Exam Details
Exam Code
:600-210Exam Name
:Implementing Cisco Service Provider Mobility UMTS NetworksCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:70 Q&AsLast Updated
:Jun 23, 2023
Cisco Cisco Certifications 600-210 Questions & Answers
-
Question 61:
Your company is adding additional subscriber IP network ranges and requires many-to-one NAT to be configured on the Cisco ASR 5000 for the subscriber IP network 10.11.23.0/24. The public IP range is 172.20.21.20 172.20.21.110, and each IP has no more than 100 subscribers. Which configuration option accomplishes this task?
A. active-charging service ACS_ACME access-ruledef apn_cisco ip src-address = 10.11.23.0/24 fw-and-nat policy base_1 access-rule priority 1 access-ruledef apn_cisco permit nat-realm nat_pool1 nat policy nat-required default-nat-realm nat_pool1 rulebase acme_rulebase fw-and-nat default-policy base_1 context cisco ip pool nat_pool1 range 172.20.21.20 172.20.21.110 napt-users-per-ip-address 100
B. active-charging service ACS_ACME access-ruledef apn_cisco ip src-address = 10.11.0.0/16 fw-and-nat policy base_1 access-rule priority 1 access-ruledef apn_cisco permit nat-realm nat_pool1 nat policy nat-required default-nat-realm nat_pool1 rulebase acme_rulebase fw-and-nat default-policy base_1 context cisco ip pool nat_pool1 range 172.20.21.20 172.20.21.110 napt-users-per-ip-address 1000
C. active-charging service ACS_ACME access-ruledef apn_cisco ip src-address = 10.11.23.0/24 nat-and-pat policy nat_1 access-rule priority 1 access-ruledef apn_cisco permit nat-realm nat_pool1 nat policy nat-required default-nat-realm nat_pool1 context cisco ip pool nat_pool1 range 172.20.21.20 172.20.21.29 napt-users-per-ip-address 100
D. active-charging service ACS_ACME access-ruledef apn_cisco ip src-address = 10.11.23.0/24 fw-and-nat policy base_1 access-rule priority 1 access-ruledef apn_cisco permit nat-realm nat_pool1 nat policy nat-required default-nat-realm nat_pool1 rulebase acme_rulebase fw-and-nat default-policy base_1 context cisco ip pool nat_pool1 range 172.20.21.20 172.20.21.29 napt-users-per-ip-address 100
-
Question 62:
Which option describes the ICAP protocol?
A. ICAP is a protocol designed to enable inter-device communications for different vendor systems to share information about subscribers in a common format. ICAP allows for subscriber session control for actions such as session disconnect and suspension.
B. ICAP is a protocol designed to enable subscribers to communicate in a peer-to-peer network for file sharing purposes and is often used to circumvent upstream content filtering.
C. ICAP is a communication access package consisting of a mixed platform of services such as web, FTP, and authentication. ICAP is used to minimize the deployment footprint and expedite new offerings for Internet service providers.
D. ICAP is a protocol designed to support dynamic content filtering, insertion, and modification of web pages. ICAP allows interaction with external content servers such as parental control (content filtering) servers to provide content filtering service support.
-
Question 63:
Your company has decided to implement URL blacklisting for the ACME company rulebase and discard any blacklisted matches found in subscriber HTTP traffic. Which configuration accomplishes this task?
A. active-charging service acme_acs url-blacklisting method exact-match rulebase acme_rulebase urlblacklisting action discard
B. active-charging service acme_acs url-blacklisting method exact-match rulebase acme_rulebase urlblacklisting action terminate-flow
C. active-charging service acme_acs url-blacklisting method http post url-blacklisting method http get rulebase acme_rulebase url-blacklisting action discard
D. active-charging service acme_acs url-blacklisting method http post url-blacklisting method http get rulebase acme_rulebase url-blacklisting action terminate-flow
-
Question 64:
Which description of a smurf attack is true?
A. A smurf attack is an attack in which small TCP packets are sent toward a server from thousands of subscribers, which causes the server network buffer to overflow and drop packets and results in a denial of service.
B. A smurf attack is an attack in which the attacker sends ICMP echo request packets using a spoofed source IP address destined to remote network broadcast addresses, which results in all recipients replying back to the spoofed source IP address in an attempt to cause a denial of service to the targeted spoofed IP address.
C. A smurf attack is an attack in which the attacker sends UDP echo packets using a spoofed source IP address destined to remote network broadcast addresses, which results in all recipients replying back to the spoofed source IP address in an attempt to cause a denial of service to the targeted spoofed IP address.
D. A smurf attack is an attack in which the attacker attempts to change the TCP MSS value to a small value for all TCP flows destined to the target device, which results in many small packets having to be processed by the target, which causes buffer overflows and denial of service.
-
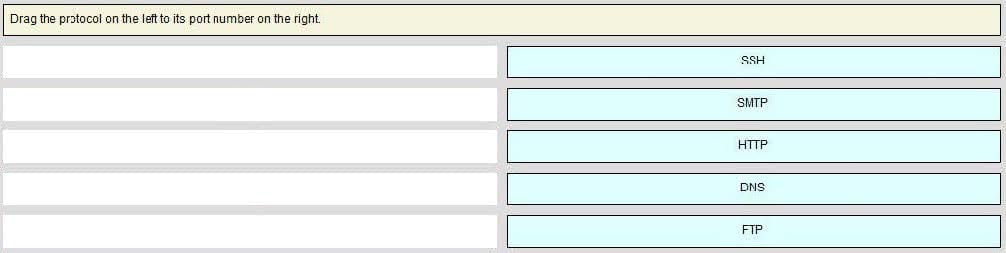
Question 65:

