Exam Details
Exam Code
:C2150-612Exam Name
:IBM Security QRadar SIEM V7.2.6 Associate AnalystCertification
:IBM CertificationsVendor
:IBMTotal Questions
:105 Q&AsLast Updated
:Jul 08, 2025
IBM IBM Certifications C2150-612 Questions & Answers
-
Question 21:
What is a key difference between the magnitude of an event and the magnitude of an offense?
A. The magnitude of an event is derived when the event is received and does not vary, the magnitude of an offense can only increase.
B. The magnitude of an event is derived when the event is received and does not vary, the magnitude of an offense can increase or decrease over time.
C. The magnitude of an event is derived from the current magnitude of the offense it creates, the magnitude of an offense can increase or decrease over time.
D. The magnitude of an event is derived when the event is received and does not vary, the magnitude of an offense is derived when the offense is created and does not vary.
-
Question 22:
What is one of the major differences between event and network data (flow)?
A. Flows can replay a whole packet by packet sessions, while events are just a snapshot.
B. A flow can have a life span that can last seconds, minutes, hours or days, while events are only a snapshot.
C. An event can have a life span that can last seconds, minutes, hours or days, while flows can only span 1 minute.
D. Events represent network activity by normalizing IP addresses, ports, byte and packet counts, while flows do not.
-
Question 23:
What are two default Report Groups? (Choose two.)
A. Analyst
B. Executive
C. Administration
D. Log Management
E. Network Management
-
Question 24:
Which column shows information as icons on the Reports tab?
A. Owner
B. Formats
C. Schedule
D. Report Name
-
Question 25:
A Security Analyst is looking on the Assets Tab at an asset with offenses associated to it.
With a "Right Click" on the IP address, where could the Security Analyst go to obtain all offenses associated with it?
A. Information > Asset Profile
B. Navigate > View by Network
C. Run Vulnerability Scan > Source offenses
D. Navigate > View Source Summary or Destination Summary
-
Question 26:
What does the Network Hierarchy provide relating to the "whole picture" that is helpful during an investigation?
A. It allows hosts that are marked to be known to have vulnerabilities to be seen quickly.
B. It allows for the isolation of traffic between the hosts in question for more in depth analysis.
C. It allows for the removal of infected hosts from the network before being added back into the network.
D. It allows for the identification of known hosts on the network versus those that aren't members of the network.
-
Question 27:
Which QRadar component stores and forwards events from local and remote log sources?
A. QRadar Data Node
B. QRadar Event Collector
C. QRadar Event Processor
D. QRadar Distributes Console
-
Question 28:
Given the following window:
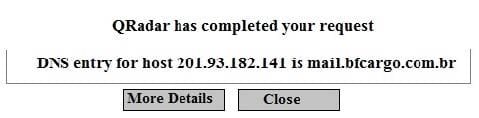
What are the steps to get this window within an offense?
A. Right click on the IP > Information > DNS Lookup
B. Right click on the IP > Information > Reverse DNS
C. Right click on the IP > Information > WHOIS Lookup
D. Right click on the IP > Information > Asset Profile
-
Question 29:
What is the difference between an offense and a triggered rule?
A. Offenses are created every time a rule's tests are satisfied, but a rule may only trigger if the response limiter allows.
B. The first time a rule triggers, it will create an offense, after than to new offense will be created for the same index type.
C. A rule will always trigger if its tests are satisfied, but an offense may only be created if the event magnitude is greater than 6.
D. An offense may be created or updated by a triggered rule, but a rule will always trigger when the tests are satisfied.
-
Question 30:
A Security Analyst, looking at a Log Activity search result, wants to limit the results to one Log Source.
Which right-click method would be the fastest way for the Security Analyst to ensure this?
A. Right click on a Log Source name, then select Filter on Log Source is
B. Right click on a Source IP Address, then select Filter on Log Source is
C. Right click on the Log Source Type name, then select Filter on Log Source Group is
D. Right click on the Log Source Group name, then select Filter on Log Source Group is
Related Exams:
C1000-002
IBM MQ V9.0 System AdministrationC1000-003
IBM Mobile Foundation v8.0 Application DevelopmentC1000-004
IBM Curam SPM V7.X Application DeveloperC1000-007
IBM Cloud Application Development v3C1000-010
IBM Operational Decision Manager Standard V8.9.1 Application DevelopmentC1000-012
IBM Watson Application Developer V3.1C1000-015
IBM Business Process Manager V8.6 Application Development using Process DesignerC1000-018
IBM QRadar SIEM V7.3.2 Fundamental AnalysisC1000-019
IBM Spectrum Protect Plus V10.1.1 ImplementationC1000-020
IBM New Workloads Sales V2
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only IBM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your C2150-612 exam preparations and IBM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.