Exam Details
Exam Code
:NSE4-5.4Exam Name
:Fortinet Network Security Expert 4 Written Exam - FortiOS 5.4Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:576 Q&AsLast Updated
:Dec 30, 2024
Fortinet Fortinet Certifications NSE4-5.4 Questions & Answers
-
Question 391:
Which of the following statements are correct regarding URL Filtering on the FortiGate unit? (Select all that apply.)
A. The allowed actions for URL Filtering include Allow, Block and Exempt.
B. The allowed actions for URL Filtering are Allow and Block.
C. The FortiGate unit can filter URLs based on patterns using text and regular expressions.
D. Any URL accessible by a web browser can be blocked using URL Filtering.
E. Multiple URL Filter lists can be added to a single protection profile.
-
Question 392:
An administrator is configuring a DLP rule for FTP traffic. When adding the rule to a DLP sensor,
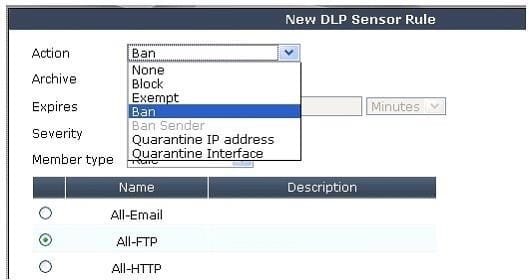
the administrator notes that the Ban Sender action is not available (greyed-out), as shown in the exhibit. Which of the following is the best explanation for the Ban Sender action NOT being available?
A. The Ban Sender action is never available for FTP traffic.
B. The Ban Sender action needs to be enabled globally for FTP traffic on the FortiGate unit before configuring the sensor.
C. Firewall policy authentication is required before the Ban Sender action becomes available.
D. The Ban Sender action is only available for known domains. No domains have yet been added to the domain list.
-
Question 393:
The following diagnostic output is displayed in the CLI:
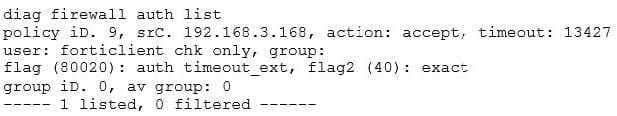
Based on this output, which of the following statements is correct?
A. Firewall policy 9 has endpoint compliance enabled but not firewall authentication.
B. The client check that is part of an SSL VPN connection attempt failed.
C. This user has been associated with a guest profile as evidenced by the group id of 0.
D. An auth-keepalive value has been enabled.
-
Question 394:
An administrator is examining the attack logs and notices the following entry:
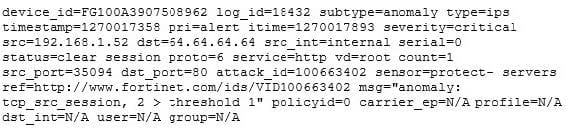
Based solely upon this log message, which of the following statements is correct?
A. This attack was blocked by the HTTP protocol decoder.
B. This attack was caught by the DoS sensor "protect-servers".
C. This attack was launched against the FortiGate unit itself rather than a host behind the FortiGate unit.
D. The number of concurrent connections to destination IP address 64.64.64.64 has exceeded the configured threshold.
-
Question 395:
In a High Availability configuration operating in Active-Active mode, which of the following correctly describes the path taken by a load-balanced HTTP session?
A. Request: Internal Host -> Master FG -> Slave FG -> Internet -> Web Server
B. Request: Internal Host -> Master FG -> Slave FG -> Master FG -> Internet -> Web Server
C. Request: Internal Host -> Slave FG -> Internet -> Web Server
D. Request: Internal Host -> Slave FG -> Master FG -> Internet -> Web Server
-
Question 396:
An organization wishes to protect its SIP Server from call flooding attacks. Which of the following configuration changes can be performed on the FortiGate unit to fulfill this requirement?
A. Apply an application control list which contains a rule for SIP and has the "Limit INVITE Request" option configured.
B. Enable Traffic Shaping for the appropriate SIP firewall policy.
C. Reduce the session time-to-live value for the SIP protocol by running the configure system session-ttl CLI command.
D. Run the set udp-idle-timer CLI command and set a lower time value.
-
Question 397:
What advantages are there in using a fully Meshed IPSec VPN configuration instead of a hub and spoke set of IPSec tunnels?
A. Using a hub and spoke topology is required to achieve full redundancy.
B. Using a full mesh topology simplifies configuration.
C. Using a full mesh topology provides stronger encryption.
D. Full mesh topology is the most fault-tolerant configuration.
-
Question 398:
An administrator wishes to generate a report showing Top Traffic by service type, but wants to exclude SMTP traffic from the report. Which of the following statements best describes how to do this?
A. In the Service field of the Data Filter, type 25/smtp and select the NOT checkbox.
B. Add the following entry to the Generic Field section of the Data Filter: service="!smtp".
C. When editing the chart, uncheck mlog to indicate that Mail Filtering data is being excluded when generating the chart.
D. When editing the chart, enter 'dns' in the Exclude Service field.
-
Question 399:
Which of the following statements is correct regarding the NAC Quarantine feature?
A. With NAC quarantine, files can be quarantined not only as a result of antivirus scanning, but also for other forms of content inspection such as IPS and DLP.
B. NAC quarantine does a client check on workstations before they are permitted to have administrative access to FortiGate.
C. NAC quarantine allows administrators to isolate clients whose network activity poses a security risk.
D. If you chose the quarantine action, you must decide whether the quarantine type is NAC quarantine or File quarantine.
-
Question 400:
Which of the following statements is correct based on the firewall configuration illustrated in the exhibit?
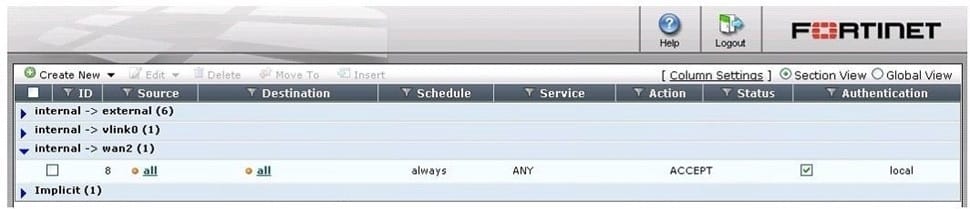
A. A user can access the Internet using only the protocols that are supported by user authentication.
B. A user can access the Internet using any protocol except HTTP, HTTPS, Telnet, and FTP. These require authentication before the user will be allowed access.
C. A user must authenticate using the HTTP, HTTPS, SSH, FTP, or Telnet protocol before they can access any services.
D. A user cannot access the Internet using any protocols unless the user has passed firewall authentication.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4-5.4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.