Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 351:
Given the following:
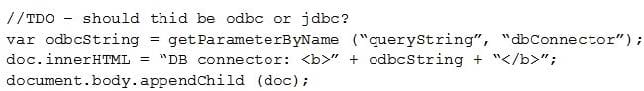
Which of the following vulnerabilities is present in the above code snippet?
A. Disclosure of database credential
B. SQL-based string concatenation
C. DOM-based injection
D. Information disclosure in comments
-
Question 352:
An organization is preparing to develop a business continuity plan. The organization is required to meet regulatory requirements relating to confidentiality and availability, which are well-defined. Management has expressed concern following initial meetings that the organization is not fully aware of the requirements associated with the regulations.
Which of the following would be MOST appropriate for the project manager to solicit additional resources for during this phase of the project?
A. After-action reports
B. Gap assessment
C. Security requirements traceability matrix
D. Business impact assessment
E. Risk analysis
-
Question 353:
A recent overview of the network's security and storage applications reveals a large amount of data that needs to be isolated for security reasons. Below are the critical applications and devices configured on the network:
1.
Firewall
2.
Core switches
3.
RM server
4.
Virtual environment
5.
NAC solution
The security manager also wants data from all critical applications to be aggregated to correlate events from multiple sources. Which of the following must be configured in certain applications to help ensure data aggregation and data isolation are implemented on the critical applications and devices? (Select TWO).
A. Routing tables
B. Log forwarding
C. Data remanants
D. Port aggregation
E. NIC teaming
F. Zones
-
Question 354:
A security researcher is gathering information about a recent spoke in the number of targeted attacks against multinational banks. The spike is on top of already sustained attacks against the banks. Some of the previous attacks have resulted in the loss of sensitive data, but as of yet the attackers have not successfully stolen any funds.
Based on the information available to the researcher, which of the following is the MOST likely threat profile?
A. Nation-state-sponsored attackers conducting espionage for strategic gain.
B. Insiders seeking to gain access to funds for illicit purposes.
C. Opportunists seeking notoriety and fame for personal gain.
D. Hacktivists seeking to make a political statement because of socio-economic factors.
-
Question 355:
A company is developing requirements for a customized OS build that will be used in an embedded environment. The company procured hardware that is capable of reducing the likelihood of successful buffer overruns while executables are processing. Which of the following capabilities must be included for the OS to take advantage of this critical hardware-based countermeasure?
A. Application whitelisting
B. NX/XN bit
C. ASLR
D. TrustZone
E. SCP
-
Question 356:
A company is migrating systems from an on-premises facility to a third-party managed datacenter. For continuity of operations and business agility, remote access to all hardware platforms must be available at all times. Access controls need to be very robust and provide an audit trail. Which of the following security controls will meet the company's objectives? (Select two.)
A. Integrated platform management interfaces are configured to allow access only via SSH
B. Access to hardware platforms is restricted to the systems administrator's IP address
C. Access is captured in event logs that include source address, time stamp, and outcome
D. The IP addresses of server management interfaces are located within the company's extranet
E. Access is limited to interactive logins on the VDi
F. Application logs are hashed cryptographically and sent to the SIEM
-
Question 357:
A financial consulting firm recently recovered from some damaging incidents that were associated with malware installed via rootkit. Post-incident analysis is ongoing, and the incident responders and systems administrators are working to determine a strategy to reduce the risk of recurrence. The firm's systems are running modern operating systems and feature UEFI and TPMs. Which of the following technical options would provide the MOST preventive value?
A. Update and deploy GPOs
B. Configure and use measured boot
C. Strengthen the password complexity requirements
D. Update the antivirus software and definitions
-
Question 358:
A government contractor was the victim of a malicious attack that resulted in the theft of sensitive information. An analyst's subsequent investigation of sensitive systems led to the following discoveries:
There was no indication of the data owner's or user's accounts being compromised.
No database activity outside of previous baselines was discovered.
All workstations and servers were fully patched for all known vulnerabilities at the time of the attack.
It was likely not an insider threat, as all employees passed polygraph tests.
Given this scenario, which of the following is the MOST likely attack that occurred?
A. The attacker harvested the hashed credentials of an account within the database administrators group after dumping the memory of a compromised machine. With these credentials, the attacker was able to access the database containing sensitive information directly.
B. An account, which belongs to an administrator of virtualization infrastructure, was compromised with a successful phishing attack. The attacker used these credentials to access the virtual machine manager and made a copy of the target virtual machine image. The attacker later accessed the image offline to obtain sensitive information.
C. A shared workstation was physically accessible in a common area of the contractor's office space and was compromised by an attacker using a USB exploit, which resulted in gaining a local administrator account. Using the local administrator credentials, the attacker was able to move laterally to the server hosting the database with sensitive information.
D. After successfully using a watering hole attack to deliver an exploit to a machine, which belongs to an employee of the contractor, an attacker gained access to a corporate laptop. With this access, the attacker then established a remote session over a VPN connection with the server hosting the database of sensitive information.
-
Question 359:
A forensics analyst suspects that a breach has occurred. Security logs show the company's OS patch system may be compromised, and it is serving patches that contain a zero-day exploit and backdoor. The analyst extracts an executable file from a packet capture of communication between a client computer and the patch server.
Which of the following should the analyst use to confirm this suspicion?
A. File size
B. Digital signature
C. Checksums
D. Anti-malware software
E. Sandboxing
-
Question 360:
A company wants to perform analysis of a tool that is suspected to contain a malicious payload. A forensic analyst is given the following snippet:
^32^[34fda19(fd^43gfd/home/user/lib/module.so.343jk^rfw(342fds43g
Which of the following did the analyst use to determine the location of the malicious payload?
A. Code deduplicators
B. Binary reverse-engineering
C. Fuzz testing
D. Security containers
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.