Exam Details
Exam Code
:MS-500Exam Name
:Microsoft 365 Security AdministrationCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:367 Q&AsLast Updated
:Sep 11, 2023
Microsoft Microsoft Certifications MS-500 Questions & Answers
-
Question 41:
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
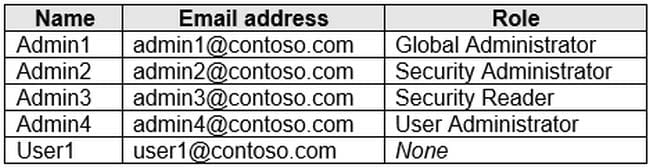
Azure AD Identity Protection detects that the account of User1 is at risk and generates an alert. How many users will receive the alert?
A. 1
B. 2
C. 3
D. 4
-
Question 42:
You have a Microsoft 365 E5 subscription.
Some users are required to use an authenticator app to access Microsoft SharePoint Online.
You need to view which users have used an authenticator app to access SharePoint Online. The solution must minimize costs.
What should you do?
A. From the Azure Active Directory admin center, view the sign-ins.
B. From the Microsoft 365 Security admin center, download a report.
C. From the Enterprise applications blade of the Azure Active Directory admin center, view the audit logs.
D. From the Azure Active Directory admin center, view the authentication methods.
-
Question 43:
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.

You enable the authentication methods registration campaign and configure the Microsoft Authenticator method for Group1.
Which users will be prompted to configure authentication during sign in?
A. User1 only
B. User2 only
C. User2 and User3 only
D. User1 and User2 only
E. User2 and User3 only
F. User1, User2, and User3 only
-
Question 44:
You have a Microsoft 365 subscription named contofco.com
You need to configure Microsoft OneDrive for Business external sharing to meet the following requirements:
Enable flic sharing for users that rave a Microsoft account Block file sharing for anonymous users.
What should you do?
A. From Advanced settings tor external sharing, select Allow or Nock sharing with people on specific domains and add contoso.com.
B. From the External sharing settings for OneDrive. select Existing external users.
C. From the External sharing settings for OneDrive, select New and existing external users.
D. From the External sharing settings for OneDrive. select Only people in your organization.
-
Question 45:
You have a Microsoft 365 E5 Subscription named cont0S0.C0rn.
You create a user named User'.
You Need to ensure that User1 can change Status of Microsoft Defender for Identity health alerts. The solution must use principle of the least principle.
What should you do?
A. From the Microsoft 365 admin center, add user' to the Azure ATP contoso.com Administrators group.
B. From the Microsoft 365 Defender portal, assign user' the Security Operator role.
C. From the Microsoft 365 admin center, add user' to the Azure ATP contoso.com users group.
D. From the Microsoft admin center, assign user1 the Hybrid Identity Administrator role.
-
Question 46:
You plan to deploy a new Microsoft 365 Subscription that will contain 500 users.
You need to ensure that the following actions are performed the users sign in to the subscription
Evaluate the users' risk level based on their location and travel. Require high-risk users to sign in by using Azure Multi-Factor Authentication (Azure MFA).
The solution must minimize cost.
Which license should you assign to each user?
A. Microsoft 365 Business Premium
B. Microsoft 365 E3
C. Enterprise Mobility + Security E3
D. Microsoft 365 ES
-
Question 47:
You have a Microsoft 365 that uses Microsoft ShareP0nt Online.
You need to ensure that users can only share files with users at specified partner companies. The solution must minimize administrative effort.
What should you do?
A. Allow only in specific security groups to share externally.
B. Set File and folder links to people.
C. Limit external by domain
D. Set External sharing to New and existing guest
-
Question 48:
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
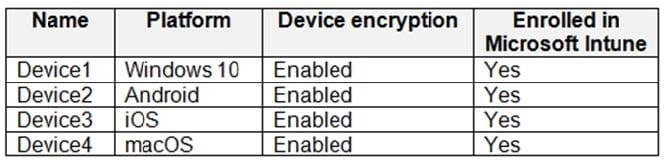
You Plan to use the encryption report in Microsoft Endpoint Manager to view devices that have encryption enabled. Which devices will be included in the encryption report?
A. Device1 only
B. Device1 and Device2 Only
C. Device1 and Device4 Only
D. Device1, Device2 and Device4 Only
E. Device1, Device2, Device 3 and Device 4
-
Question 49:
You have a Microsoft 365 E5 subscription that has Microsoft Defender for Office 365 enabled.
You need to review the zero-hour auto purge (ZAP) configuration for the subscription.
Which two threat policies should you review? Each correct answer presents part of the solution NOTE: Each correct selection is worth one point,
A. Safe attachments Built-in protection (Microsoft)
B. Anti-malware (Default) Default
C. Safe links Built-in protection (Microsoft)
D. Anti-spam outbound policy (Default)
E. Office365 AntiPhish Default (Default)
F. Anti-spam inbound policy (Default)
-
Question 50:
Your company has a Microsoft 365 E5 subscription that contains a user named User.
User1 leaves the company.
You need to identify all the personal data of User1 that is stored in the subscription.
What should you do in the Microsoft Purview compliance portal?
A. Create an eDscovery case.
B. Perform an audit.
C. Perform a content search.
D. Submit a Data Subject Request (DSR).
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-500 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.