Exam Details
Exam Code
:CIS-VRExam Name
:Certified Implementation Specialist - Vulnerability ResponseCertification
:ServiceNow CertificationsVendor
:ServiceNowTotal Questions
:60 Q&AsLast Updated
:Jun 21, 2025
ServiceNow ServiceNow Certifications CIS-VR Questions & Answers
-
Question 21:
What option can be used to close out a Vulnerable Item Record or initiate the Exception Process?
A. Complete
B. Update
C. Close/Defer
D. Save
-
Question 22:
When an approval is rejected for a Vulnerable Item exception, what happens to the State field for that record?
A. It reverts to `Analysis'
B. It is set to `New'
C. It is set to `In Review'
D. It will be set back to its previous value
-
Question 23:
Some customers may have a clearly-defined, well-documented vulnerability exception process and some may even provide a diagram illustrating that process.
What is the main advantage of having this documentation when translating it into a Flow or Workflow?
A. Perfect opportunity for process improvement
B. Understand their internal process
C. Build the Flow/Workflow directly into the platform
D. No advantage
-
Question 24:
Approvals within the Vulnerability Application are created based on:
A. The sys_approval and the sn_vul_vulnerable_item tables
B. The sn_vul_vulnerable_item and sn_vul_vulnerability tables
C. The sn_vul_change_approval table
D. The sys_approval table
-
Question 25:
Best Practices dictate that when creating a Change task from a Vulnerable Item, which of the following fields should be used for assigning the Assigned To field on the Change task?
A. Assigned To on Vulnerable Item
B. Managed By on CMDB_CI
C. Assigned To on CMDB_CI Record
D. Best Practice does not dictate a specific field
-
Question 26:
What do Vulnerability Exceptions require?
A. An Approval by default
B. An Exception Workflow
C. A GRC integration
D. A Filter Group
-
Question 27:
Ignoring a Vulnerable Item:
A. Permanently removes the item from the list of Active Vulnerable Items
B. Move the item to the Slushbucket
C. Has no impact on the list of Active Vulnerable Items
D. Temporarily removes the item from the list of Active Vulnerable Items
-
Question 28:
Which application provides the opportunity to align security events with organizational controls, automatically appraising other business functions of potential impact?
A. Performance Analytics
B. Event Management
C. Governance, Risk, and Compliance
D. Service Mapping
-
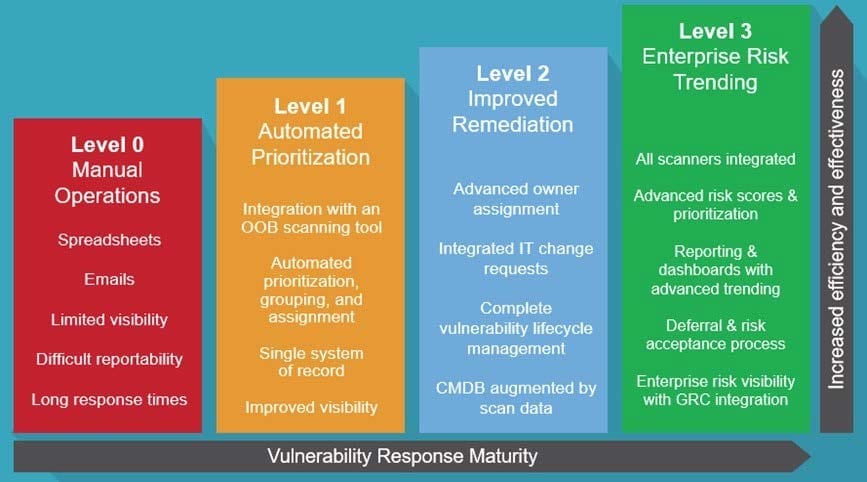
Question 29:
Which Vulnerability maturity level provides advanced owner assignment?
A. Enterprise risk trending
B. Automated prioritization
C. Manual operations
D. Improved remediation
-
Question 30:
Vulnerability Response is a scoped application; which prefix is attached to all items related to the application?
A. cmn_vul
B. vul
C. sn_vul
D. x_vul
Related Exams:
CAD
Certified Application DeveloperCAS-PA
Certified Application Specialist - Performance AnalyticsCIS-APM
Certified Implementation Specialist - Application Portfolio ManagementCIS-CPG
Certified Implementation Specialist - Cloud Provisioning and GovernanceCIS-CSM
Certified Implementation Specialist - Customer Service ManagementCIS-DISCOVERY
Certified Implementation Specialist - DiscoveryCIS-EM
Certified Implementation Specialist - Event MangementCIS-FSM
Certified Implementation Specialist - Field Service ManagementCIS-HAM
Certified Implementation Specialist - Hardware Asset ManagementCIS-HR
Certified Implementation Specialist - Human Resource
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only ServiceNow exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CIS-VR exam preparations and ServiceNow certification application, do not hesitate to visit our Vcedump.com to find your solutions here.