Exam Details
Exam Code
:N10-007Exam Name
:CompTIA Network+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1251 Q&AsLast Updated
:
CompTIA CompTIA Certifications N10-007 Questions & Answers
-
Question 801:
Which of the following are considered physical security detection methods? (Select TWO).
A. Cameras
B. Asset tags
C. Biometric readers
D. Access control vestibules
E. IPS infrastructure
F. Locking racks
-
Question 802:
A technician has completed configuration on a new satellite location. The location has a new firewall and a small internal network. The technician has been asked to perform basic vulnerability testing. Which of the following tools would BEST assist the technician in verifying the security of the site?
A. Packet sniffer
B. Bandwidth tester
C. Port scanner
D. Protocol analyzer
-
Question 803:
Which of the following technologies can be implemented on network devices to increase throughput in network storage systems?
A. Trunking
B. Frame Relay
C. Jumbo frames
D. InfiniBand
-
Question 804:
A user reports a laptop wireless connection is working at the user's desk but not in a recent building addition. A network administrator logs into the wireless controller, searches for the user's MAC address, and receives the following results:
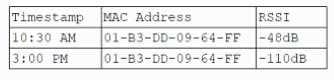
Which of the following describes the reason for the issue?
A. Frequency mismatch
B. Distance limitation
C. Channel overlap
D. Wrong SSID
-
Question 805:
Which of the following protocols would enable a company to upgrade its Internet connection by acquiring its own public IP prefixes and autonomous system number?
A. EIGRP
B. BGP
C. IPv6
D. MPLS
-
Question 806:
A small company decided to use a single virtual appliance lo filter spam as well as a reverse proxy to filter traffic to its internal web server. Which of the following did the company MOST likely deploy?
A. IPS
B. Firewall
C. SIEM
D. UTM
E. Content filler
-
Question 807:
Ann, a user, is attempting to charge her phone using the USB port of her computer. She realizes the port has been disabled. Which of the following policies would restrict the use of the USB port?
A. BYOD
B. NDA
C. SLA
D. AUP
-
Question 808:
A network engineer is provisioning a new Linux server in a public cloud. Which of the following types of cloud service should be utilized?
A. PaaS
B. SaaS
C. DaaS
D. laaS
-
Question 809:
A network administrator installed a WAP to extend the network. However, the company wants to contain the signal so it does not extend beyond the company's parking structure. Which of the following solutions would work BEST?
A. Create MAC filtering.
B. Change the channel.
C. Change the encryption.
D. Install a directional antenna.
-
Question 810:
A network administrator has implemented file integrity monitoring on all relevant devices. This will provide the ability to detect whenever the files are:
A. reinstalled.
B. executed.
C. read.
D. written.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your N10-007 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.