Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 651:
A security analyst is inspecting pseudocode of the following multithreaded application:
1. perform daily ETL of data
1.1 validate that yesterday's data model file exists
1.2 validate that today's data model file does not exist
1.2 extract yesterday's data model
1.3 transform the format
1.4 load the transformed data into today's data model file
1.5 exit
Which of the following security concerns is evident in the above pseudocode?
A. Time of check/time of use
B. Resource exhaustion
C. Improper storage of sensitive data
D. Privilege escalation
-
Question 652:
The code snippet below controls all electronic door locks to a secure facility in which the doors should only fail open in an emergency. In the code, "criticalValue" indicates if an emergency is underway:

Which of the following is the BEST course of action for a security analyst to recommend to the software developer?
A. Rewrite the software to implement fine-grained, conditions-based testing
B. Add additional exception handling logic to the main program to prevent doors from being opened
C. Apply for a life-safety-based risk exception allowing secure doors to fail open
D. Rewrite the software's exception handling routine to fail in a secure state
-
Question 653:
An infrastructure team is at the end of a procurement process and has selected a vendor. As part of the final negotiations, there are a number of outstanding issues, including:
1.
Indemnity clauses have identified the maximum liability
2.
The data will be hosted and managed outside of the company's geographical location
The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant on the project, which of the following should the project's security consultant recommend as the NEXT step?
A. Develop a security exemption, as it does not meet the security policies
B. Mitigate the risk by asking the vendor to accept the in-country privacy principles
C. Require the solution owner to accept the identified risks and consequences
D. Review the entire procurement process to determine the lessons learned
-
Question 654:
A security administrator is hardening a TrustedSolaris server that processes sensitive data. The data owner has established the following security requirements:
The data is for internal consumption only and shall not be distributed to outside individuals The systems administrator should not have access to the data processed by the server The integrity of the kernel image is maintained
Which of the following host-based security controls BEST enforce the data owner's requirements? (Choose three.)
A. SELinux
B. DLP
C. HIDS
D. Host-based firewall
E. Measured boot
F. Data encryption
G. Watermarking
-
Question 655:
A security analyst has been asked to create a list of external IT security concerns, which are applicable to the organization. The intent is to show the different types of external actors, their attack vectors, and the types of vulnerabilities that would cause business impact. The Chief Information Security Officer (CISO) will then present this list to the board to request funding for controls in areas that have insufficient coverage.
Which of the following exercise types should the analyst perform?
A. Summarize the most recently disclosed vulnerabilities.
B. Research industry best practices and latest RFCs.
C. Undertake an external vulnerability scan and penetration test.
D. Conduct a threat modeling exercise.
-
Question 656:
Ann, a corporate executive, has been the recent target of increasing attempts to obtain corporate secrets by competitors through advanced, well-funded means. Ann frequently leaves her laptop unattended and physically unsecure in hotel rooms during travel. A security engineer must find a practical solution for Ann that minimizes the need for user training. Which of the following is the BEST solution in this scenario?
A. Full disk encryption
B. Biometric authentication
C. An eFuse-based solution
D. Two-factor authentication
-
Question 657:
A security consultant is performing a penetration test on www.comptia.org and wants to discover the DNS administrator's email address to use in a later social engineering attack. The information listed with the DNS registrar is private. Which of the following commands will also disclose the email address?
A. dig comptia.org
B. whois comptia.org
C. nslookup ype=SOA comptia.org
D. dnsrecon comptia.org hostmaster
-
Question 658:
A security administrator is reviewing the following output from an offline password audit:
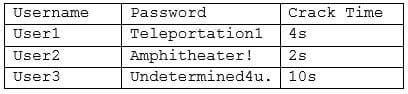
Which of the following should the systems administrator implement to BEST address this audit finding? (Choose two.)
A. Cryptoprocessor
B. Bcrypt
C. SHA-256
D. PBKDF2
E. Message authentication
-
Question 659:
A corporate forensic investigator has been asked to acquire five forensic images of an employee database application. There are three images to capture in the United States, one in the United Kingdom, and one in Germany. Upon completing the work, the forensics investigator saves the images to a local workstation. Which of the following types of concerns should the forensic investigator have about this work assignment?
A. Environmental
B. Privacy
C. Ethical
D. Criminal
-
Question 660:
An engineer is reviewing the security architecture for an enterprise network. During the review, the engineer notices an undocumented node on the network. Which of the following approaches can be utilized to determine how this node operates? (Choose two.)
A. Use reverse engineering and techniques
B. Assess the node within a continuous integration environment
C. Employ a static code analyzer
D. Review network and traffic logs
E. Use a penetration testing framework to analyze the node
F. Analyze the output of a ping sweep
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.