Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 311:
A request has been approved for a vendor to access a new internal server using only HTTPS and SSH to manage the back-end system for the portal. Internal users just need HTTP and HTTPS access to all internal web servers. All other external access to the new server and its subnet is not allowed. The security manager must ensure proper access is configured.
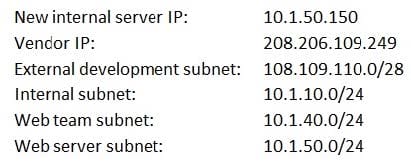
Below is a snippet from the firewall related to that server (access is provided in a top-down model):

Which of the following lines should be configured to allow the proper access? (Choose two.)
A. Move line 3 below line 4 and change port 80 to 443 on line 4.
B. Move line 3 below line 4 and add port 443 to line.
C. Move line 4 below line 5 and add port 80 to 8080 on line 2.
D. Add port 22 to line 2.
E. Add port 22 to line 5.
F. Add port 443 to line 2.
G. Add port 443 to line 5.
-
Question 312:
An incident responder wants to capture volatile memory comprehensively from a running machine for forensic purposes. The machine is running a very recent release of the Linux OS. Which of the following technical approaches would be the MOST feasible way to accomplish this capture?
A. Run the memdump utility with the -k flag.
B. Use a loadable kernel module capture utility, such as LiME.
C. Run dd on/dev/mem.
D. Employ a stand-alone utility, such as FTK Imager.
-
Question 313:
A penetration testing manager is contributing to an RFP for the purchase of a new platform. The manager has provided the following requirements:
1.
Must be able to MITM web-based protocols
2.
Must be able to find common misconfigurations and security holes
Which of the following types of testing should be included in the testing platform? (Choose two.)
A. Reverse engineering tool
B. HTTP intercepting proxy
C. Vulnerability scanner
D. File integrity monitor
E. Password cracker
F. Fuzzer
-
Question 314:
A new database application was added to a company's hosted VM environment. Firewall ACLs were modified to allow database users to access the server remotely. The company's cloud security broker then identified abnormal from a database user on-site. Upon further investigation, the security team noticed the user ran code on a VM that provided access to the hypervisor directly and access to other sensitive data.
Which of the following should the security do to help mitigate future attacks within the VM environment? (Choose two.)
A. Install the appropriate patches.
B. Install perimeter NGFW.
C. Configure VM isolation.
D. Deprovision database VM.
E. Change the user's access privileges.
F. Update virus definitions on all endpoints.
-
Question 315:
Ann, a security administrator, is conducting an assessment on a new firewall, which was placed at the perimeter of a network containing PII. Ann runs the following commands on a server (10.0.1.19) behind the firewall:

From her own workstation (192.168.2.45) outside the firewall, Ann then runs a port scan against the server and records the following packet capture of the port scan:
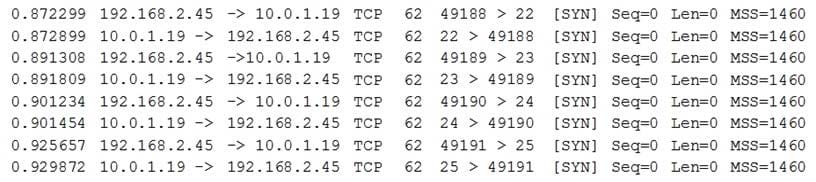
Connectivity to the server from outside the firewall worked as expected prior to executing these commands.
Which of the following can be said about the new firewall?
A. It is correctly dropping all packets destined for the server.
B. It is not blocking or filtering any traffic to the server.
C. Iptables needs to be restarted.
D. The IDS functionality of the firewall is currently disabled.
-
Question 316:
A laptop is recovered a few days after it was stolen.
Which of the following should be verified during incident response activities to determine the possible impact of the incident?
A. Full disk encryption status
B. TPM PCR values
C. File system integrity
D. Presence of UEFI vulnerabilities
-
Question 317:
A project manager is working with a software development group to collect and evaluate user scenarios related to the organization's internally designed data analytics tool. While reviewing stakeholder input, the project manager would like to formally document the needs of the various stakeholders and the associated organizational compliance objectives supported by the project.
Which of the following would be MOST appropriate to use?
A. Roles matrix
B. Peer review
C. BIA
D. SRTM
-
Question 318:
A school contracts with a vendor to devise a solution that will enable the school library to lend out tablet computers to students while on site. The tablets must adhere to string security and privacy practices. The school's key requirements are to:
1.
Maintain privacy of students in case of loss
2.
Have a theft detection control in place
3.
Be compliant with defined disability requirements
4.
Have a four-hour minimum battery life
Which of the following should be configured to BEST meet the requirements? (Choose two.)
A. Remote wiping
B. Geofencing
C. Antivirus software
D. TPM
E. FDE
F. Tokenization
-
Question 319:
Following a recent outage, a systems administrator is conducting a study to determine a suitable bench stock on server hard drives.
Which of the following metrics is MOST valuable to the administrator in determining how many hard drives to keep-on hand?
A. TTR
B. ALE
C. MTBF
D. SLE
E. RPO
-
Question 320:
An organization's network security administrator has been using an SSH connection to manage switches and routers for several years. After attempting to connect to a router, an alert appears on the terminal emulation software, warning that the SSH key has changed.
After confirming the administrator is using the typical workstation and the router has not been replaced, which of the following are the MOST likely explanations for the warning message? (Choose two.).
A. The SSH keys were given to another department.
B. A MITM attack is being performed by an APT.
C. The terminal emulator does not support SHA-256.
D. An incorrect username or password was entered.
E. A key rotation has occurred as a result of an incident.
F. The workstation is not syncing with the correct NTP server.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.