Exam Details
Exam Code
:MCIA-LEVEL-1-MAINTENANCEExam Name
:MuleSoft Certified Integration Architect - Level 1 MAINTENANCECertification
:Mulesoft CertificationsVendor
:MulesoftTotal Questions
:116 Q&AsLast Updated
:Jul 14, 2025
Mulesoft Mulesoft Certifications MCIA-LEVEL-1-MAINTENANCE Questions & Answers
-
Question 11:
What is an example of data confidentiality?
A. Signing a file digitally and sending it using a file transfer mechanism
B. Encrypting a file containing personally identifiable information (PV)
C. Providing a server's private key to a client for secure decryption of data during a two- way SSL handshake
D. De-masking a person's Social Security number while inserting it into a database
-
Question 12:
Insurance organization is planning to deploy Mule application in MuleSoft Hosted runtime plane. As a part of requirement , application should be scalable . highly available. It also has regulatory requirement which demands logs to be retained for at least 2 years. As an Integration Architect what step you will recommend in order to achieve this?
A. It is not possible to store logs for 2 years in CloudHub deployment. External log management system is required.
B. When deploying an application to CloudHub , logs retention period should be selected as 2 years
C. When deploying an application to CloudHub, worker size should be sufficient to store 2 years data
D. Logging strategy should be configured accordingly in log4j file deployed with the application.
-
Question 13:
A Mule application is being designed To receive nightly a CSV file containing millions of records from an external vendor over SFTP, The records from the file need to be validated, transformed. And then written to a database. Records can be inserted into the database in any order.
In this use case, what combination of Mule components provides the most effective and performant way to write these records to the database?
A. Use a Parallel for Each scope to Insert records one by one into the database
B. Use a Scatter-Gather to bulk insert records into the database
C. Use a Batch job scope to bulk insert records into the database.
D. Use a DataWeave map operation and an Async scope to insert records one by one into the database.
-
Question 14:
An organization has deployed both Mule and non-Mule API implementations to integrate its customer and order management systems. All the APIs are available to REST clients on the public internet.
The organization wants to monitor these APIs by running health checks: for example, to determine if an API can properly accept and process requests. The organization does not have subscriptions to any external monitoring tools and also
does not want to extend its IT footprint.
What Anypoint Platform feature provides the most idiomatic (used for its intended purpose) way to monitor the availability of both the Mule and the non-Mule API implementations?
A. API Functional Monitoring
B. Runtime Manager
C. API Manager
D. Anypoint Visualizer
-
Question 15:
Refer to the exhibit.
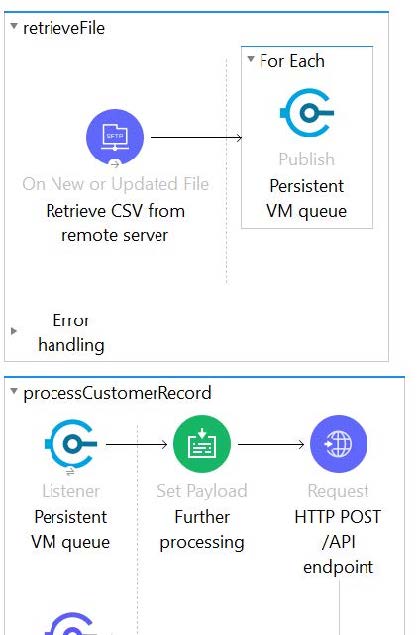
This Mule application is deployed to multiple Cloudhub workers with persistent queue enabled. The retrievefile flow event source reads a CSV file from a remote SFTP server and then publishes each record in the CSV file to a VM queue. The
processCustomerRecords flow's VM Listner receives messages from the same VM queue and then processes each message separately.
How are messages routed to the cloudhub workers as messages are received by the VM Listener?
