Exam Details
Exam Code
:EPM-DEFExam Name
:CyberArk Defender - EPMCertification
:CyberArk CertificationsVendor
:CyberArkTotal Questions
:60 Q&AsLast Updated
:Jul 19, 2025
CyberArk CyberArk Certifications EPM-DEF Questions & Answers
-
Question 51:
Which EPM reporting tool provides a comprehensive view of threat detection activity?
A. Threat Detection Dashboard
B. Detected Threats
C. Threat Detection Events
D. McAfee ePO Reports
-
Question 52:
For Advanced Policies, what can the target operating system users be set to?
A. Local or AD users and groups, Azure AD User, Azure AD Group
B. AD Groups, Azure AD Groups
C. Local or AD users and groups
D. Local or AD users, Azure AD Users
-
Question 53:
Which threat intelligence source requires the suspect file to be sent externally?
A. NSRL
B. Palo Alto Wildfire
C. VirusTotal
D. CyberArk Application Risk Analysis Service (ARA)
-
Question 54:
What is the CyberArk recommended practice when deploying the EPM agent to non- persistent VDIs?
A. A separate set
B. a VDI advanced policy
C. a separate license
D. A separate computer group
-
Question 55:
Where would an EPM admin configure an application policy that depends on a script returning true for an end user's machine being connected to an open (no password protection) Wi-Fi?
A. Advanced Policy - Application Control - Check Wi-Fi security
B. Advanced Policy - Options: Conditional enforcement - Apply Policy according to Script execution result
C. Default policies - Check if network access is secure
D. Advanced Policy - Access - Specify permissions to be set for Wi-Fi network security
-
Question 56:
An end user is experiencing performance issues on their device after the EPM Agent had been installed on their machine. What should the EPM Administrator do first to help resolve the issue?
A. Verify any 3rd party security solutions have been added to EPM's Files To Be Ignored Always configuration and CyberArk EPM has also been excluded from the 3rd party security solutions.
B. Enable the Default Policy's Privilege Management Control, Unhandled Privileged Applications in Elevate mode.
C. Rerun the agent installation on the user's machine to repair the installation.
D. Uninstall or disable any anti-virus software prohibiting the EPM Agent functionalities.
-
Question 57:
An EPM Administrator is looking to enable the Threat Deception feature, under what section should the EPM Administrator go to enable this feature?
A. Threat Protection Inbox
B. Policies
C. Threat Intelligence
D. Policy Audit
-
Question 58:
What is a valid step to investigate an EPM agent that is unable to connect to the EPM server?
A. On the end point, open a browser session to the URL of the EPM server.
B. Ping the endpoint from the EPM server.
C. Ping the server from the endpoint.
D. Restart the end point
-
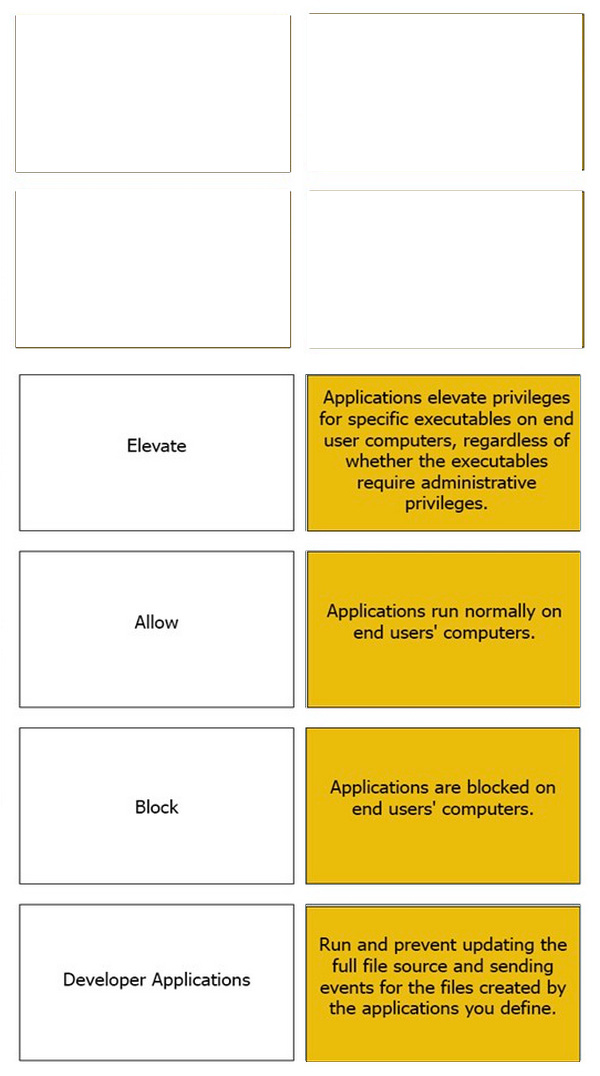
Question 59:
DRAG DROP
Match the Application Groups policy to their correct description.
