Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 271:
A technician is reviewing the following log:
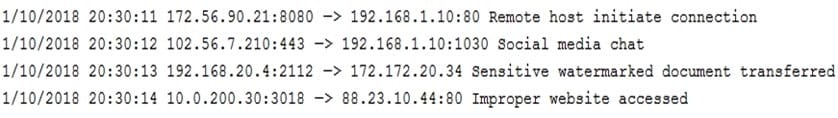
Which of the following tools should the organization implement to reduce the highest risk identified in this log?
A. NIPS
B. DLP
C. NGFW
D. SIEM
-
Question 272:
A penetration tester is trying to gain access to a remote system. The tester is able to see the secure login page and knows one user account and email address, but has not yet discovered a password.
Which of the following would be the EASIEST method of obtaining a password for the known account?
A. Man-in-the-middle
B. Reverse engineering
C. Social engineering
D. Hash cracking
-
Question 273:
A company is moving all of its web applications to an SSO configuration using SAML. Some employees report that when signing in to an application, they get an error message on the login screen after entering their username and password, and are denied access. When they access another system that has been converted to the new SSO authentication model, they are able to authenticate successfully without being prompted for login.
Which of the following is MOST likely the issue?
A. The employees are using an old link that does not use the new SAML authentication.
B. The XACML for the problematic application is not in the proper format or may be using an older schema.
C. The web services methods and properties are missing the required WSDL to complete the request after displaying the login page.
D. A threat actor is implementing an MITM attack to harvest credentials.
-
Question 274:
A security analyst for a bank received an anonymous tip on the external banking website showing the following:
Protocols supported
-TLS 1.0
-
SSL 3
-
SSL 2 Cipher suites supported
-TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA-ECDH p256r1
-TLS_DHE_RSA_WITH_AES_256_CBC_SHA-DH 1024bit
-TLS_RSA_WITH_RC4_128_SHA TLS_FALLBACK_SCSV non supported POODLE Weak PFS OCSP stapling supported
Which of the following should the analyst use to reproduce these findings comprehensively?
A. Query the OCSP responder and review revocation information for the user certificates.
B. Review CA-supported ciphers and inspect the connection through an HTTP proxy.
C. Perform a POODLE (SSLv3) attack using an exploitations framework and inspect the output.
D. Inspect the server certificate and simulate SSL/TLS handshakes for enumeration.
-
Question 275:
Ann, a retiring employee, cleaned out her desk. The next day, Ann's manager notices company equipment that was supposed to remain at her desk is now missing.
Which of the following would reduce the risk of this occurring in the future?
A. Regular auditing of the clean desk policy
B. Employee awareness and training policies
C. Proper employee separation procedures
D. Implementation of an acceptable use policy
-
Question 276:
A regional transportation and logistics company recently hired its first Chief Information Security Officer (CISO). The CISO's first project after onboarding involved performing a vulnerability assessment against the company's public facing network. The completed scan found a legacy collaboration platform application with a critically rated vulnerability. While discussing this issue with the line of business, the CISO learns the vulnerable application cannot be updated without the company incurring significant losses due to downtime or new software purchases.
Which of the following BEST addresses these concerns?
A. The company should plan future maintenance windows such legacy application can be updated as needed.
B. The CISO must accept the risk of the legacy application, as the cost of replacing the application greatly exceeds the risk to the company.
C. The company should implement a WAF in front of the vulnerable application to filter out any traffic attempting to exploit the vulnerability.
D. The company should build a parallel system and perform a cutover from the old application to the new application, with less downtime than an upgrade.
-
Question 277:
An enterprise's Chief Technology Officer (CTO) and Chief Information Security Officer (CISO) are meeting to discuss ongoing capacity and resource planning issues. The enterprise has experienced rapid, massive growth over the last 12 months, and the technology department is stretched thin for resources. A new accounting service is required to support the enterprise's growth, but the only available compute resources that meet the accounting service requirements are on the virtual platform, which is hosting the enterprise's website.
Which of the following should the CISO be MOST concerned about?
A. Poor capacity planning could cause an oversubscribed host, leading to poor performance on the company's website.
B. A security vulnerability that is exploited on the website could expose the accounting service.
C. Transferring as many services as possible to a CSP could free up resources.
D. The CTO does not have the budget available to purchase required resources and manage growth.
-
Question 278:
When implementing a penetration testing program, the Chief Information Security Officer (CISO) designates different organizational groups within the organization as having different responsibilities, attack vectors, and rules of engagement. First, the CISO designates a team to operate from within the corporate environment. This team is commonly referred to as:
A. the blue team.
B. the white team.
C. the operations team.
D. the read team.
E. the development team.
-
Question 279:
A security engineer is working to secure an organization's VMs. While reviewing the workflow for creating VMs on demand, the engineer raises a concern about the integrity of the secure boot process of the VM guest.
Which of the following would BEST address this concern?
A. Configure file integrity monitoring of the guest OS.
B. Enable the vTPM on a Type 2 hypervisor.
C. Only deploy servers that are based on a hardened image.
D. Protect the memory allocation of a Type 1 hypervisor.
-
Question 280:
A vendor develops a mobile application for global customers. The mobile application supports advanced encryption of data between the source (the mobile device) and the destination (the organization's ERP system).
As part of the vendor's compliance program, which of the following would be important to take into account?
A. Mobile tokenization
B. Export controls
C. Device containerization
D. Privacy policies
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.