Exam Details
Exam Code
:C2150-612Exam Name
:IBM Security QRadar SIEM V7.2.6 Associate AnalystCertification
:IBM CertificationsVendor
:IBMTotal Questions
:105 Q&AsLast Updated
:Jul 08, 2025
IBM IBM Certifications C2150-612 Questions & Answers
-
Question 71:
What is a primary goal with the use of building blocks?
A. A method to create reusable rule responses
B. A reusable test stack that can be used in other rules
C. A method to generate reference set updates without using a rule
D. A method to create new events back into the pipeline without using a rule
-
Question 72:
Which two are top level options when right clicking on an IP Address within the Offense Summary page? (Choose two.)
A. WHOIS
B. Navigate
C. DNS Lookup
D. Information
E. Asset Summary Page
-
Question 73:
What is an example of the use of a flow data that provides more information than an event data?
A. Represents a single event on the network
B. Automatically identifies and better classifies new assets found on a network
C. Performs near real-time comparisons of application data with logs sent from security devices
D. Represents network activity by normalizing IP addresses ports, byte and packet counts, as well as other details
-
Question 74:
Given these default options for dashboards on the QRadar Dashboard Tab: Which will display a list of offenses?
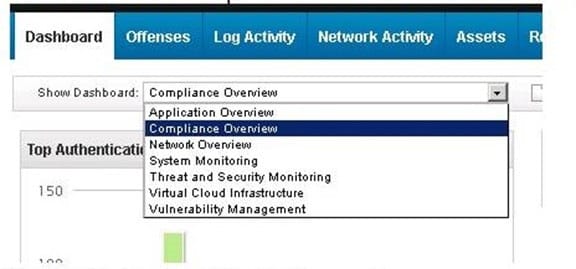
A. Network Overview
B. System Monitoring
C. Vulnerability Management
D. Threat and Security Monitoring
-
Question 75:
What is a common purpose for looking at flow data?
A. To see which users logged into a remote system
B. To see which users were accessing report data in QRadar
C. To see application versions installed on a network endpoint
D. To see how much information was sent from a desktop to a remote website
-
Question 76:
Which saved searches can be included on the Dashboard?
A. Event and Flow saved searches
B. Asset and Network saved searches
C. User and Vulnerability saved searches
D. Network Activity and Risk saved searches
-
Question 77:
What is the key difference between Rules and Building Blocks in QRadar?
A. Rules have Actions and Responses; Building Blocks do not.
B. The Response Limiter is available on Building Blocks but not on Rules.
C. Building Blocks are built-in to the product; Rules are customized for each deployment.
D. Building Blocks are Rules which are evaluated on both Flows and Events; Rules are evaluated on Offenses of Flows or Events.
-
Question 78:
Which Anomaly Detection Rule type can test events or flows for volume changes that occur in regular patterns to detect outliers?
A. Outlier Rule
B. Anomaly Rule
C. Threshold Rule
D. Behavioral Rule
-
Question 79:
What are the various timestamps related to a flow?
A. First Packet Time, Storage Time, Log Source Time
B. First Packet Time, Storage Time, Last Packet Time
C. First Packet Time, Log Source Time, Last Packet Time
D. First Packet Time, Storage Time, Log Source Time, End Time
-
Question 80:
Which QRadar add-on component can generate a list of the unencrypted protocols that can communicate from a DMZ to an internal network?
A. QRadar Risk Manager
B. QRadar Flow Collector
C. QRadar Incident Forensics
D. QRadar Vulnerability Manager
Related Exams:
C1000-002
IBM MQ V9.0 System AdministrationC1000-003
IBM Mobile Foundation v8.0 Application DevelopmentC1000-004
IBM Curam SPM V7.X Application DeveloperC1000-007
IBM Cloud Application Development v3C1000-010
IBM Operational Decision Manager Standard V8.9.1 Application DevelopmentC1000-012
IBM Watson Application Developer V3.1C1000-015
IBM Business Process Manager V8.6 Application Development using Process DesignerC1000-018
IBM QRadar SIEM V7.3.2 Fundamental AnalysisC1000-019
IBM Spectrum Protect Plus V10.1.1 ImplementationC1000-020
IBM New Workloads Sales V2
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only IBM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your C2150-612 exam preparations and IBM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.