Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 531:
A technician receives the following security alert from the firewall's automated system:
Match_Time: 10/10/16 16:20:43 Serial: 002301028176 Device_name: COMPSEC1 Type: CORRELATION Scrusex: domain\samjones Scr: 10.50.50.150 Object_name: beacon detection Object_id: 6005 Category: compromised-host Severity: medium Evidence: host repeatedly visited a dynamic DNS domain (17 time) After reviewing the alert, which of the following is the BEST analysis?
A. the alert is a false positive because DNS is a normal network function.
B. this alert indicates a user was attempting to bypass security measures using dynamic DNS.
C. this alert was generated by the SIEM because the user attempted too many invalid login attempts.
D. this alert indicates an endpoint may be infected and is potentially contacting a suspect host.
-
Question 532:
A software development team has spent the last 18 months developing a new web-based front-end that will allow clients to check the status of their orders as they proceed through manufacturing. The marketing team schedules a launch party to present the new application to the client base in two weeks. Before the launch, the security team discovers numerous flaws that may introduce dangerous vulnerabilities, allowing direct access to a database used by manufacturing. The development team did not plan to remediate these vulnerabilities during development.
Which of the following SDLC best practices should the development team have followed?
A. Implementing regression testing
B. Completing user acceptance testing
C. Verifying system design documentation
D. Using a SRTM
-
Question 533:
A system owner has requested support from data owners to evaluate options for the disposal of equipment containing sensitive data. Regulatory requirements state the data must be rendered unrecoverable via logical means or physically destroyed. Which of the following factors is the regulation intended to address?
A. Sovereignty
B. E-waste
C. Remanence
D. Deduplication
-
Question 534:
Following a recent data breach, a company has hired a new Chief Information Security Officer (CISO). The CISO is very concerned about the response time to the previous breach and wishes to know how the security team expects to react to a future attack. Which of the following is the BEST method to achieve this goal while minimizing disruption?
A. Perform a black box assessment
B. Hire an external red team audit
C. Conduct a tabletop exercise.
D. Recreate the previous breach.
E. Conduct an external vulnerability assessment.
-
Question 535:
An organization is in the process of integrating its operational technology and information technology areas. As part of the integration, some of the cultural aspects it would like to see include more efficient use of resources during change windows, better protection of critical infrastructure, and the ability to respond to incidents. The following observations have been identified:
1.
The ICS supplier has specified that any software installed will result in lack of support.
2.
There is no documented trust boundary defined between the SCADA and corporate networks.
3.
Operational technology staff have to manage the SCADA equipment via the engineering workstation.
4.
There is a lack of understanding of what is within the SCADA network.
Which of the following capabilities would BEST improve the security position?
A. VNC, router, and HIPS
B. SIEM, VPN, and firewall
C. Proxy, VPN, and WAF
D. IDS, NAC, and log monitoring
-
Question 536:
A consulting firm was hired to conduct assessment for a company. During the first stage, a penetration tester used a tool that provided the following output:
TCP 80 open
TCP 443 open
TCP 1434 filtered
The penetration tester then used a different tool to make the following requests:
GET / script/login.php?token=45$MHT000MND876
GET / script/login.php?token=@#984DCSPQ%091DF
Which of the following tools did the penetration tester use?
A. Protocol analyzer
B. Port scanner
C. Fuzzer
D. Brute forcer
E. Log analyzer
F. HTTP interceptor
-
Question 537:
An advanced threat emulation engineer is conducting testing against a client's network. The engineer conducts the testing in as realistic a manner as possible. Consequently, the engineer has been gradually ramping up the volume of attacks over a long period of time. Which of the following combinations of techniques would the engineer MOST likely use in this testing? (Choose three.)
A. Black box testing
B. Gray box testing
C. Code review
D. Social engineering
E. Vulnerability assessment
F. Pivoting
G. Self-assessment
H. White teaming
I. External auditing
-
Question 538:
An organization has recently deployed an EDR solution across its laptops, desktops, and server infrastructure. The organization's server infrastructure is deployed in an IaaS environment. A database within the non-production environment has been misconfigured with a routable IP and is communicating with a command and control server.
Which of the following procedures should the security responder apply to the situation? (Choose two.)
A. Contain the server.
B. Initiate a legal hold.
C. Perform a risk assessment.
D. Determine the data handling standard.
E. Disclose the breach to customers.
F. Perform an IOC sweep to determine the impact.
-
Question 539:
A security consultant is improving the physical security of a sensitive site and takes pictures of the unbranded building to include in the report. Two weeks later, the security consultant misplaces the phone, which only has one hour of charge left on it. The person who finds the phone removes the MicroSD card in an attempt to discover the owner to return it. The person extracts the following data from the phone and EXIF data from some files: DCIM Images folder Audio books folder Torrentz
My TAX.xls Consultancy HR Manual.doc Camera: SM-G950F
Exposure time: 1/60s Location: 3500 Lacey Road USA Which of the following BEST describes the security problem?
A. MicroSD in not encrypted and also contains personal data.
B. MicroSD contains a mixture of personal and work data.
C. MicroSD in not encrypted and contains geotagging information.
D. MicroSD contains pirated software and is not encrypted.
-
Question 540:
A security engineer is assisting a developer with input validation, and they are studying the following code block:
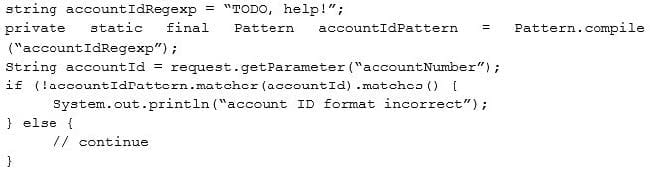
The security engineer wants to ensure strong input validation is in place for customer-provided account identifiers. These identifiers are ten-digit numbers. The developer wants to ensure input validation is fast because a large number of people use the system.
Which of the following would be the BEST advice for the security engineer to give to the developer?
A. Replace code with Java-based type checks
B. Parse input into an array
C. Use regular expressions
D. Canonicalize input into string objects before validation
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.