Exam Details
Exam Code
:GCCCExam Name
:GCCC - GIAC Critical Controls Certification (GCCC)Certification
:Cyber SecurityVendor
:GIACTotal Questions
:93 Q&AsLast Updated
:
GIAC Cyber Security GCCC Questions & Answers
-
Question 1:
A security incident investigation identified the following modified version of a legitimate system file on a compromised client:
C:\Windows\System32\winxml.dll Addition Jan. 16, 2014 4:53:11 PM
The infection vector was determined to be a vulnerable browser plug-in installed by the user. Which of the organization's CIS Controls failed?
A. Application Software Security
B. Inventory and Control of Software Assets
C. Maintenance, Monitoring, and Analysis of Audit Logs
D. Inventory and Control of Hardware Assets
-
Question 2:
Which of the following best describes the CIS Controls?
A. Technical, administrative, and policy controls based on research provided by the SANS Institute
B. Technical controls designed to provide protection from the most damaging attacks based on current threat data
C. Technical controls designed to augment the NIST 800 series
D. Technical, administrative, and policy controls based on current regulations and security best practices
-
Question 3:
A global corporation has major data centers in Seattle, New York, London and Tokyo. Which of the following is the correct approach from an intrusion detection and event correlation perspective?
A. Configure all data center systems to use local time
B. Configure all data center systems to use GMT time
C. Configure all systems to use their default time settings
D. Synchronize between Seattle and New York, and use local time for London and Tokyo
-
Question 4:
What is the relationship between a service and its associated port?
A. A service closes a port after a period of inactivity
B. A service relies on the port to select the protocol
C. A service sets limits on the volume of traffic sent through the port
D. A service opens the port and listens for network traffic
-
Question 5:
DHCP logging output in the screenshot would be used for which of the following?
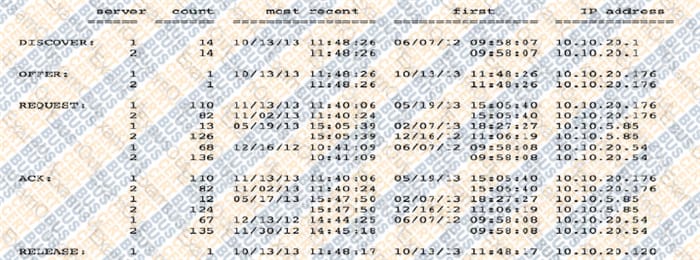
A. Enforcing port-based network access control to prevent unauthorized devices on the network.
B. Identifying new connections to maintain an up-to-date inventory of devices on the network.
C. Detecting malicious activity by compromised or unauthorized devices on the network.
D. Providing ping sweep results to identify live network hosts for vulnerability scanning.
-
Question 6:
Kenya is a system administrator for SANS. Per the recommendations of the CIS Controls she has a dedicated host (kenya- adminbox / 10.10.10.10) for any administrative tasks. She logs into the dedicated host with her domain admin credentials. Which of the following connections should not exist from kenyaadminbox?
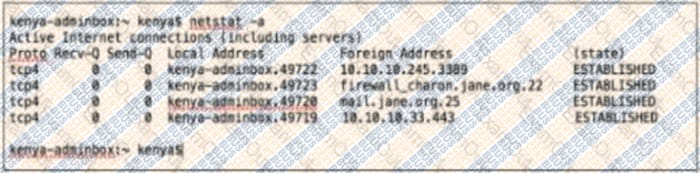
A. 10.10.245.3389
B. Mail.jane.org.25
C. Firewall_charon.jane.org.22
D. 10.10.10.33.443
-
Question 7:
Of the options shown below, what is the first step in protecting network devices?
A. Creating standard secure configurations for all devices
B. Scanning the devices for known vulnerabilities
C. Implementing IDS to detect attacks
D. Applying all known security patches
-
Question 8:
Which of the following is used to prevent spoofing of e-mail addresses?
A. Sender Policy Framework
B. DNS Security Extensions
C. Public-Key Cryptography
D. Simple Mail Transfer Protocol
-
Question 9:
Which CIS Control includes storing system images on a hardened server, scanning production systems for out-of-date software, and using file integrity assessment tools like tripwire?
A. Inventory of Authorized and Unauthorized Software
B. Continuous Vulnerability Management
C. Secure Configurations for Network Devices such as Firewalls, Routers and Switches
D. Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
-
Question 10:
Which of the following should be used to test antivirus software?
A. FIPS 140-2
B. Code Red
C. Heartbleed
D. EICAR
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GIAC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your GCCC exam preparations and GIAC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.