CFR-410 Exam Details
-
Exam Code
:CFR-410 -
Exam Name
:CyberSec First Responder (CFR) -
Certification
:CertNexus Certifications -
Vendor
:CertNexus -
Total Questions
:180 Q&As -
Last Updated
:Jan 13, 2026
CertNexus CFR-410 Online Questions & Answers
-
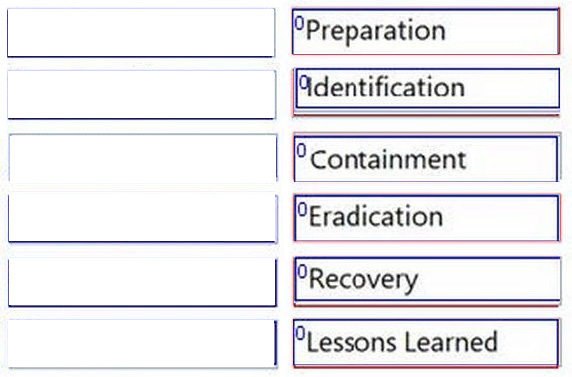
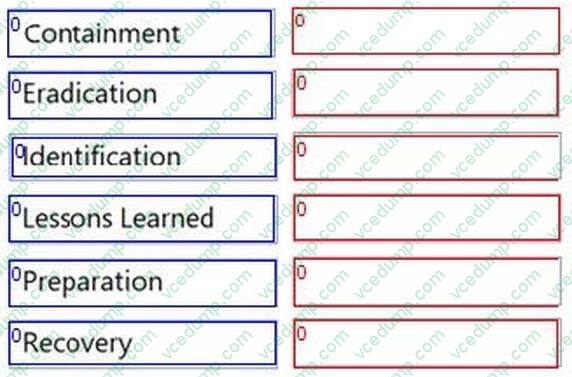
Question 1:
DRAG DROP
What is the correct order of the DFIR phases?
Select and Place:
-
Question 2:
A first responder notices a file with a large amount of clipboard information stored in it. Which part of the MITRE ATTandCK matrix has the responder discovered?
A. Collection
B. Discovery
C. Lateral movement
D. Exfiltration -
Question 3:
It was recently discovered that many of an organization's servers were running unauthorized cryptocurrency mining software. Which of the following assets were being targeted in this attack? (Choose two.)
A. Power resources
B. Network resources
C. Disk resources
D. Computing resources
E. Financial resources -
Question 4:
While reviewing some audit logs, an analyst has identified consistent modifications to the sshd_config file for an organization's server. The analyst would like to investigate and compare contents of the current file with archived versions of files that are saved weekly. Which of the following tools will be MOST effective during the investigation?
A. cat * | cut –d
B. more * | grep
C. diff
D. sort * -
Question 5:
Traditional SIEM systems provide:
A. Unknown Attacks Analysis User Behavior Analysis and Network Anomalies
B. Aggregation, Normalization, Correlation, and Alerting.
C. Static Malware Analysis, Dynamic Malware Analysis, and Hybrid Malware Analysis.
D. Privileged Identity Management. Privileged Access Management, and Identity and Access Management. -
Question 6:
Which of the following is the FIRST step taken to maintain the chain of custody in a forensic investigation?
A. Security and evaluating the electronic crime scene.
B. Transporting the evidence to the forensics lab
C. Packaging the electronic device
D. Conducting preliminary interviews -
Question 7:
Which three of the following are included in encryption architecture? (Choose three.)
A. Certificate
B. Encryption keys
C. Encryption engine
D. Database encryption
E. Data -
Question 8:
A security analyst has discovered that an application has failed to run. Which of the following is the tool MOST likely used by the analyst for the initial discovery?
A. syslog
B. MSConfig
C. Event Viewer
D. Process Monitor -
Question 9:
Which three answer options are password attack methods and techniques? (Choose three.)
A. Cross-Site Scripting attack
B. Brute force attack
C. Man-in-the-middle attack
D. Hybrid attack
E. Dictionary attack -
Question 10:
When tracing an attack to the point of origin, which of the following items is critical data to map layer 2 switching?
A. DNS cache
B. ARP cache
C. CAM table
D. NAT table
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CertNexus exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CFR-410 exam preparations and CertNexus certification application, do not hesitate to visit our Vcedump.com to find your solutions here.