Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 381:
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.
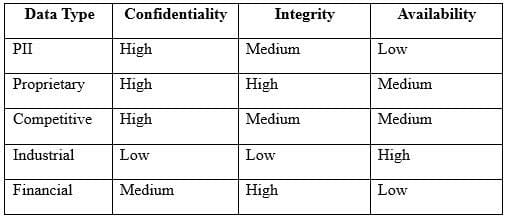
Based on the data classification table above, which of the following BEST describes the overall classification?
A. High confidentiality, high availability
B. High confidentiality, medium availability
C. Low availability, low confidentiality
D. High integrity, low availability
-
Question 382:
A company has decided to replace all the T-1 uplinks at each regional office and move away from using the existing MPLS network. All regional sites will use high-speed connections and VPNs to connect back to the main campus. Which of the following devices would MOST likely be added at each location?
A. SIEM
B. IDS/IPS
C. Proxy server
D. Firewall
E. Router
-
Question 383:
A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot.
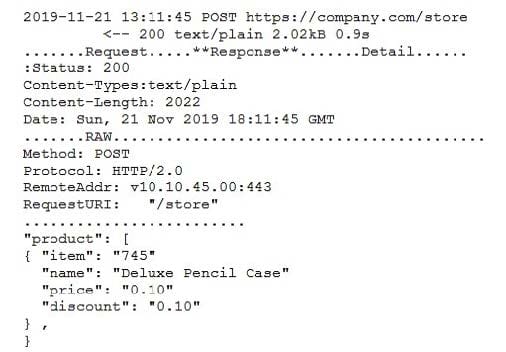
Which of the following tools was MOST likely used to exploit the application?
A. The engineer captured the data with a protocol analyzer, and then utilized Python to edit the data
B. The engineer queried the server and edited the data using an HTTP proxy interceptor
C. The engineer used a cross-site script sent via curl to edit the data
D. The engineer captured the HTTP headers, and then replaced the JSON data with a banner-grabbing tool
-
Question 384:
An organization is attempting to harden its web servers and reduce the information that might be disclosed by potential attackers. A security anal... reviewing vulnerability scan result from a recent web server scan. Portions of the scan results are shown below: Finding# 5144322 First time detected 10 nov 2015 09:00 GMT_0600 Last time detected 10 nov 2015 09:00 GMT_0600 CVSS base: 5 Access path: http://myorg.com/mailinglist.htm Request: GET http://mailinglist.aspx?content=volunteer Response: C:\Docments\MarySmith\malinglist.pdf Which of the following lines indicates information disclosure about the host that needs to be remediated?
A. Response: C:\Docments\marysmith\malinglist.pdf
B. Finding#5144322
C. First Time detected 10 nov 2015 09:00 GMT_0600
D. Access path: http//myorg.com/mailinglist.htm
E. Request: GET http://myorg.come/mailinglist.aspx?content=volunteer
-
Question 385:
In the past, the risk committee at Company A has shown an aversion to even minimal amounts of risk acceptance. A security engineer is preparing recommendations regarding the risk of a proposed introducing legacy ICS equipment. The project will introduce a minor vulnerability into the enterprise. This vulnerability does not significantly expose the enterprise to risk and would be expensive against.
Which of the following strategies should the engineer recommended be approved FIRST?
A. Avoid
B. Mitigate
C. Transfer
D. Accept
-
Question 386:
A security administrator is advocating for enforcement of a new policy that would require employers with privileged access accounts to undergo periodic inspections and review of certain job performance data. To which of the following policies is the security administrator MOST likely referring?
A. Background investigation
B. Mandatory vacation
C. Least privilege
D. Separation of duties
-
Question 387:
An SQL database is no longer accessible online due to a recent security breach. An investigation reveals that unauthorized access to the database was possible due to an SQL injection vulnerability. To prevent this type of breach in the future, which of the following security controls should be put in place before bringing the database back online? (Choose two.)
A. Secure storage policies
B. Browser security updates
C. Input validation
D. Web application firewall
E. Secure coding standards
F. Database activity monitoring
G.
-
Question 388:
An organization enables BYOD but wants to allow users to access the corporate email, calendar, and contacts from their devices. The data associated with the user's accounts is sensitive, and therefore, the organization wants to comply with the following requirements:
Active full-device encryption Enabled remote-device wipe Blocking unsigned applications Containerization of email, calendar, and contacts
Which of the following technical controls would BEST protect the data from attack or loss and meet the above requirements?
A. Require frequent password changes and disable NFC.
B. Enforce device encryption and activate MAM.
C. Install a mobile antivirus application.
D. Configure and monitor devices with an MDM.
-
Question 389:
A Chief Information Security Officer (CISO) is reviewing technical documentation from various regional offices and notices some key differences between these groups. The CISO has not discovered any governance documentation. The CISO creates the following chart to visualize the differences among the networking used:
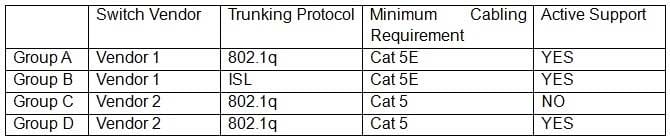
Which of the following would be the CISO's MOST immediate concern?
A. There are open standards in use on the network.
B. Network engineers have ignored defacto standards.
C. Network engineers are not following SOPs.
D. The network has competing standards in use.
-
Question 390:
An organization has employed the services of an auditing firm to perform a gap assessment in preparation for an upcoming audit. As part of the gap assessment, the auditor supporting the assessment recommends the organization engage with other industry partners to share information about emerging attacks to organizations in the industry in which the organization functions.
Which of the following types of information could be drawn from such participation?
A. Threat modeling
B. Risk assessment
C. Vulnerability data
D. Threat intelligence
E. Risk metrics
F. Exploit frameworks
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.