Exam Details
Exam Code
:MS-500Exam Name
:Microsoft 365 Security AdministrationCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:367 Q&AsLast Updated
:Sep 11, 2023
Microsoft Microsoft Certifications MS-500 Questions & Answers
-
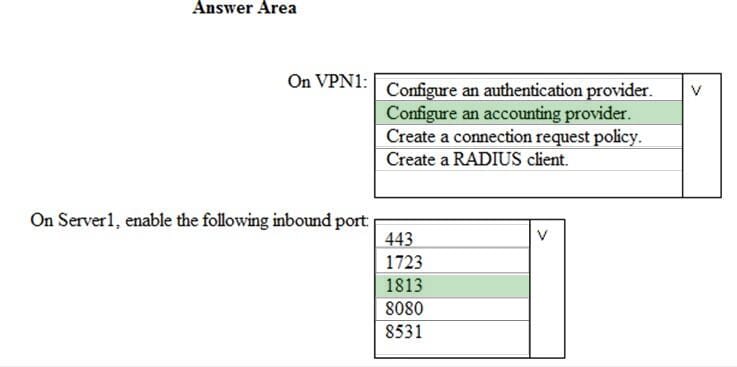
Question 341:
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains a VPN server named VPN1 that runs Windows Server 2016 and has the Remote Access server role installed.
You have a Microsoft Azure subscription.
You are deploying Microsoft Defender for Identity.
You install a Microsoft Defender for Identity standalone sensor on a server named Server1 that runs Windows Server 2016.
You need to integrate the VPN and Microsoft Defender for Identity.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

-
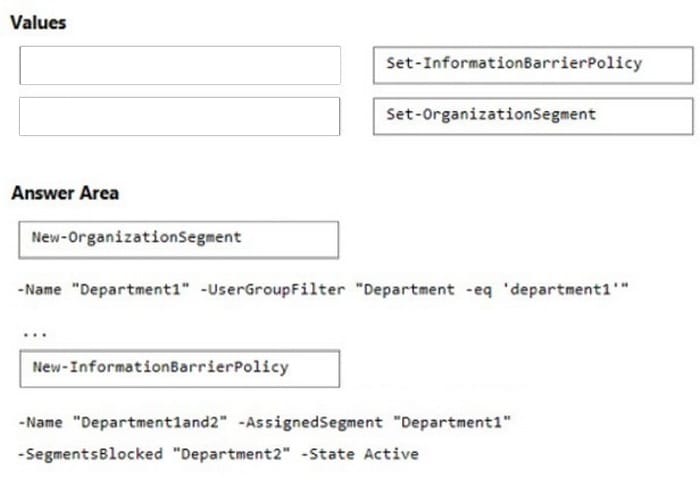
Question 342:
DRAG DROP
Your company has two departments named department1 and department2 and a Microsoft 365 E5 subscription.
You need to prevent communication between the users in department1 and the users in department2.
How should you complete the PowerShell script?
To answer, drag the appropriate values to the correct targets. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

-
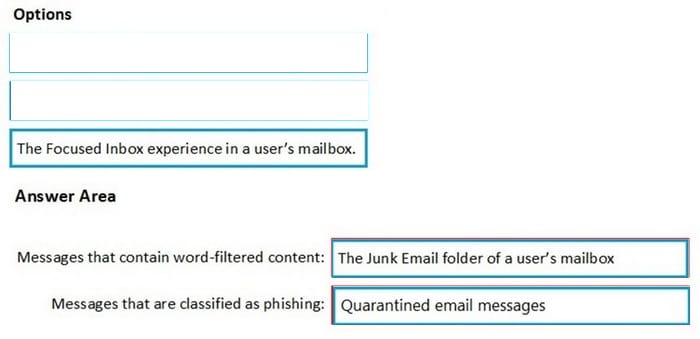
Question 343:
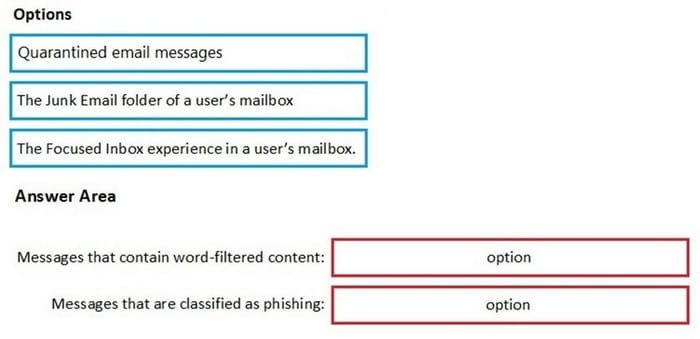
DRAG DROP
You have a Microsoft 365 E5 subscription. All users use Microsoft Exchange Online.
