Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 441:
When reviewing KRIs of the email security appliance with the Chief Information Security Officer (CISO) of an insurance company, the security engineer notices the following:
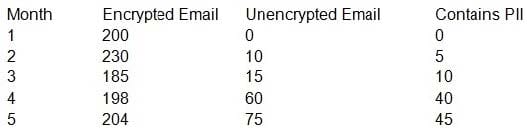
Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?
A. Quarantine emails sent to external domains containing PII and release after inspection.
B. Prevent PII from being sent to domains that allow users to sign up for free webmail.
C. Enable transport layer security on all outbound email communications and attachments.
D. Provide security awareness training regarding transmission of PII.
-
Question 442:
A company is transitioning to a new VDI environment, and a system engineer is responsible for developing a sustainable security strategy for the VDIs. Which of the following is the MOST appropriate order of steps to be taken?
A. Firmware update, OS patching, HIDS, antivirus, baseline, monitoring agent
B. OS patching, baseline, HIDS, antivirus, monitoring agent, firmware update
C. Firmware update, OS patching, HIDS, antivirus, monitoring agent, baseline
D. Baseline, antivirus, OS patching, monitoring agent, HIDS, firmware update
-
Question 443:
Due to a recent breach, the Chief Executive Officer (CEO) has requested the following activities be conducted during incident response planning:
Involve business owners and stakeholders Create an applicable scenario Conduct a biannual verbal review of the incident response plan Report on the lessons learned and gaps identified
Which of the following exercises has the CEO requested?
A. Parallel operations
B. Full transition
C. Internal review
D. Tabletop
E. Partial simulation
-
Question 444:
A security analyst has requested network engineers integrate sFlow into the SOC's overall monitoring picture. For this to be a useful addition to the monitoring capabilities, which of the following must be considered by the engineering team?
A. Effective deployment of network taps
B. Overall bandwidth available at Internet PoP
C. Optimal placement of log aggregators
D. Availability of application layer visualizers
-
Question 445:
An information security officer is responsible for one secure network and one office network. Recent intelligence suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials across networks. To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data:
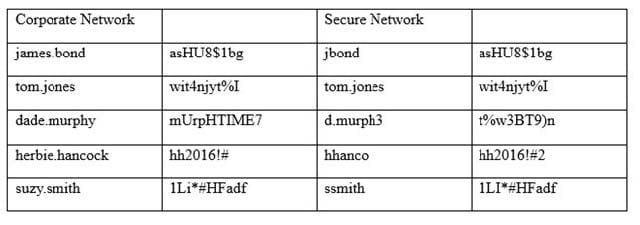
Which of the following tools was used to gather this information from the hashed values in the file?
A. Vulnerability scanner
B. Fuzzer
C. MD5 generator
D. Password cracker
E. Protocol analyzer
-
Question 446:
The Chief Information Officer (CISO) is concerned that certain systems administrators will privileged access may be reading other users' emails. Review of a tool's output shows the administrators have used web mail to log into other users' inboxes.
Which of the following tools would show this type of output?
A. Log analysis tool
B. Password cracker
C. Command-line tool
D. File integrity monitoring tool
-
Question 447:
As part of the development process for a new system, the organization plans to perform requirements analysis and risk assessment. The new system will replace a legacy system, which the organization has used to perform data analytics. Which of the following is MOST likely to be part of the activities conducted by management during this phase of the project?
A. Static code analysis and peer review of all application code
B. Validation of expectations relating to system performance and security
C. Load testing the system to ensure response times is acceptable to stakeholders
D. Design reviews and user acceptance testing to ensure the system has been deployed properly
E. Regression testing to evaluate interoperability with the legacy system during the deployment
-
Question 448:
A security analyst who is concerned about sensitive data exfiltration reviews the following:

Which of the following tools would allow the analyst to confirm if data exfiltration is occuring?
A. Port scanner
B. SCAP tool
C. File integrity monitor
D. Protocol analyzer
-
Question 449:
A Chief Security Officer (CSO) is reviewing the organization's incident response report from a recent incident. The details of the event indicate:
1.
A user received a phishing email that appeared to be a report from the organization's CRM tool.
2.
The user attempted to access the CRM tool via a fraudulent web page but was unable to access the tool.
3.
The user, unaware of the compromised account, did not report the incident and continued to use the CRM tool with the original credentials.
4.
Several weeks later, the user reported anomalous activity within the CRM tool.
5.
Following an investigation, it was determined the account was compromised and an attacker in another country has gained access to the CRM tool.
6.
Following identification of corrupted data and successful recovery from the incident, a lessons learned activity was to be led by the CSO.
Which of the following would MOST likely have allowed the user to more quickly identify the unauthorized use of credentials by the attacker?
A. Security awareness training
B. Last login verification
C. Log correlation
D. Time-of-check controls
E. Time-of-use controls
F. WAYF-based authentication
-
Question 450:
Two competing companies experienced similar attacks on their networks from various threat actors. To improve response times, the companies wish to share some threat intelligence about the sources and methods of attack.
Which of the following business documents would be BEST to document this engagement?
A. Business partnership agreement
B. Memorandum of understanding
C. Service-level agreement
D. Interconnection security agreement
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.