Select and Place:

-
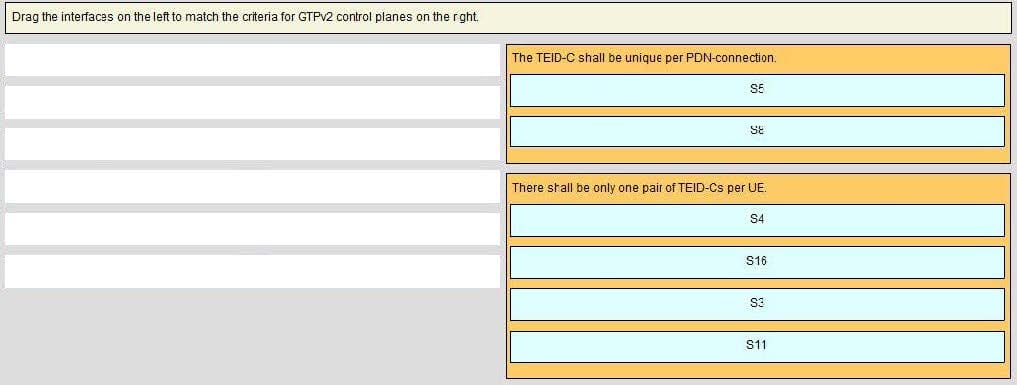
Question 66:
Select and Place:

-
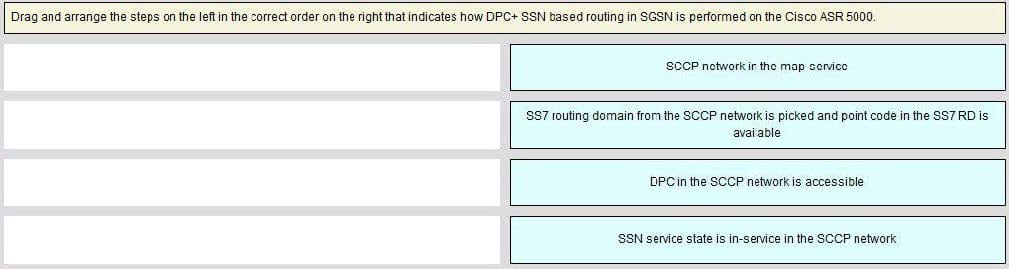
Question 67:
Select and Place:

-
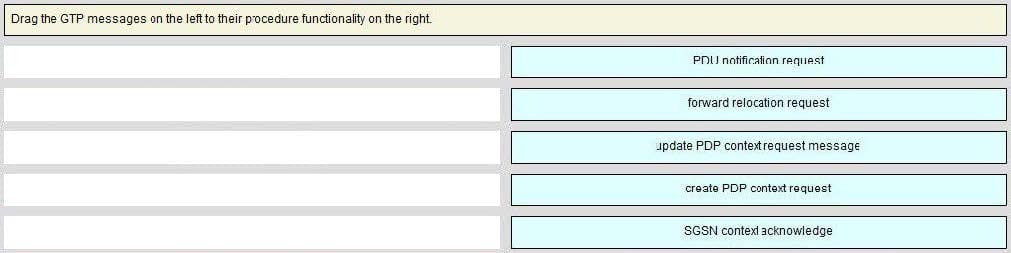
Question 68:
Select and Place:

-
Question 69:

Select and Place:

-
Question 70:
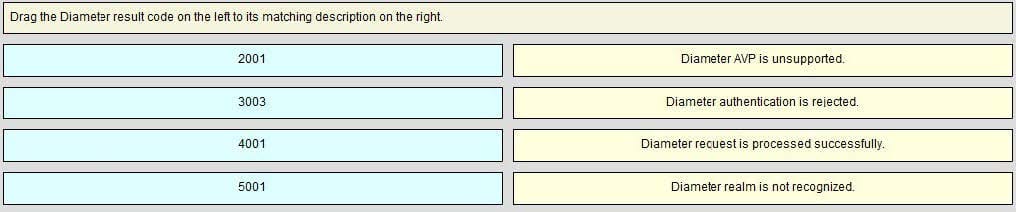
Select and Place:

Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 600-210 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.