Select and Place:
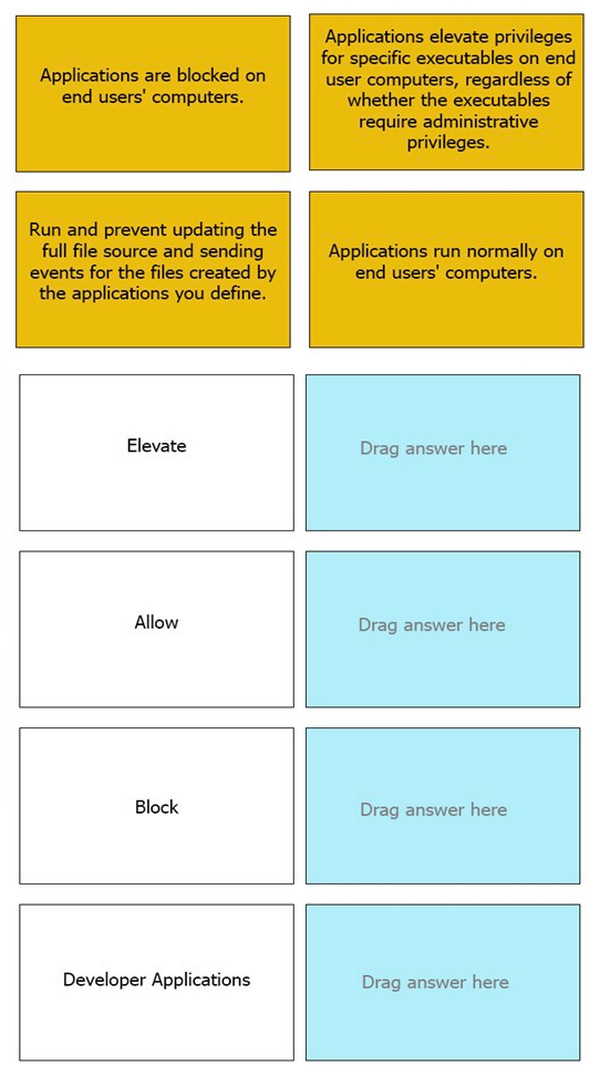
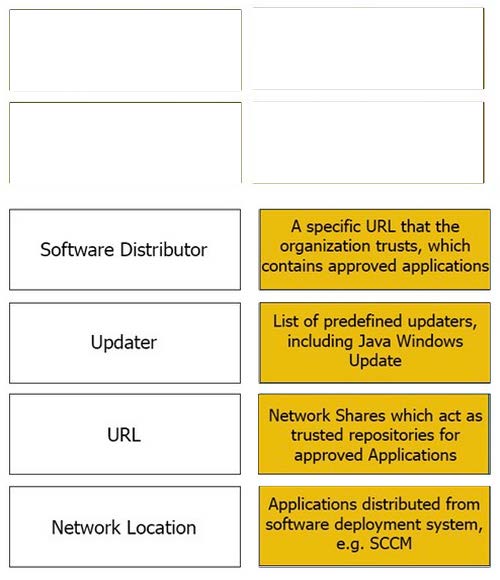
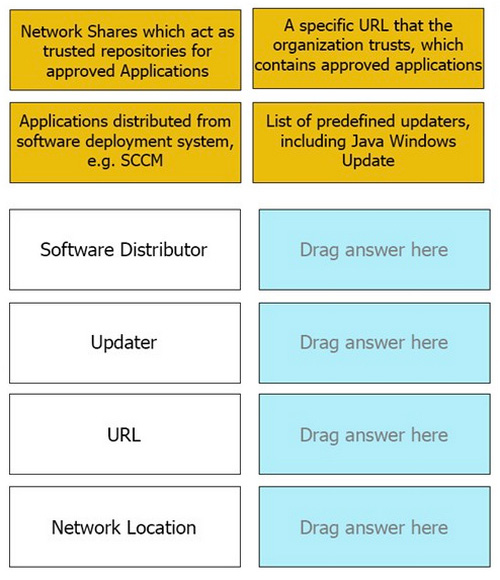
-
Question 60:
DRAG DROP
Match the Trusted Source to its correct definition:
Select and Place:
Related Exams:
CAU201
CyberArk DefenderCAU301
CyberArk SentryCAU302
CyberArk Defender - SentryCAU305
Sentry (Combined) CAU305 - CyberArk CDE RecertificationCPC-SEN
CyberArk Sentry - Privilege CloudEPM-DEF
CyberArk Defender - EPMPAM-CDE-RECERT
CyberArk CDE RecertificationPAM-DEF
CyberArk Defender - PAMPAM-SEN
CyberArk Sentry PAMSECRET-SEN
CyberArk Sentry - Secrets Manager
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CyberArk exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your EPM-DEF exam preparations and CyberArk certification application, do not hesitate to visit our Vcedump.com to find your solutions here.