Exam Details
Exam Code
:JN0-102Exam Name
:Internet Associate, Junos(JNCIA-Junos)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:419 Q&AsLast Updated
:Jul 12, 2025
Juniper Juniper Certifications JN0-102 Questions & Answers
-
Question 171:
-- Exhibit -user@router> show configuration firewall
familyinet {
filter demo {
term example {
from {
source-address {
100.100.100.0/24;
}
destination-address {
200.200.200.0/24;
}
}
then {
reject;
}
}
term testing {
from {
source-address {
10.10.10.0/28;
}
destination-address {
200.200.200.0/24;
}
}
then sample;
}
term results {
from {
address {
200.200.200.0/24;
}
}
then accept;
}
term final {
then policer LAPD;
}
}
}
-- Exhibit -Given the configuration shown in the exhibit, what will happen to traffic from source 10.10.10.25 destined
to 200.200.200.1?
A. The traffic will be rejected.
B. The traffic will be dropped.
C. The traffic will be forwarded.
D. The traffic will be policed.
-
Question 172:
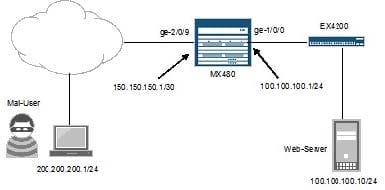
Referring to the exhibit, you are asked to rate-limit traffic from Web-Server to the subnet where Mal-User is located. All other traffic should be permitted.
Which firewall filter configuration do you use?
A. [edit firewall]user@router# showpolicer LIMIT-MAL-USER {if-exceeding {bandwidth-limit 400k;burstsize-limit 100k;}then discard;}familyinet {filter STOP-MAL-USER {term one {from {source-address {100.100.100.10/32;}destination-address {200.200.200.0/24;}}thenpolicer LIMIT-MAL-USER;}term two {then accept;}}}
B. [edit firewall]user@router# showpolicer LIMIT-BAD-USER {if-exceeding {bandwidth-limit 400k;burstsize-limit 100k;}then discard;}familyinet {filter STOP-MAL-USER {term one {from {source-address {100.100.100.10/32;}destination-address {200.200.200.0/24;}}thenpolicer LIMIT-MAL-USER;}term two {then accept;}}}
C. [edit firewall]user@router# showpolicer LIMIT-MAL-USER {if-exceeding {bandwidth-limit 400k;burstsize-limit 100k;}then discard;}familyinet {filter STOP-MAL-USER {term one {from {source-address {100.100.100.10/32;}destination-address {200.200.200.0/24;}}thenpolicer LIMIT-MAL-USER;}term two {then reject;}}}
D. [edit firewall]user@router# showpolicer LIMIT-MAL-USER {if-exceeding {bandwidth-limit 400k;burstsize-limit 100k;}then discard;}familyinet {filter STOP-MAL-USER {term one {from {source-address {200.200.200.0/24;}destination-address {100.100.100.10/32;}}thenpolicer LIMIT-MAL-USER;}term two {then accept;}}}
-
Question 173:
What are two valid actions for a routing policy? (Choose two.)
A. discard
B. next policy
C. accept
D. ignore
-
Question 174:
Which statement is true about routing tables on a Junos device?
A. They purge any routes not selected as active routes.
B. They exist in two places: the Routing Engine and the Packet Forwarding Engine.
C. They are exclusively designed to handle dynamic routing protocols.
D. They populate the forwarding table.
-
Question 175:
Two devices on an Ethernet segment sent frames at the same time causing a collision. Which two statements are true? (Choose two.)
A. Both devices stop transmitting, wait a random period of time, verify the wire is idle, and re-transmit.
B. The device with the lowest MAC address is permitted to retransmit first.
C. The device with the lowest MAC address sends a jam signal to notify all other devices of the collision.
D. Both devices send a jam signal to notify all other devices of the collision.
-
Question 176:
What represents the binary equivalence of 207?
A. 11001111
B. 11101011
C. 11010111
D. 11010101
-
Question 177:
You have been asked to create a static route with a next hop that is not directly connected to the router.
Which configuration parameter enables the static route to accomplish this scenario?
A. resolve
B. indirect
C. next-hop
D. recursive
-
Question 178:
Which command displays the amount of space available on the storage media?
A. show chassis routing-engine
B. show system file-storage
C. file list
D. show system storage
-
Question 179:
What is the role of route preference?
A. It is used as a tiebreaker when the same prefix is available through multiple protocols.
B. It is used to determine the preferred path to a given destination.
C. It is used to select the best route between multiple equal-cost paths.
D. It is used to select which routing table to use for forwarding.
-
Question 180:
-- Exhibit -[edit class-of-service]
user@router# show
interfaces {
ge-0/0/2 {
unit 0 {
classifiers {
inet-precedence default;
}
}
}
}
-- Exhibit -Referring to the exhibit, which type of classifier is being used in this CoS configuration?
A. behavior aggregate
B. policer
C. multifield
D. forwarding policy
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-1103
Design, Associate (JNCIA-Design)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-102 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.