Exam Details
Exam Code
:N10-008Exam Name
:CompTIA Network+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1219 Q&AsLast Updated
:Feb 16, 2025
CompTIA CompTIA Certifications N10-008 Questions & Answers
-
Question 221:
Which of the following ports should a network administrator enable for encrypted log-in to a network switch?
A. 22
B. 23
C. 80
D. 123
-
Question 222:
A network security engineer is investigating a potentially malicious Insider on the network. The network security engineer would like to view all traffic coming from the user's PC to the switch without interrupting any traffic or having any downtime. Which of the following should the network security engineer do?
A. Turn on port security.
B. Implement dynamic ARP inspection.
C. Configure 802.1Q.
D. Enable port mirroring.
-
Question 223:
A hacker used a packet sniffer on the network to capture the hardware address of the server. Which of the following types of attacks can the hacker perform now?
A. Piggybacking
B. MAC spoofing
C. Evil twin
D. VLAN hopping
-
Question 224:
A technician is troubleshooting servers with high CPU usage. While trying to connect, the technician needs to open a port for remote access. Which of the following ports should the technician open?
A. 443
B. 3321
C. 8080
D. 5900
-
Question 225:
A support agent receives a report that a remote user's wired devices are constantly disconnecting and have slow speeds. Upon inspection, the support agent sees that the user's coaxial modem has a signal power of -97dB. Which of the following should the support agent recommend to troubleshoot the issue?
A. Removing any splitters connected to the line
B. Switching the devices to wireless
C. Moving the devices closer to the modern
D. Lowering the network speed
-
Question 226:
An application is not working. When the log files are reviewed, the application continuously tries to reach the following destination:
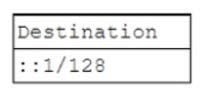
Which of the following is most likely associated with this IP address?
A. APIPA
B. Default gateway
C. Link local
D. Loopback
-
Question 227:
A user reports that the internet seems slow on a workstation, but no other users have reported any issues. The server team confirms the servers are functioning normally. A technician suspects something specific to the user's computer is overutilizing bandwidth. Which of the following commands should the technician use to further investigate the issue?
A. nmap
B. tcpdump
C. netstat
D. nslookup
-
Question 228:
Which of the following most likely determines the size of a rack for installation? (Select two).
A. KVM size
B. Switch depth
C. Hard drive size
D. Cooling fan speed
E. Outlet amperage
F. Server height
-
Question 229:
An administrator wants to host services on the internet using an internal server. The server is configured with an RFC1918 address, and the administrator wants to make the services that are hosted on the server available on one of the company's public IP addresses. Which of the following should the administrator configure to allow this access?
A. IPv6 tunneling
B. Virtual IP
C. Dual stack
D. EUI-64
-
Question 230:
A software developer changed positions within a company and is now a sales engineer. The security team discovered that the former software developer had been modifying code to implement small features requested by customers. Which of the following would be the best thing for the security administrator to implement to prevent this from happening?
A. A software patching policy
B. A role-based access control policy
C. Firewalls on the software development servers
D. Longer and more complex password requirements
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your N10-008 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.