Exam Details
Exam Code
:NSE4-5.4Exam Name
:Fortinet Network Security Expert 4 Written Exam - FortiOS 5.4Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:576 Q&AsLast Updated
:Dec 30, 2024
Fortinet Fortinet Certifications NSE4-5.4 Questions & Answers
-
Question 551:
Which statement is correct concerning creating a custom signature?
A. It must start with the name
B. It must indicate whether the traffic flow is from the client or the server.
C. It must specify the protocol. Otherwise, it could accidentally match lower-layer protocols.
D. It is not supported by Fortinet Technical Support.
-
Question 552:
Which operating system vulnerability can you protect when selecting signatures to include in an IPS sensor? (Choose three)
A. Irix
B. QNIX
C. Linux
D. Mac OS
E. BSD
-
Question 553:
Which of the following statements best describes the role of a DC agents in an FSSO DC?
A. Captures the login events and forward them to the collector agent.
B. Captures the user IP address and workstation name and forward that information to the FortiGate devices.
C. Captures the login and logoff events and forward them to the collector agent.
D. Captures the login events and forward them to the FortiGate devices.
-
Question 554:
An Internet browser is using the WPAD DNS method to discover the PAC file's URL. The DNS server replies to the browser's request with the IP address 10.100.1.10. Which URL will the browser use to download the PAC file?
A. http://10.100.1.10/proxy.pac
B. https://10.100.1.10/
C. http://10.100.1.10/wpad.dat
D. https://10.100.1.10/proxy.pac
-
Question 555:
Which of the following IPsec configuration modes can be used for implementing L2TP- over- IPSec VPNs?
A. Policy-based IPsec only.
B. Route-based IPsec only.
C. Both policy-based and route-based VPN.
D. L2TP-over-IPSec is not supported by FortiGate devices.
-
Question 556:
Which of the following statements describe some of the differences between symmetric and asymmetric cryptography? (Choose two.)
A. In symmetric cryptography, the keys are publicly available. In asymmetric cryptography, the keys must be kept secret.
B. Asymmetric cryptography can encrypt data faster than symmetric cryptography
C. Symmetric cryptography uses one pre-shared key. Asymmetric cryptography uses a pair or keys
D. Asymmetric keys can be sent to the remote peer via digital certificates. Symmetric keys cannot
-
Question 557:
A FortiGate device is configure to perform an AV and IPS scheduled update every hour.
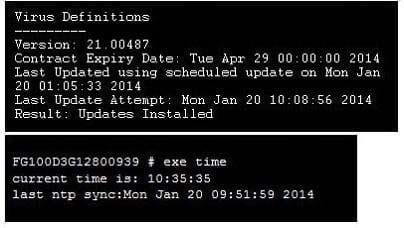
Given the information in the exhibit, when will the next update happen?
A. 01:00
B. 02:05
C. 11:00
D. 11:08
-
Question 558:
Which of the following statements are true about the SSL Proxy certificate that must be used for SSL Content Inspection? (Choose two.)
A. It cannot be signed by a private CA
B. It must have either the field "CA=True" or the filed "Key Usage=KeyCertSign"
C. It must be installed in the FortiGate device
D. The subject filed must contain either the FQDN, or the IP address of the FortiGate device
-
Question 559:
A FortiGate is configured to receive push updates from the FortiGuard Distribution Network, however, they are not being received.
Which is one reason for this problem?
A. The FortiGate is connected to multiple ISPs.
B. FortiGuard scheduled updates are enabled in the FortiGate configuration.
C. The FortiGate is in Transparent mode.
D. The external facing interface of the FortiGate is configured to get the IP address from a DHCP server.
-
Question 560:
Which best describe the mechanism of a TCP SYN flood?
A. The attacker keeps open many connections with slow data transmission so that other clients cannot start new connections.
B. The attacker sends a packet designed to "sync" with the FortiGate.
C. The attacker sends a specially crafted malformed packet, intended to crash the target by exploiting its parser.
D. The attacker starts many connections, but never acknowledges to fully form them.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4-5.4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.