A. Each message is routed to ONE of the Cloudhub workers in a DETERMINSTIC round robin fashion thereby EXACTLY BALANCING messages among the cloudhub workers
B. Each messages routes to ONE of the available Clouhub workers in a NON- DETERMINSTIC non round-robin fashion thereby APPROXIMATELY BALANCING messages among the cloudhub workers
C. Each message is routed to the SAME Cloudhub worker that retrieved the file, thereby BINDING ALL messages to ONLY that ONE Cloudhub worker
D. Each message is duplicated to ALL of the Cloudhub workers, thereby SHARING EACH message with ALL the Cloudhub workers.
-
Question 16:
A system administrator needs to determine when permissions were last changed for an Anypoint Platform user. Which Anypoint Platform component should the administrator use to obtain this information?
A. Audit Logging
B. Anypoint Monitoring
C. Anypiont Studio
D. Mule Stack Traces
-
Question 17:
An organization is not meeting its growth and innovation objectives because IT cannot deliver projects last enough to keep up with the pace of change required by the business. According to MuleSoft's IT delivery and operating model, which step should the organization lake to solve this problem?
A. Modify IT governance and security controls so that line of business developers can have direct access to the organization's systems of record
B. Switch from a design-first to a code-first approach for IT development
C. Adopt a new approach that decouples core IT projects from the innovation that happens within each line of business
D. Hire more |T developers, architects, and project managers to increase IT delivery
-
Question 18:
A Mule application is built to support a local transaction for a series of operations on a single database. The mule application has a Scatter-Gather scope that participates in the local transaction. What is the behavior of the Scatter-Gather when running within this local transaction?
A. Execution of all routes within Scatter-Gather occurs in parallel Any error that occurs inside Scatter-Gather will result in a roll back of all the database operations
B. Execution of all routes within Scatter-Gather occurs sequentially Any error that occurs inside Scatter-Gather will be handled by error handler and will not result in roll back
C. Execution of all routes within Scatter-Gather occurs sequentially Any error that occurs inside Scatter-Gather will result in a roll back of all the database operations
D. Execution of all routes within Scatter-Gather occurs in parallel Any error that occurs inside Scatter-Gather will be handled by error handler and will not result in roll back
-
Question 19:
As part of a growth strategy, a supplier signs a trading agreement with a large customer. The customer sends purchase orders to the supplier according to the ANSI X12 EDI standard, and the supplier creates the orders in its ERP system
using the information in the EDI document.
The agreement also requires that the supplier provide a new RESTful API to process request from the customer for current product inventory level from the supplier' s ERP system.
Which two fundamental integration use cases does the supplier need to deliver to provide an end-to-end solution for this business scenario? (Choose two.)
A. Synchronized data transfer
B. Sharing data with external partners
C. User interface integration
D. Streaming data ingestion
E. Data mashups
-
Question 20:
Refer to the exhibit.
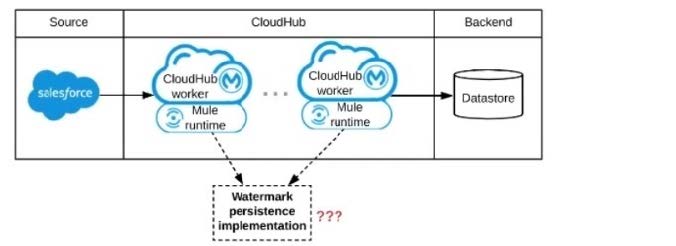
A Mule application is being designed to be deployed to several CIoudHub workers. The Mule application's integration logic is to replicate changed Accounts from Satesforce to a backend system every 5 minutes.
A watermark will be used to only retrieve those Satesforce Accounts that have been modified since the last time the integration logic ran.
What is the most appropriate way to implement persistence for the watermark in order to support the required data replication integration logic?
A. Persistent Anypoint MQ Queue
B. Persistent Object Store
C. Persistent Cache Scope
D. Persistent VM Queue
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Mulesoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MCIA-LEVEL-1-MAINTENANCE exam preparations and Mulesoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.