Microsoft 365 is configured to use the default policy settings without any custom rules.
You manage message hygiene.
Where are suspicious email messages placed by default? To answer, drag the appropriate location to the correct message types. Each option may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
Select and Place:
-
Question 344:
DRAG DROP
You have a Microsoft 365 subscription that contains 20 data loss prevention (DLP) policies.
You need to identify the following:
1.
Rules that are applied without Triggering a policy alert
2.
The top 10 files that have matched DLP policies
3.
Alerts that are miscategorized
Which report should you use for each requirement? To answer, drag the appropriate reports to the correct requirements. Each report may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll
to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

-
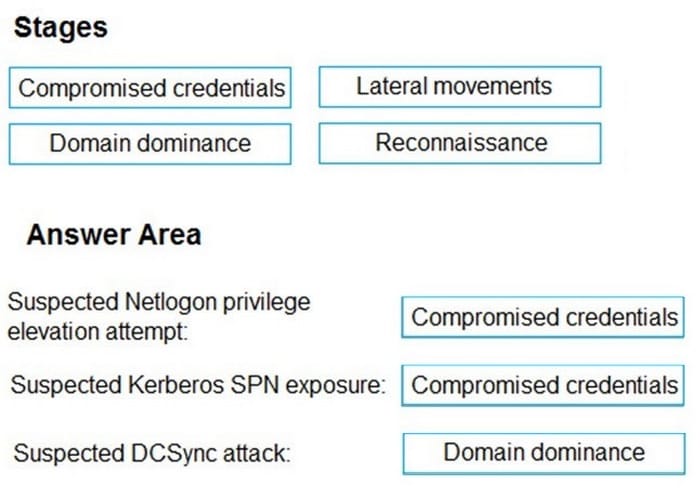
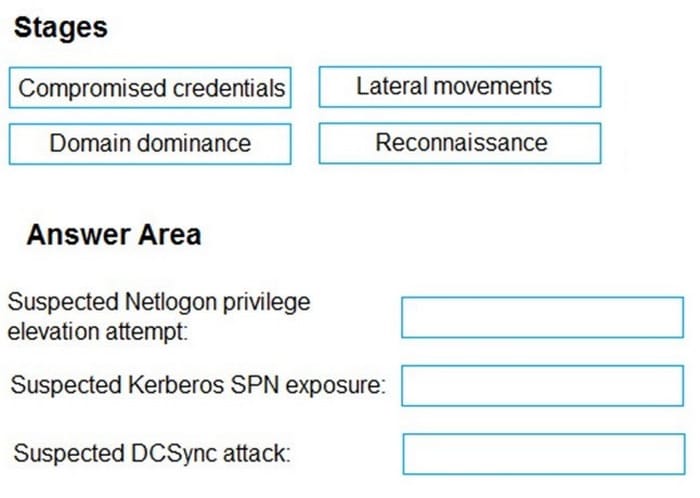
Question 345:
DRAG DROP
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Identity. You receive the following alerts:
1.
Suspected Netlogon privilege elevation attempt
2.
Suspected Kerberos SPN exposure
3.
Suspected DCSync attack
To which stage of the cyber-attack kill chain does each alert map? To answer, drag the appropriate alerts to the correct stages. Each alert may be used once, more than once, or not at all. You may need to drag the split bar between panes or
scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
-
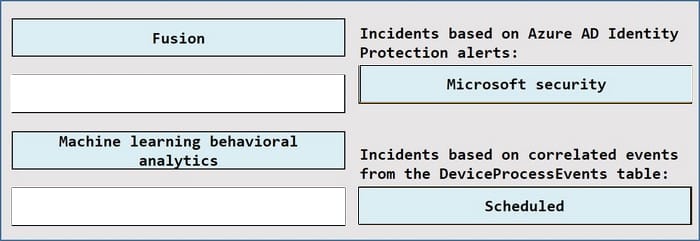
Question 346:
DRAG DROP
You have a Microsoft 365 E5 subscription.
