Exam Details
Exam Code
:N10-008Exam Name
:CompTIA Network+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1219 Q&AsLast Updated
:Feb 16, 2025
CompTIA CompTIA Certifications N10-008 Questions & Answers
-
Question 291:
After a company installed a new IPS, the network is experiencing speed degradation. A network administrator is troubleshooting the issue and runs a speed test. The results from the different network locations are as follows:
Which of the following is the most likely issue?
A. Packet loss
B. Bottlenecking
C. Channel overlap
D. Network congestion
-
Question 292:
While working in a coffee shop, an attacker watches a user log in to a corporate system and writes down the user's log-in credentials. Which of the following social engineering attacks is this an example of?
A. Shoulder surfing
B. Dumpster diving
C. Phishing
D. Tailgating
-
Question 293:
A customer connects a firewall to an ISP router that translates traffic destined for the internet. The customer can connect to the internet but not to the remote site. Which of the following will verify the status of NAT?
A. tcpdump
B. nmap
C. ipconfig
D. tracert
-
Question 294:
A server application requires large amounts of data to be sent at a consistent rate. Which of the following should an engineer most likely configure to meet these requirements?
A. Link speed
B. Jumbo frames
C. Switch Virtual Interface
D. Spanning tree
-
Question 295:
A network technician is troubleshooting an issue that involves connecting to a server via SSH. The server has one network interface that does not support subinterfaces. The technician runs a command on the server and receives the following output:
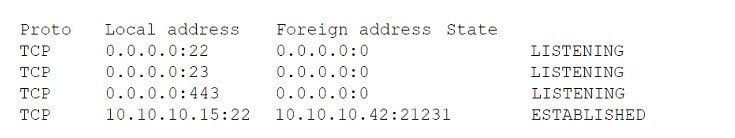
On the host, the technician runs another command and receives the following:
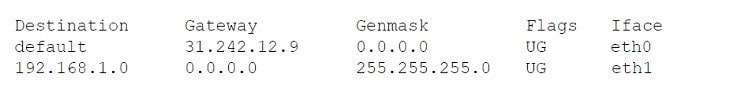
Which of the following best explains the issue?
A. A firewall is blocking access to the server.
B. The server is plugged into a trunk port.
C. The host does not have a route to the server.
D. The server is not running the SSH daemon.
-
Question 296:
A network administrator is deploying a new switch and wants to make sure that the default priority value was set for a spanning tree. Which of the following values would the network administrator expect to see?
A. 4096
B. 8192
C. 32768
D. 36684
-
Question 297:
Which of the following functions is used to prioritize network traffic based on the type of traffic?
A. QoS
B. VPN
C. CDN
D. TTL
-
Question 298:
A network administrator is looking for a solution to extend Layer 2 capabilities and replicate backups between sites. Which of the following is the best solution?
A. Security Service Edge
B. Data center interconnect
C. Infrastructure as code
D. Zero trust architecture
-
Question 299:
Which of the following can be used to identify users after an action has occurred?
A. Access control vestibule
B. Cameras
C. Asset tag
D. Motion detectors
-
Question 300:
A network engineer is interested in using wireless technologies in densely forested areas. Which of the following frequencies would be best for this use?
A. 2.4GHz
B. 5GHz
C. 5.9GHz
D. 6GHz
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your N10-008 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.