Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 621:
A forensic analyst suspects that a buffer overflow exists in a kernel module. The analyst executes the following command:
dd if=/dev/ram of=/tmp/mem/dmp The analyst then reviews the associated output: ^34^#AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/bin/bash^21^03#45
However, the analyst is unable to find any evidence of the running shell.
Which of the following of the MOST likely reason the analyst cannot find a process ID for the shell?
A. The NX bit is enabled
B. The system uses ASLR
C. The shell is obfuscated
D. The code uses dynamic libraries
-
Question 622:
After several industry comnpetitors suffered data loss as a result of cyebrattacks, the Chief Operating Officer (COO) of a company reached out to the information security manager to review the organization's security stance. As a result of the discussion, the COO wants the organization to meet the following criteria:
Blocking of suspicious websites Prevention of attacks based on threat intelligence Reduction in spam Identity-based reporting to meet regulatory compliance Prevention of viruses based on signature Protect applications from web-based threats
Which of the following would be the BEST recommendation the information security manager could make?
A. Reconfigure existing IPS resources
B. Implement a WAF
C. Deploy a SIEM solution
D. Deploy a UTM solution
E. Implement an EDR platform
-
Question 623:
A server (10.0.0.2) on the corporate network is experiencing a DoS from a number of marketing desktops that have been compromised and are connected to a separate network segment. The security engineer implements the following configuration on the management router:
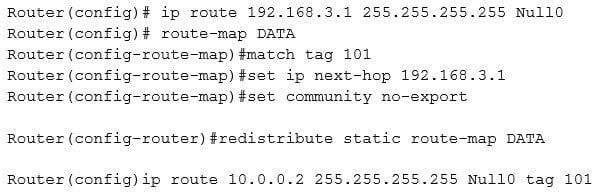
Which of the following is the engineer implementing?
A. Remotely triggered black hole
B. Route protection
C. Port security
D. Transport security
E. Address space layout randomization
-
Question 624:
A security technician receives a copy of a report that was originally sent to the board of directors by the Chief Information Security Officer (CISO). The report outlines the following KPI/KRI data for the last 12 months:
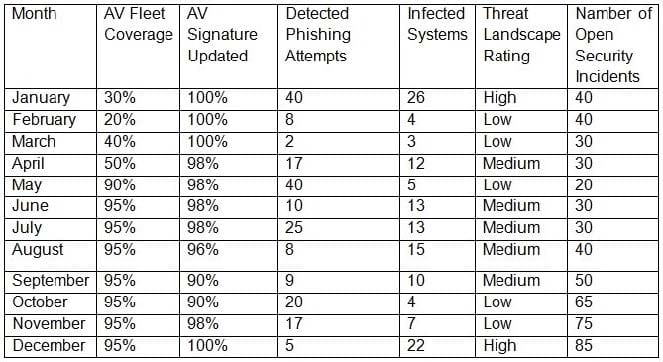
Which of the following BEST describes what could be interpreted from the above data?
A. 1. AV coverage across the fleet improved
2.
There is no correlation between infected systems and AV coverage.
3.
There is no correlation between detected phishing attempts and infected systems
4.
A correlation between threat landscape rating and infected systems appears to exist.
5.
Effectiveness and performance of the security team appears to be degrading.
B. 1. AV signature coverage has remained consistently high
2.
AV coverage across the fleet improved
3.
A correlation between phishing attempts and infected systems appears to exist
4.
There is a correlation between the threat landscape rating and the security team's performance.
5.
There is no correlation between detected phishing attempts and infected systems
C. 1. There is no correlation between infected systems and AV coverage
2.
AV coverage across the fleet improved
3.
A correlation between phishing attempts and infected systems appears to exist
4.
There is no correlation between the threat landscape rating and the security team's performance.
5.
There is a correlation between detected phishing attempts and infected systems
D. 1. AV coverage across the fleet declined
2.
There is no correlation between infected systems and AV coverage.
3.
A correlation between phishing attempts and infected systems appears to exist
4.
There is no correlation between the threat landscape rating and the security team's performance
5.
Effectiveness and performance of the security team appears to be degrading.
-
Question 625:
A Chief Information Security Officer (CISO is reviewing and revising system configuration and hardening guides that were developed internally and have been used several years to secure the organization's systems.
The CISO knows improvements can be made to the guides.
Which of the following would be the BEST source of reference during the revision process?
A. CVE database
B. Internal security assessment reports
C. Industry-accepted standards
D. External vulnerability scan reports
E. Vendor-specific implementation guides
-
Question 626:
A security engineer is working with a software development team. The engineer is tasked with ensuring all security requirements are adhered to by the developers. Which of the following BEST describes the contents of the supporting
document the engineer is creating?
A. A series of ad-hoc tests that each verify security control functionality of the entire system at once.
B. A series of discrete tasks that, when viewed in total, can be used to verify and document each individual constraint from the SRTM.
C. A set of formal methods that apply to one or more of the programing languages used on the development project.
D. A methodology to verify each security control in each unit of developed code prior to committing the code.
-
Question 627:
A technician is validating compliance with organizational policies. The user and machine accounts in the AD are not set to expire, which is non-compliant. Which of the following network tools would provide this type of information?
A. SIEM server
B. IDS appliance
C. SCAP scanner
D. HTTP interceptor
-
Question 628:
A security analyst is classifying data based on input from data owners and other stakeholders. The analyst has identified three data types:
Financially sensitive data Project data Sensitive project data
The analyst proposes that the data be protected in two major groups, with further access control separating the financially sensitive data from the sensitive project data. The normal project data will be stored in a separate, less secure location. Some stakeholders are concerned about the recommended approach and insist that commingling data from different sensitive projects would leave them vulnerable to industrial espionage.
Which of the following is the BEST course of action for the analyst to recommend?
A. Conduct a quantitative evaluation of the risks associated with commingling the data and reject or accept the concerns raised by the stakeholders.
B. Meet with the affected stakeholders and determine which security controls would be sufficient to address the newly raised risks.
C. Use qualitative methods to determine aggregate risk scores for each project and use the derived scores to more finely segregate the data.
D. Increase the number of available data storage devices to provide enough capacity for physical separation of non-sensitive project data.
-
Question 629:
A Chief Information Security Officer (CISO) is working with a consultant to perform a gap assessment prior to an upcoming audit. It is determined during the assessment that the organization lacks controls to effectively assess regulatory compliance by third-party service providers. Which of the following should be revised to address this gap?
A. Privacy policy
B. Work breakdown structure
C. Interconnection security agreement
D. Vendor management plan
E. Audit report
-
Question 630:
A project manager is working with system owners to develop maintenance windows for system pathing and upgrades in a cloud-based PaaS environment. Management has indicated one maintenance windows will be authorized per month, but clients have stated they require quarterly maintenance windows to meet their obligations. Which of the following documents should the project manager review?
A. MOU
B. SOW
C. SRTM
D. SLA
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.