Exam Details
Exam Code
:NSE4-5.4Exam Name
:Fortinet Network Security Expert 4 Written Exam - FortiOS 5.4Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:576 Q&AsLast Updated
:Dec 30, 2024
Fortinet Fortinet Certifications NSE4-5.4 Questions & Answers
-
Question 61:
How can a browser trust a web-server certificate signed by a third party CA?
A. The browser must have the CA certificate that signed the web-server certificate installed.
B. The browser must have the web-server certificate installed.
C. The browser must have the private key of CA certificate that signed the web-browser certificate installed.
D. The browser must have the public key of the web-server certificate installed.
-
Question 62:
How does FortiGate verify the login credentials of a remote LDAP user?
A. FortiGate sends the user entered credentials to the LDAP server for authentication.
B. FortiGate re-generates the algorithm based on the login credentials and compares it against the algorithm stored on the LDAP server.
C. FortiGate queries its own database for credentials.
D. FortiGate queries the LDAP server for credentials.
-
Question 63:
Which of the following settings and protocols can be used to provide secure and restrictive administrative access to FortiGate? (Choose three.)
A. Trusted host
B. HTTPS
C. Trusted authentication
D. SSH
E. FortiTelemetry
-
Question 64:
Which statement about the firewall policy authentication timeout is true?
A. It is a hard timeout. The FortiGate removes the temporary policy for a user's source IP address after this times expires.
B. It is a hard timeout. The FortiGate removes the temporary policy for a user's source MAC address after this times expires.
C. It is an idle timeout. The FortiGate considers a user to be idle if it does not see any packets coming from the user's source MAC address.
D. It is an idle timeout. The FortiGate considers a user to be idle if it does not see any packets coming from the user's source IP.
-
Question 65:
Which statements best describe auto discovery VPN (ADVPN). (Choose two.)
A. It requires the use of dynamic routing protocols so that spokes can learn the routes to other spokes.
B. ADVPN is only supported with IKEv2.
C. Tunnels are negotiated dynamically between spokes.
D. Every spoke requires a static tunnel to be configured to other spokes so that phase 1 and phase 2 proposals are defined in advance.
-
Question 66:
View the exhibit.
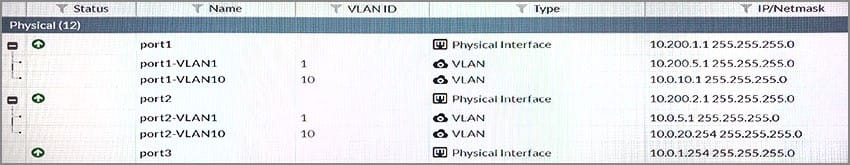
Which statements about the exhibit are true? (Choose two.)
A. port1-VLAN10 and port2-VLAN10 can be assigned to different VDOMs.
B. port1-VLAN1 is the native VLAN for the port1 physical interface.
C. Traffic between port1-VLAN1 and port2-VLAN1 is allowed by default.
D. Broadcast traffic received in port1-VLAN10 will not be forwarded to port2-VLAN10.
-
Question 67:
What FortiGate feature can be used to allow IPv6 clients to connect to IPv4 servers?
A. IPv6-over-IPv4 IPsec
B. NAT64
C. IPv4-over-IPv6 IPsec
D. NAT66
-
Question 68:
Which of the following statements about NTLM authentication are correct? (Choose two.)
A. It is useful when users log in to DCs that are not monitored by a collector agent.
B. It takes over as the primary authentication method when configured alongside FSSO.
C. Multi-domain environments require DC agents on every domain controller.
D. NTLM-enabled web browsers are required.
-
Question 69:
What are the purposes of NAT traversal in IPsec? (Choose two.)
A. To detect intermediary NAT devices in the tunnel path.
B. To encapsulate ESP packets in UDP packets using port 4500.
C. To force a new DH exchange with each phase 2 re-key
D. To dynamically change phase 1 negotiation mode to Aggressive.
-
Question 70:
Which statements about application control are true? (Choose two.)
A. Enabling application control profile in a security profile enables application control for all the traffic flowing through the FortiGate.
B. It cannot take an action on unknown applications.
C. It can inspect encrypted traffic.
D. It can identify traffic from known applications, even when they are using non-standard TCP/UDP ports.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4-5.4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.