Exam Details
Exam Code
:N10-008Exam Name
:CompTIA Network+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1219 Q&AsLast Updated
:Feb 16, 2025
CompTIA CompTIA Certifications N10-008 Questions & Answers
-
Question 611:
While waking from the parking lot lo an access-controlled door an employee sees an authorized user open the door. Then the employee notices that another person catches the door before It closes and goes inside.
Which of the following attacks Is taking place?
A. Tailgating
B. Pipgybacking
C. Shoulder surfing
D. Phisning
-
Question 612:
A technician is contracted to install a redundant cluster of devices from the ISP In case of a hardware failure within the network. Which of the following would provide the BEST redundant solution in Layer 2 devices?
A. Multiple routers
B. Multiple switches
C. Multiple firewalls
D. Multiple budges
-
Question 613:
Which of the following is MOST appropriate for enforcing bandwidth limits when the performance of an application is not affected by the use of buffering but is heavily impacted by packet drops?
A. Traffic shaping
B. Traffic policing
C. Traffic marking
D. Traffic classification
-
Question 614:
At which of the following OSI model layers does routing occur?
A. Data link
B. Transport
C. Physical
D. Network
-
Question 615:
During a recent security audit, a contracted penetration tester discovered the organization uses a number of insecure protocols. Which of the following ports should be disallowed so only encrypted protocols are allowed? (Select TWO).
A. 22
B. 23
C. 69
D. 443
E. 587
F. 8080
-
Question 616:
Users in a branch can access an ln-house database server, but II is taking too long to fetch records. The analyst does not know whether the Issue is being caused by network latency. Which of the following will the analyst MOST likely use to retrieve the metrics that are needed to resolve this issue?
A. SNMP
B. Link state
C. Syslog
D. QoS
E. Traffic shaping
-
Question 617:
Which of the following documents would be used to define uptime commitments from a provider, along with details on measurement and enforcement?
A. NDA
B. SLA
C. MOU
D. AUP
-
Question 618:
A network administrator is decommissioning a server. Which of the following will the network administrator MOST likely consult?
A. Onboarding and off boarding policies
B. Business continuity plan
C. Password requirements
D. Change management documentation
-
Question 619:
A network engineer needs to create a subnet that has the capacity for five VLANs. with the following number of clients lo be allowed on each:
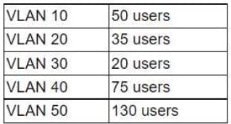
Which of the following is the SMALLEST subnet capable of this setup that also has the capacity to double the number of clients in the future?
A. 10.0.0.0/21
B. 10.0.0.0/22
C. 10.0.0.0/23
D. 10.0.0.0/24
-
Question 620:
A company rents out a large event space and includes wireless internet access for each tenant. Tenants reserve a two-hour window from the company each week, which includes a tenant-specific SSID. However, all users share the company's network hardware.
The network support team is receiving complaints from tenants that some users are unable to connect to the wireless network. Upon investigation, the support team discovers a pattern indicating that after a tenant with a particularly large attendance ends its sessions, tenants throughout the day are unable to connect.
The following settings are common to all network configurations: Which of the following actions would MOST likely reduce this Issue? (Select TWO).
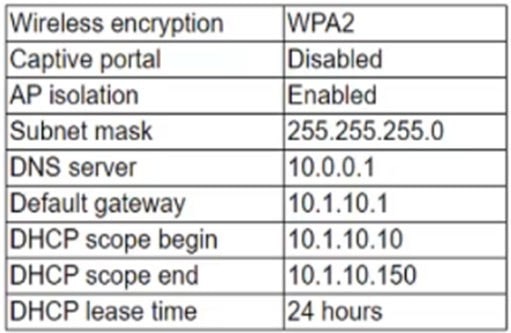
A. Change to WPA encryption
B. Change the DNS server to 10.1.10.1.
C. Change the default gateway to 10.0.0.1.
D. Change the DHCP scope end to 10.1.10.250
E. Disable AP isolation
F. Change the subnet mask lo 255.255.255.192.
G. Reduce the DHCP lease time to four hours.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your N10-008 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.