You plan to implement Microsoft Sentinel to create incidents based on:
1.
Azure Active Directory (Azure AD) Identity Protection alerts
2.
Correlated events from the DeviceProcessEvents table
Which analytic rule types should you use for each incident type? To answer, drag the appropriate rule types to the correct incident types. Each rule type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:

-
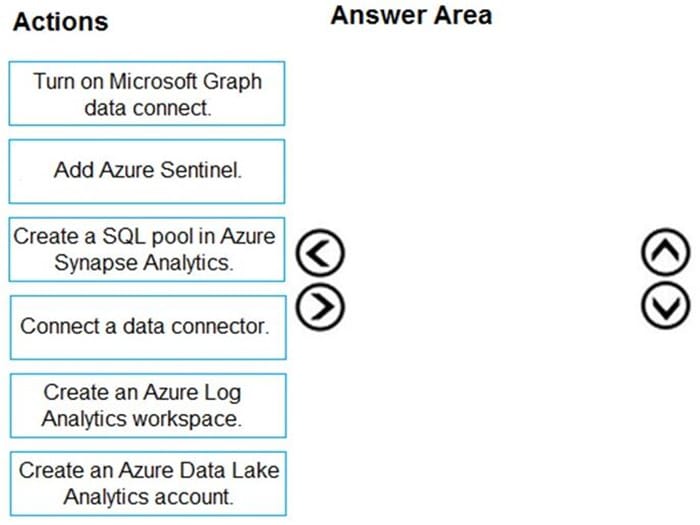
Question 347:
DRAG DROP
You have an Azure subscription and a Microsoft 365 subscription.
You need to perform the following actions:
1.
Deploy Azure Sentinel.
2.
Collect the Microsoft 365 activity log by using Azure Sentinel.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
-
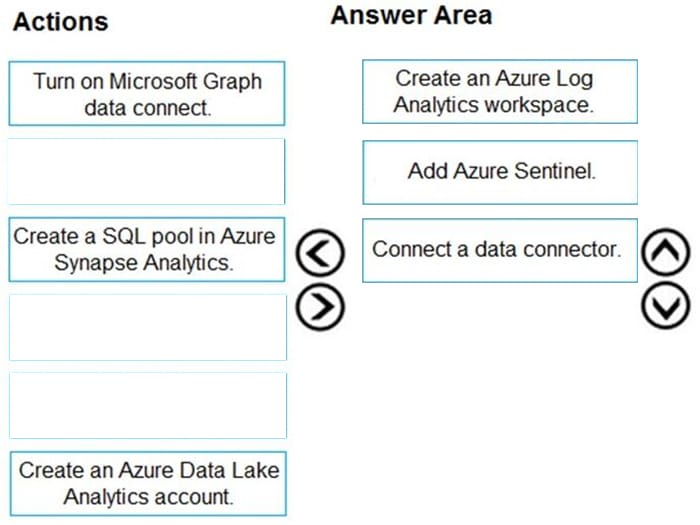
Question 348:
DRAG DROP
You have an Azure Sentinel workspace that has an Office 365 connector.
You are threat hunting events that have suspicious traffic from specific IP addresses.
