system
C. Kernel
D. System
E. Device
-
Question 189:
Which statement is correct regarding virus scanning on a FortiGate unit?
A. Virus scanning is enabled by default.
B. Fortinet customer support enables virus scanning remotely for you.
C. Virus scanning must be enabled in a security profile, which must be applied to a firewall policy.
D. Enabling virus scanning in a UTM security profile enables virus scanning for all traffic flowing through the FortiGate device.
-
Question 190:
Which of the following actions that can be taken by the Data Leak Prevention scanning? (Choose three.)
A. Block
B. Reject
C. Tag
D. Log only
E. Quarantine IP address
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.