Exam Details
Exam Code
:MD-101Exam Name
:Managing Modern DesktopsCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:421 Q&AsLast Updated
:Oct 30, 2023
Microsoft Microsoft Certifications MD-101 Questions & Answers
-
Question 201:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10.
You save a provisioning package named Package1 to a folder named C:\Folder1.
You need to apply Package1 to Computer1.
Solution: From File Explorer, you go to C:\Folder1, and then you double-click the Package1.ppkg file.
Does this meet the goal?
A. Yes
B. No
-
Question 202:
Your company has an internal portal that uses a URL of http://contoso.com.
The network contains computers that run Windows 10. The default browser on all the computers is Microsoft Edge.
You need to ensure that all users only use Internet Explorer to connect to the internal portal. The solution must ensure that Microsoft Edge can be used to connect to all other websites.
What should you do from each computer?
A. From Internet Explorer, configure the Compatibility View settings
B. From the local policy, configure Enterprise Mode
C. From Microsoft Edge, configure the Advanced Site Settings
D. From the Settings app, configure the default web browser settings
-
Question 203:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Directory group named Group1 that contains Windows 10 Enterprise devices and Windows 10 Pro devices.
From Microsoft Intune, you create a device configuration profile named Profile1.
You need to ensure that Profile1 applies to only the Windows 10 Enterprise devices in Group1.
Solution: You create a scope tag, and then you add the scope tag to the Windows 10 Enterprise devices. You edit the settings of Profile1.
Does this meet the goal?
A. Yes
B. No
-
Question 204:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Directory group named Group1 that contains Windows 10 Enterprise devices and Windows 10 Pro devices.
From Microsoft Intune, you create a device configuration profile named Profile1.
You need to ensure that Profile1 applies to only the Windows 10 Enterprise devices in Group1.
Solution: You configure an applicability rule for Profile1. You assign Profile1 to Group1.
Does this meet the goal?
A. Yes
B. No
-
Question 205:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Directory group named Group1 that contains Windows 10 Enterprise devices and Windows 10 Pro devices.
From Microsoft Intune, you create a device configuration profile named Profile1.
You need to ensure that Profile1 applies to only the Windows 10 Enterprise devices in Group1.
Solution: You create an Azure Active Directory group that contains only the Windows 10 Enterprise devices. You assign Profile1 to the new group.
Does this meet the goal?
A. Yes
B. No
-
Question 206:
You have a computer named Computer1 that runs Windows 10.
Computer1 is used by a user named User1.
You need to ensure that when User1 opens websites from untrusted locations by using Microsoft Edge, Microsoft Edge runs in an isolated container.
What should you do first?
A. From Windows Features, turn on Windows Defender Application Guard.
B. From Windows Features, turn on Hyper-V Platform.
C. From Windows Security, configure the Virus and threat protection settings.
D. From Windows Security, configure the Device security settings.
-
Question 207:
You have computers that run Windows 10 and are managed by using Microsoft Intune.
Users store their files in a folder named D:\Folder1.
You need to ensure that only a trusted list of applications is granted write access to D:\Folder1.
What should you configure in the device configuration profile?
A. Microsoft Defender SmartScreen
B. Microsoft Defender Exploit Guard
C. Microsoft Defender Application Guard
D. Microsoft Defender Application Control
-
Question 208:
You have a hybrid Microsoft Azure Active Directory (Azure AD) tenant, a Microsoft System Center Configuration Manager (Current Branch) environment, and a Microsoft 365 subscription. You have computers that run Windows 10 as shown in the following table.
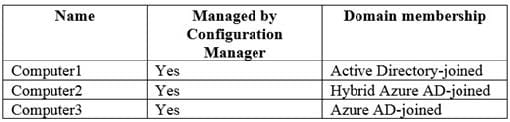
You plan to use Microsoft 365 Device Management.
Which computers support co-management by Configuration Manager and Device Management?
A. Computer3 only
B. Computer1 and Computer2 only
C. Computer2 only
D. Computer1, Computer2, and Computer3
-
Question 209:
You have a shared computer that runs Windows 10.
The computer is infected with a virus.
You discover that a malicious TTF font was used to compromise the computer.
You need to prevent this type of threat from affecting the computer in the future.
What should you use?
A. Windows Defender Exploit Guard
B. Windows Defender Application Guard
C. Windows Defender Credential Guard
D. Windows Defender System Guard
E. Windows Defender SmartScreen
-
Question 210:
You have a public computer named Public1 that runs Windows 10.
Users use Public1 to browse the internet by using Microsoft Edge.
You need to view events associated with website phishing attacks on Public1.
Which Event Viewer log should you view?
A. Applications and Services Logs > Microsoft\Windows > DeviceGuard > Operational
B. Applications and Services Logs > Microsoft > Windows > Security-Mitigations > User Mode
C. Applications and Services Logs > Microsoft > Windows > SmartScreen > Debug
D. Applications and Services Logs > Microsoft > Windows > Windows Defender > Operational
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MD-101 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.