You need to save the events and the relevant query results for future reference.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
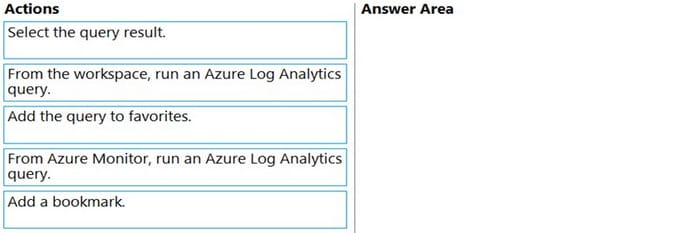
-
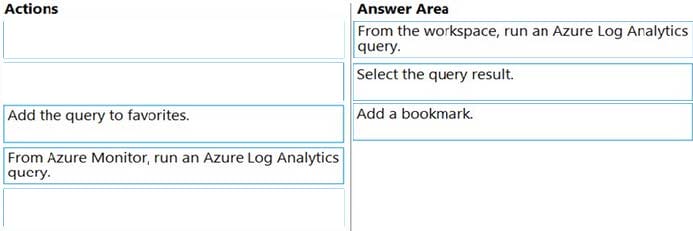
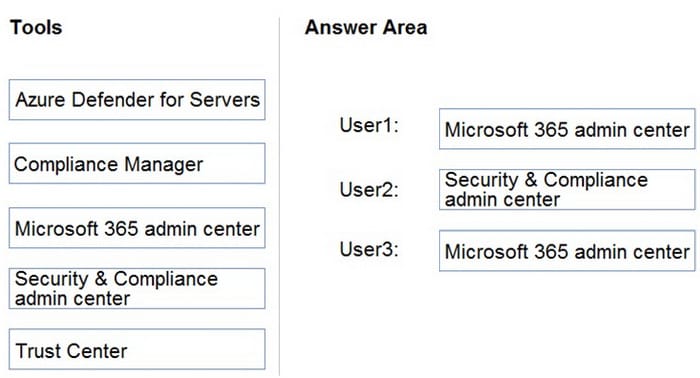
Question 349:
DRAG DROP
You have a Microsoft 365 E5 tenant that contains three users named User1, User2, and User3.
You need to assign roles or role groups to the users as shown in the following table.
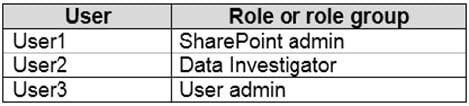
What should you use to assign a role or role group to each user? To answer, drag the appropriate tools to the correct roles or role groups. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between
panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
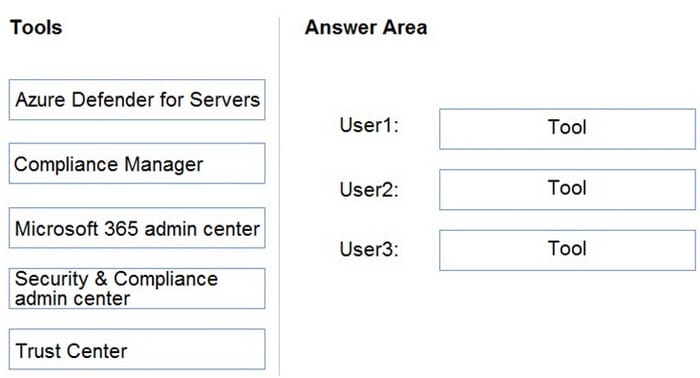
-
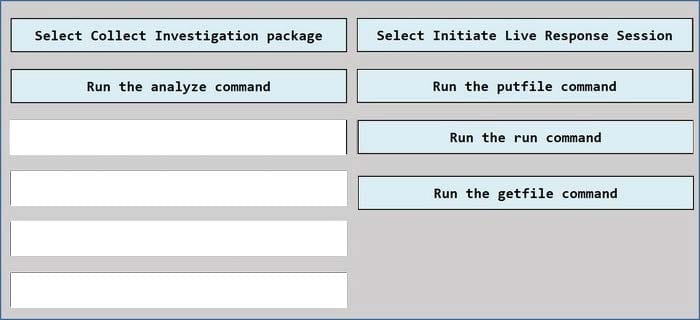
Question 350:
DRAG DROP
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint and contains a Windows 10 device named Device1.
You have a PowerShell script named script1 that collects forensic data and saves the results as a file on the device from which the script is run.
You receive a Microsoft Defender for Endpoint alert for suspicious activities on Device1.
You need to run script1 on Device1 and retrieve the output file of the script.
Which four actions should you perform in sequence in Microsoft 365 Defender portal?
To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
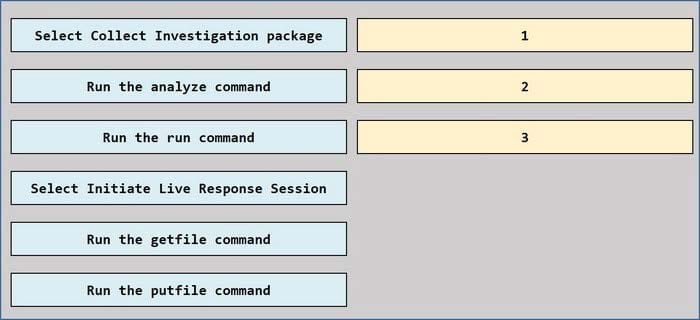
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-500 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.